The time required to crack an encryption algorithm is directly related to the length of the key used to secure the data.
 Every now and then, our development team comes across someone still using antiquated DES for encryption. If you haven’t made the switch to the Advanced Encryption Standard (AES), let’s take a look at the two standards and see why you should!
Every now and then, our development team comes across someone still using antiquated DES for encryption. If you haven’t made the switch to the Advanced Encryption Standard (AES), let’s take a look at the two standards and see why you should!
Data Encryption Standard (DES):
DES is a symmetric block cipher (shared secret key), with a key length of 56-bits. Published as the Federal Information Processing Standards (FIPS) 46 standard in 1977, DES was officially withdrawn in 2005 [although NIST has approved Triple DES (3DES) through 2030 for sensitive government information].
The federal government originally developed DES encryption over 35 years ago to provide cryptographic security for all government communications. The idea was to ensure government systems all used the same, secure standard to facilitate interconnectivity.
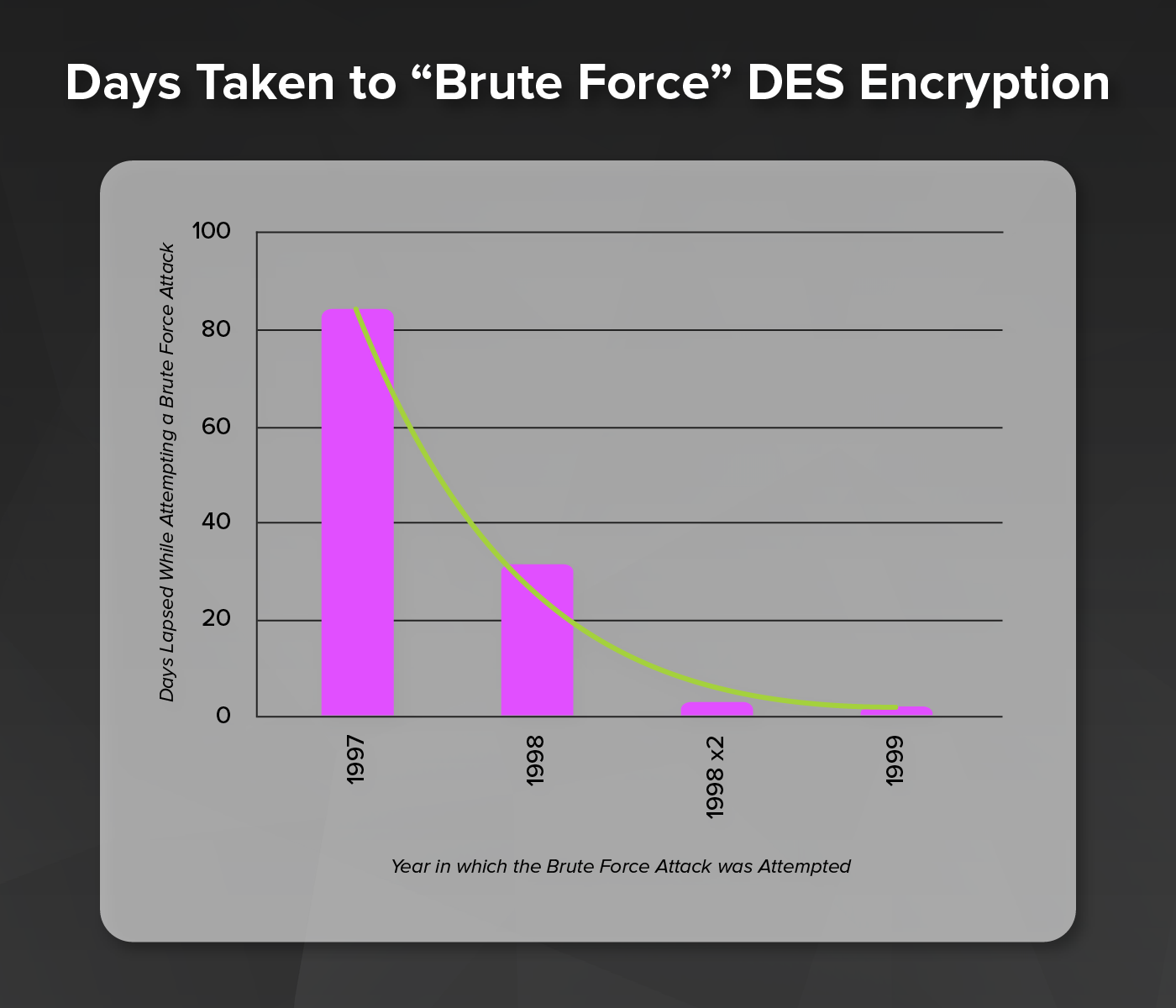
To show that the DES was inadequate and should not be used in important systems anymore, a series of challenges were sponsored to see how long it would take to decrypt a message. Two organizations played key roles in breaking DES: distributed.net and the Electronic Frontier Foundation (EFF).
- The DES I contest (1997) took 84 days to use a brute force attack to break the encrypted message.
- In 1998, there were two DES II challenges issued. The first challenge took just over a month and the decrypted text was "The unknown message is: Many hands make light work". The second challenge took less than three days, with the plaintext message "It's time for those 128-, 192-, and 256-bit keys".
- The final DES III challenge in early 1999 only took 22 hours and 15 minutes. Electronic Frontier Foundation's Deep Crack computer (built for less than $250,000) and distributed.net's computing network found the 56-bit DES key, deciphered the message, and they (EFF & distributed.net) won the contest. The decrypted message read "See you in Rome (Second AES Candidate Conference, March 22-23, 1999)", and was found after checking about 30 percent of the key space...Finally proving that DES belonged to the past.
Even Triple DES (3DES), a way of using DES encryption three times, proved ineffective against brute force attacks (in addition to slowing down the process substantially).
Advanced Encryption Standard (AES):
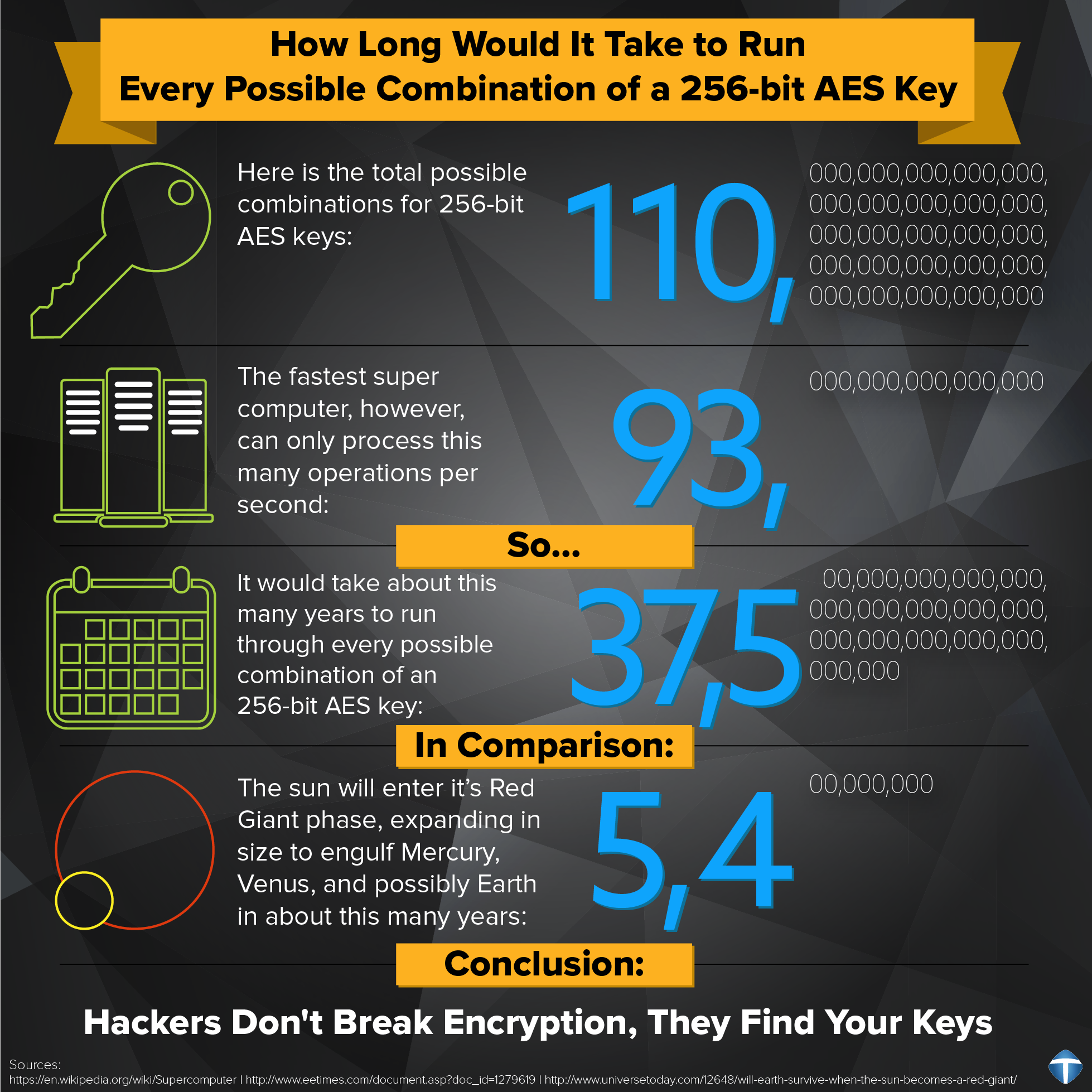
Published as a FIPS 197 standard in 2001. AES data encryption is a more mathematically efficient and elegant cryptographic algorithm, but its main strength rests in the option for various key lengths. AES allows you to choose a 128-bit, 192-bit or 256-bit key, making it exponentially stronger than the 56-bit key of DES. In terms of structure, DES uses the Feistel network which divides the block into two halves before going through the encryption steps. AES on the other hand, uses permutation-substitution, which involves a series of substitution and permutation steps to create the encrypted block. The original DES designers made a great contribution to data security, but one could say that the aggregate effort of cryptographers for the AES algorithm has been far greater.
One of the original requirements by the National Institute of Standards and Technology (NIST) for the replacement algorithm was that it had to be efficient both in software and hardware implementations (DES was originally practical only in hardware implementations). Java and C reference implementations were used to do performance analysis of the algorithms. AES was chosen through an open competition with 15 candidates from as many research teams around the world, and the total amount of resources allocated to that process was tremendous. Finally, in October 2000, a NIST press release announced the selection of Rijndael as the proposed Advanced Encryption Standard (AES).
Comparing DES and AES
| DES | AES | |
| Developed | 1977 | 2000 |
| Key Length | 56 bits | 128, 192, or 256 bits |
| Cipher Type | Symmetric block cipher | Symmetric block cipher |
| Block Size | 64 bits | 128 bits |
| Security | Proven inadequate | Considered secure |
So the question remains for anyone still using DES encryption…
How can we help you make the switch to AES?




 Enter PGP. PGP stands for Pretty Good Privacy, and before you get too distracted by the name, I can tell you it is actually much better than just pretty good. PGP uses symmetric and asymmetric keys to encrypt data being transferred across networks. It was developed by the American computer scientist Phil Zimmerman, who made it available for non-commercial use for no charge in 1991. To encrypt data, PGP generates a symmetric key to encrypt data which is protected by the asymmetric key.
Enter PGP. PGP stands for Pretty Good Privacy, and before you get too distracted by the name, I can tell you it is actually much better than just pretty good. PGP uses symmetric and asymmetric keys to encrypt data being transferred across networks. It was developed by the American computer scientist Phil Zimmerman, who made it available for non-commercial use for no charge in 1991. To encrypt data, PGP generates a symmetric key to encrypt data which is protected by the asymmetric key.




 The newest version of the IBM i (AS400) operating system, V7R1, brings sophisticated new security tools from IBM’s larger systems to mid-range markets. These new features allow third-party companies such as Townsend Security to offer NIST-certified automatic AES encryption, so that you can now encrypt your sensitive data without application changes!
The newest version of the IBM i (AS400) operating system, V7R1, brings sophisticated new security tools from IBM’s larger systems to mid-range markets. These new features allow third-party companies such as Townsend Security to offer NIST-certified automatic AES encryption, so that you can now encrypt your sensitive data without application changes!

 AES Encryption
AES Encryption 


 It was fascinating to read the headlines this week about the terrible flaw that was discovered in the Advanced Encryption Standard (AES). It sounded like the end of security as we know it. I read blogs and articles that headlined “AES Broken” and “Fatal Flaw in AES”. It was fun reading, but completely misleading. So, what really happened?
It was fascinating to read the headlines this week about the terrible flaw that was discovered in the Advanced Encryption Standard (AES). It sounded like the end of security as we know it. I read blogs and articles that headlined “AES Broken” and “Fatal Flaw in AES”. It was fun reading, but completely misleading. So, what really happened? When encrypting data, the most widely accepted cryptographic standard is the Advanced Encryption Standard (AES).
When encrypting data, the most widely accepted cryptographic standard is the Advanced Encryption Standard (AES). There are several potential problems related to the use of the CUSP mode of AES encryption.
There are several potential problems related to the use of the CUSP mode of AES encryption.
 As it turns out, the weakness, in these devices, was not in the actual AES encryption, but in the key management processes. All the affected vendors quickly released replacements or patches to fix the problem, which is the right thing to do. But it was fascinating to watch some of the responses to this problem. Many commentators complained that the FIPS-140 testing was faulty, or that FIPS-140 testing was irrelevant. The implication is that FIPS-140 does not really give you any assurance of security, and therefore, also by implication, that it is not important.
As it turns out, the weakness, in these devices, was not in the actual AES encryption, but in the key management processes. All the affected vendors quickly released replacements or patches to fix the problem, which is the right thing to do. But it was fascinating to watch some of the responses to this problem. Many commentators complained that the FIPS-140 testing was faulty, or that FIPS-140 testing was irrelevant. The implication is that FIPS-140 does not really give you any assurance of security, and therefore, also by implication, that it is not important. First, FIPS-140 certification is not a guarantee of security. It is an assurance that encryption and related security algorithms have been implemented in compliance with published standards, that an application uses good practices in exposing it’s operational interfaces, that start up tests validate that the application has not been modified or corrupted, that cryptographic material is not exposed in application logs or leaked to memory, and that an independent expert has reviewed the source code. Going through a FIPS-140 certification is a grueling process for an encryption vendor and almost always results in finding some issues that need to be addressed to make the product more secure. Companies that engage in FIPS-140 certifications produce better products, and become better security designers in the process.
First, FIPS-140 certification is not a guarantee of security. It is an assurance that encryption and related security algorithms have been implemented in compliance with published standards, that an application uses good practices in exposing it’s operational interfaces, that start up tests validate that the application has not been modified or corrupted, that cryptographic material is not exposed in application logs or leaked to memory, and that an independent expert has reviewed the source code. Going through a FIPS-140 certification is a grueling process for an encryption vendor and almost always results in finding some issues that need to be addressed to make the product more secure. Companies that engage in FIPS-140 certifications produce better products, and become better security designers in the process. When you stop to think about it, this makes perfect sense. If the world used a secret algorithm to encrypt data, if that algorithm were ever to be discovered then all the world’s data would be at risk. But if the key is the one-and-only secret that unlocks the data, then a compromised key only puts the data at risk that was encrypted with that particular key. All the other data that has been encrypted with other keys is still safe. This demonstrates both the wisdom of strong (and open) algorithms, but also the essential importance of strong key protection.
When you stop to think about it, this makes perfect sense. If the world used a secret algorithm to encrypt data, if that algorithm were ever to be discovered then all the world’s data would be at risk. But if the key is the one-and-only secret that unlocks the data, then a compromised key only puts the data at risk that was encrypted with that particular key. All the other data that has been encrypted with other keys is still safe. This demonstrates both the wisdom of strong (and open) algorithms, but also the essential importance of strong key protection. Many software vendors are beginning to recognize the value of certifications. Some claim certifications they don’t actually have (HINT: PCI does not certify encryption software) and some will use confusing language to infer they have achieved levels of certification they haven’t. Recently I visited a website that claimed (I’m paraphrasing):
Many software vendors are beginning to recognize the value of certifications. Some claim certifications they don’t actually have (HINT: PCI does not certify encryption software) and some will use confusing language to infer they have achieved levels of certification they haven’t. Recently I visited a website that claimed (I’m paraphrasing):