Over the last several years, encryption key management has attained “essential infrastructure” status. When done properly, key management can protect encrypted data - and in the event of a data breach, can even provide a company with an exemption for a breach notification.
 I recently sat down with Patrick Townsend, Founder and CEO of Townsend Security to talk about encryption key management and the importance of standards, what to look for in a key manager, and fundamental features of an enterprise grade key manager. While Townsend Security isn’t alone in the key management game, there are a few telltale signs that differentiate a key manager that meets industry standards and one that will leave you with a breach notification on your hands. Let’s jump in.
I recently sat down with Patrick Townsend, Founder and CEO of Townsend Security to talk about encryption key management and the importance of standards, what to look for in a key manager, and fundamental features of an enterprise grade key manager. While Townsend Security isn’t alone in the key management game, there are a few telltale signs that differentiate a key manager that meets industry standards and one that will leave you with a breach notification on your hands. Let’s jump in.
Hi Patrick. Townsend Security has been in the key management game for close to 10 years now. Back when Alliance Key Manager was brought to market, people weren’t really sure what key management was. Now it is considered essential infrastructure.
Yes, it sure is. Things have changed so dramatically over the last few years. Encrypting sensitive data is now a requirement for businesses who need to meet data privacy compliance regulations. And it is also achieving visibility at the executive level as a part of a GRC (governance, risk, compliance) plan. The landscape really has changed a great deal, and I think organizations are stepping up and doing a better job.
We are also seeing databases implementing encryption directly into the database engine. MongoDB Enterprise is an excellent example of this by incorporating AES encryption into the WiredTiger storage engine and providing KMIP for good key management. Microsoft SQL Server Enterprise has also built the encryption engine right into the database with transparent data encryption (TDE) and provides extensible key management (EKM) for vendors like us to plug in to and allow users to properly manage encryption keys.
Let’s spend a minute on compliance. What regulations require key management?
It is true that there are a lot of compliance regulations and most of us fall under multiple. Certainly, GDPR and the new Australian law have come on board and are affecting the way companies all over the world, even outside of the EU, who are now taking steps to protect that data. Almost all regulations require the protection of data, which encryption can help with. Regarding encryption, from a best practices point of view, if you don’t have proper key management, you don’t have encryption.
PCI DSS and the payment industry has now been with us for a decade and that also drives the protection of a lot of sensitive data. While PCI DSS is a private regulation between merchants who accept credit cards and the industry, it is a strong regulation with strong penalties. Because of the longevity and focus on security, PCI DSS often informs other regulations and corporate governance boards.
While we live in a very complex set of compliance requirements, there are fortunately some similarities. When we set out to protect sensitive data, and do it right, which I am sure you know by now means based on standards and security best practices, we find business meeting a broad set of regulations.
As I mentioned earlier, key management is considered essential infrastructure. Back when Townsend Security first entered the market, there were just a few options for the enterprise to choose from. Today, options have dramatically increased. With that said, there are a few ways to distinguish a key manager that meets industry standards and one that will leave you with a breach notification on your hands.
There are a few key quality indicators when assessing key management systems. First off, a key management server must be validated to FIPS 140-2. That is the US and Canadian standard for cryptographic modules and it is just a fundamental indicator of the seriousness of a company and its ability to build good key management solutions. Unfortunately, there are claims of FIPS 140-2 compliance by vendors who have systems which have actually not completed a validation. It’s always a good idea to ask your key management vendor what their certificate number is so that you can look it up yourself on the NIST website. Additionally, key management vendors should be able meet KMIP requirements by demonstrating interoperability. These sorts of validations and certifications show that a key management vendor is stepping up to the technical requirements that customers expect.
Finally, there are individual specific validations to regulations. Our key manager, for example, has been through a PCI DSS validation with a QSA auditor and with VMware. You want to avoid solutions that are simply “key storage” which haven’t been validated and there has not been external review and validation of the cryptographic approach. It is incredibly easy to get encryption and key management wrong from a technical point of view.
Third-party attestations and validations are critically important. You are putting your digital assets, not to mention your company’s reputation, at risk when you use a poor quality key management server (KMS). Fortunately, today there are very affordable solutions available everywhere from a traditional hardware security module, to VMware, to the cloud. 10 years ago, key management servers where terribly expensive.
Yeah, I have been seeing key managers hitting the market that range from open source to cloud service provider (CSP) provided. Some key managers will even claim FIPS compliance when a simple check with NIST shows them nowhere to be found. You also get providers who claim FIPS compliance because they are using a module that has been through a validation, which as I am sure you can tell us more about, doesn’t make your solution compliant.
That’s right. Unfortunately, there is still a fair amount of snake oil in the industry. People claim FIPS 140-2 compliance, but haven’t fully been through the process. As you mentioned, claiming one component as being FIPS 140-2 compliant does not make your entire solution compliant. I like to say, “I drive a Toyota. If I put a Jaguar hood ornament on my car, it doesn't turn my car into a Jaguar. It is still a Toyota!” There is a lot of language used by some solution providers that just isn’t accurate and should be verified before choosing a solution.
You also talked about governance. Let’s take a look at the recent Marriott/Starwood breach. There was an interesting statement where they said “we can’t be absolutely sure that the encryption keys weren’t lost.” If you are using enterprise level key management systems, you have monitoring and audit trails that will show if keys have been retrieved. By them not knowing, it is easy to surmise that they weren’t adequately protecting our information. This was a failure of governance in regards to critical security infrastructure. We might not be talking about the breach right now had they had industry standard key management in place.
Changing gears a little, we have in the past seen cloud vendors offer key management systems in their shared environments. Multi tenant key management presents a concern for enterprises. Just last week I had a conversation with a security professional from a global enterprise who said, “for us, trust is paramount to our brand. We will never allow encryption keys to be stored and accessed by a cloud vendor.” I thought it was a very interesting statement and completely lines up with other enterprises that I speak with.
There is also a bit of confusion on the term KMS. For example, VMware defines KMS as a Key Management Server. Amazon, on the other hand, defines their KMS as a “Key Management Service.”
Well, there is a bit of confusion on this isn’t there? A true enterprise key management system (KMS), is responsible for the entire lifecycle of an encryption key - from generation where admins create provably strong keys, to storage, to provisioning applications and users who need the keys, all the way through to the archival and destruction of the keys. Key management systems manage all of those phases according to industry standards.
A key management service can better be defined as storage service and offers a mix of capabilities. Some are services that are shared, multi-tenant environments. CSP key managers often work this way (think AWS KMS, Azure Key Vault). Many services don’t give you full access or control over a key’s complete lifecycle. Some services allow you to bring your own key, but then bring that into their own infrastructure, where you then share administrative access and control.
It is very important to know that if you are truly trying to do security the right way, you need a key management system that is built to industry standards and validated to industry standards. One last point, it is possible to do key management correctly in the cloud. There are third-party key management offerings that can be found in the marketplace that meet all the standards that we have been talking about, and are dedicated to you and only you. Our Alliance Key Manager is one, for example.
A feature that we are very proud of with our key manager is that it runs the same software in the Cloud, VMware, or as a traditional hardware security module (HSM). We have customers setting up hybrid cloud/on-prem deployments or even cross-cloud. The way we license our key managers works really well for the modern enterprise which needs a predictable, low TCO. With Alliance Key Manager, there are never added fees for additional databases or applications.
To hear this conversation in its entirety, download our podcast Don’t Forget About FIPS 140-2 and Other Fundamental Key Management Features and hear Patrick Townsend further what enterprises should look for in a key manager, the importance of standards, and other fundamental features of an enterprise grade key manager.



 As the social revolution moves into the business world, protecting your data is more important than ever. This was a key takeaway for attendees of the recent “Dreamforce to You” event in Seattle, WA, hosted by Salesforce.
As the social revolution moves into the business world, protecting your data is more important than ever. This was a key takeaway for attendees of the recent “Dreamforce to You” event in Seattle, WA, hosted by Salesforce. We couldn’t agree more. As a security company, this is something we have been saying since the beginning. We have offered NIST-validated AES encryption for all the major enterprise platforms for over ten years, been securing managed file transfers with PGP encryption, and recently stepped up our game with a FIPS 140-2 compliant encryption key management HSM. Simply put, we are helping organizations protect their sensitive information and meet compliance regulations with certified encryption solutions.
We couldn’t agree more. As a security company, this is something we have been saying since the beginning. We have offered NIST-validated AES encryption for all the major enterprise platforms for over ten years, been securing managed file transfers with PGP encryption, and recently stepped up our game with a FIPS 140-2 compliant encryption key management HSM. Simply put, we are helping organizations protect their sensitive information and meet compliance regulations with certified encryption solutions.
 When I had this “Aha” moment years ago, I realized that our company had to radically change how we approached the development of our encryption and key management products. I knew that we had to step up to much higher standards, and change how we looked at our own products. But where does one go to figure out how to do encryption right? Fortunately, our company had several good enterprise customers who helped point the way. Enterprise security architects directed us to the National Institute of Standards and Technology (NIST) web site and the FIPS-140 certification process. The NIST and FIPS-140 certification outline the proper standards and best practices for encryption, decryption, key management, and logging. So began the complete transformation in how we bring Townsend Security encryption products to market.
When I had this “Aha” moment years ago, I realized that our company had to radically change how we approached the development of our encryption and key management products. I knew that we had to step up to much higher standards, and change how we looked at our own products. But where does one go to figure out how to do encryption right? Fortunately, our company had several good enterprise customers who helped point the way. Enterprise security architects directed us to the National Institute of Standards and Technology (NIST) web site and the FIPS-140 certification process. The NIST and FIPS-140 certification outline the proper standards and best practices for encryption, decryption, key management, and logging. So began the complete transformation in how we bring Townsend Security encryption products to market. Well, you already know how this came out. In the end I could come to no other conclusion. We would either do the right thing, or get out of the security market altogether. We’re still in, so you know that we made that commitment and investment in NIST certification of our correctly implemented encryption solutions. We did learn a lot about encryption development processes and best practices. And I must say our products are so much better for it.
Well, you already know how this came out. In the end I could come to no other conclusion. We would either do the right thing, or get out of the security market altogether. We’re still in, so you know that we made that commitment and investment in NIST certification of our correctly implemented encryption solutions. We did learn a lot about encryption development processes and best practices. And I must say our products are so much better for it.
 AES encryption has become the de facto standard for protecting data at rest in databases and unstructured data such as flat files, messages, EDI, and XML documents. As enterprises deploy data security solutions to meet compliance requirements, they are frequently surprised by the performance impacts of encryption. Inadequate attention to encryption performance can lead to increased costs, delayed or failed projects, compliance failure, reduced flexibility to meet competitive challenges, and exposure to legal liability.
AES encryption has become the de facto standard for protecting data at rest in databases and unstructured data such as flat files, messages, EDI, and XML documents. As enterprises deploy data security solutions to meet compliance requirements, they are frequently surprised by the performance impacts of encryption. Inadequate attention to encryption performance can lead to increased costs, delayed or failed projects, compliance failure, reduced flexibility to meet competitive challenges, and exposure to legal liability.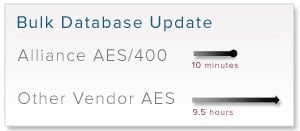 A large multi-brand retailer, that sells its products online and in traditional retail outlets needed to meet PCI Data Security Standards for protecting customer credit card information. After evaluating several different vendors for performance they decided on AES Encryption from Townsend Security. They deployed the Alliance AES/400 Encryption solution to protect sensitive data in DB2 database files and in a variety of unstructured data files and were able to achieve PCI compliance in record time.
A large multi-brand retailer, that sells its products online and in traditional retail outlets needed to meet PCI Data Security Standards for protecting customer credit card information. After evaluating several different vendors for performance they decided on AES Encryption from Townsend Security. They deployed the Alliance AES/400 Encryption solution to protect sensitive data in DB2 database files and in a variety of unstructured data files and were able to achieve PCI compliance in record time. In our encryption practice we often help customers integrate the exchange of encrypted data between different applications within the organization, and between their own applications and a vendor’s or customer’s application. It is truly amazing to me how often we encounter non-standard encryption that makes this integration very difficult. The problem is not the lack of standards for encryption. Most compliance regulations provide clear guidance and references to encryption standards. Here is what the PCI Data Security Standard (PCI DSS) Navigation Guide says about encryption (my emphasis):
In our encryption practice we often help customers integrate the exchange of encrypted data between different applications within the organization, and between their own applications and a vendor’s or customer’s application. It is truly amazing to me how often we encounter non-standard encryption that makes this integration very difficult. The problem is not the lack of standards for encryption. Most compliance regulations provide clear guidance and references to encryption standards. Here is what the PCI Data Security Standard (PCI DSS) Navigation Guide says about encryption (my emphasis): I just returned from a trip to Europe and Encryption Key Management was a very hot topic. This is a topic I very much like to speak about, given our recent release of
I just returned from a trip to Europe and Encryption Key Management was a very hot topic. This is a topic I very much like to speak about, given our recent release of 

