
For most organizations, the entire impetus to encrypt is closely tied to the need to be compliant with one regulation or another. There is the PCI regulation, the HITECH act of 2009, HIPAA, Sarbanes-Oxley, and a whole host of state privacy laws. If you are going through the due diligence of database encryption, you sure as heck want to get it right the first time.
A big part of getting it right is using the right encryption tool. There are plenty of tools on the market that claim to do encryption, and you probably know a clever programmer or two who thinks he can come up with a nifty little data scrambling algorithm that no-one has ever seen before. But encryption — real encryption — demands that we reach for a higher standard.
The U.S. Department of Commerce publishes the definitive encryption standard on its National Institute of Standard and Technology (NIST) website and to date, hundreds of cryptographic providers have achieved this high standard. As of this writing, NIST has certified over 1,300 AES encryption implementations.
A Fundamental TruthCryptographers do not suffer fools lightly. Their science is mathematically based and their algorithms are well known and well vetted. A fundamental truth of cryptography is that real encryption cannot rely on keeping the algorithm secret. Instead the secret that protects the data is the encryption key, and only the encryption key. Anyone who says different may find themselves on the receiving end of an extra-long mathematical dissertation on the mathematical correctness of accepted encryption algorithms.

When you stop to think about it, this makes perfect sense. If the world used a secret algorithm to encrypt data, if that algorithm were ever to be discovered then all the world’s data would be at risk. But if the key is the one-and-only secret that unlocks the data, then a compromised key only puts the data at risk that was encrypted with that particular key. All the other data that has been encrypted with other keys is still safe. This demonstrates both the wisdom of strong (and open) algorithms, but also the essential importance of strong key protection.
Another benefit of open algorithms is that they are peer reviewed and extremely well vetted. The AES standard that is the de-facto standard for encrypting data at rest is well known in cryptography and mathematical circles and is recognized the world over as the most effective method for encrypting business data. Its modes of encryption are well known and proven. And there is a strong body of knowledge about how to correctly implement the AES standard. From the perspective of a cryptographic (encryption) provider, encryption libraries are not easy to write, but they are known to be solid when implemented according to accepted standards.
Homegrown EncryptionUnfortunately, some software providers seemed to have taken a different road. AES encryption must have seemed too difficult, or too cumbersome, so instead they found loopholes and/or shortcuts to simplify their implementation. Some software providers use untested software, or unique and un-vetted methods of encryption. These data scrambling methods aren’t (and never could be) NIST or FIPS certified, but if their customers never ask about certification or independent validation, those providers are not likely to raise the topic.
So we are seeing a raft of uncertified, and un-vetted cipher methods introduced in the market place. Some, like OMAC, CS, and CWC have languished on the NIST list of “Proposed Modes” for years, while others like CUSP have never even been submitted as a proposed standard. And while it is possible that one or more of these upstart modes could be better than one of the current, standard modes, there is no way to know this because these new modes have not been properly tested and crypto-analyzed. Without testing and peer review, each of these modes is just another premature idea that is statistically more likely to be a bad encryption method than a good one.
Show Me the Cert!
Many software vendors are beginning to recognize the value of certifications. Some claim certifications they don’t actually have (HINT: PCI does not certify encryption software) and some will use confusing language to infer they have achieved levels of certification they haven’t. Recently I visited a website that claimed (I’m paraphrasing):
Our stuff uses FIPS 140-2 certified algorithms to ensure the highest level of data security.The
NIST AES website displays no record of this company ever having received a certification for any encryption software. Clearly they recognize the value of certification, but have not yet knuckled down to do the hard work to make it so. And if you don’t check their supposed “facts,” it’s likely that you’ll soon regret it.
My advice? When someone claims to be certified for any type of encryption, ask a simple question: “Can you show me the cert?” It ought to be available on the web, or in paper form that they can show to you so that you know this software has passed an independent evaluation. If they have a cert, then you can dig down deeper and find out whether the software will fit your needs. But if they are claiming a certification that they cannot prove, my advice is to keep your hand on your wallet and then run.
For more information on encryption and key management, download our white paper titled "
AES Encryption and Related Concepts."
 This customer currently has our managed file transfer solution, FTP Manager with PGP encryption, and was confused as to why they would need AES encryption if they were using PGP. I explained that PGP encryption protects data in motion - when it is transferred outside his company. If he was storing data on his AS/400, he would need AES encryption to protect his data at rest.
This customer currently has our managed file transfer solution, FTP Manager with PGP encryption, and was confused as to why they would need AES encryption if they were using PGP. I explained that PGP encryption protects data in motion - when it is transferred outside his company. If he was storing data on his AS/400, he would need AES encryption to protect his data at rest. AES Encryption
AES Encryption ![]() PGP encryption is the standard when it comes to encrypting files that need to be transferred. Pretty Good Privacy (PGP) is the standard for encrypted file exchange among the world’s largest financial, medical, industrial, and services companies. Also know that when encrypting a file with PGP, you may be using AES encryption.
PGP encryption is the standard when it comes to encrypting files that need to be transferred. Pretty Good Privacy (PGP) is the standard for encrypted file exchange among the world’s largest financial, medical, industrial, and services companies. Also know that when encrypting a file with PGP, you may be using AES encryption. 

 At Townsend, we have a lot of conversations with customers and prospects about data privacy, compliance requirements and best practices for IT security in general. We have written numerous articles on these topics and posted them on our blog. As the end of 2011 quickly approaches, we thought it would be worthwhile to list out our most read articles of the year.
At Townsend, we have a lot of conversations with customers and prospects about data privacy, compliance requirements and best practices for IT security in general. We have written numerous articles on these topics and posted them on our blog. As the end of 2011 quickly approaches, we thought it would be worthwhile to list out our most read articles of the year. 


 When you stop to think about it, this makes perfect sense. If the world used a secret algorithm to encrypt data, if that algorithm were ever to be discovered then all the world’s data would be at risk. But if the key is the one-and-only secret that unlocks the data, then a compromised key only puts the data at risk that was encrypted with that particular key. All the other data that has been encrypted with other keys is still safe. This demonstrates both the wisdom of strong (and open) algorithms, but also the essential importance of strong key protection.
When you stop to think about it, this makes perfect sense. If the world used a secret algorithm to encrypt data, if that algorithm were ever to be discovered then all the world’s data would be at risk. But if the key is the one-and-only secret that unlocks the data, then a compromised key only puts the data at risk that was encrypted with that particular key. All the other data that has been encrypted with other keys is still safe. This demonstrates both the wisdom of strong (and open) algorithms, but also the essential importance of strong key protection. Many software vendors are beginning to recognize the value of certifications. Some claim certifications they don’t actually have (HINT: PCI does not certify encryption software) and some will use confusing language to infer they have achieved levels of certification they haven’t. Recently I visited a website that claimed (I’m paraphrasing):
Many software vendors are beginning to recognize the value of certifications. Some claim certifications they don’t actually have (HINT: PCI does not certify encryption software) and some will use confusing language to infer they have achieved levels of certification they haven’t. Recently I visited a website that claimed (I’m paraphrasing):
 AES encryption has become the de facto standard for protecting data at rest in databases and unstructured data such as flat files, messages, EDI, and XML documents. As enterprises deploy data security solutions to meet compliance requirements, they are frequently surprised by the performance impacts of encryption. Inadequate attention to encryption performance can lead to increased costs, delayed or failed projects, compliance failure, reduced flexibility to meet competitive challenges, and exposure to legal liability.
AES encryption has become the de facto standard for protecting data at rest in databases and unstructured data such as flat files, messages, EDI, and XML documents. As enterprises deploy data security solutions to meet compliance requirements, they are frequently surprised by the performance impacts of encryption. Inadequate attention to encryption performance can lead to increased costs, delayed or failed projects, compliance failure, reduced flexibility to meet competitive challenges, and exposure to legal liability.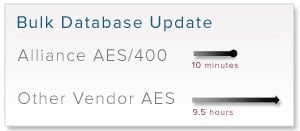 A large multi-brand retailer, that sells its products online and in traditional retail outlets needed to meet PCI Data Security Standards for protecting customer credit card information. After evaluating several different vendors for performance they decided on AES Encryption from Townsend Security. They deployed the Alliance AES/400 Encryption solution to protect sensitive data in DB2 database files and in a variety of unstructured data files and were able to achieve PCI compliance in record time.
A large multi-brand retailer, that sells its products online and in traditional retail outlets needed to meet PCI Data Security Standards for protecting customer credit card information. After evaluating several different vendors for performance they decided on AES Encryption from Townsend Security. They deployed the Alliance AES/400 Encryption solution to protect sensitive data in DB2 database files and in a variety of unstructured data files and were able to achieve PCI compliance in record time.

 I just listened to a discussion of database security hosted by Oracle that was very well done. At one point the discussion turned to current threats and how the Enterprise has lost the ability to use perimeter protection for sensitive data. This has been a topic of much discussion in the security area for the last few months. Perimeter protection is based on the use of Firewall and similar technologies to keep the bad guys out, but this approach is failing with the advance of more sophisticated attacks, the use of social media by large organizations, the advance of mobile technologies, insider threats, and the migration of applications to cloud platforms. The trend is called “de-perimeterization” and represents a bit of a challenge to organizations that need to protect sensitive data.
I just listened to a discussion of database security hosted by Oracle that was very well done. At one point the discussion turned to current threats and how the Enterprise has lost the ability to use perimeter protection for sensitive data. This has been a topic of much discussion in the security area for the last few months. Perimeter protection is based on the use of Firewall and similar technologies to keep the bad guys out, but this approach is failing with the advance of more sophisticated attacks, the use of social media by large organizations, the advance of mobile technologies, insider threats, and the migration of applications to cloud platforms. The trend is called “de-perimeterization” and represents a bit of a challenge to organizations that need to protect sensitive data.