 MSP identifying and implementing top-notch business, security, and IT solutions
MSP identifying and implementing top-notch business, security, and IT solutions
“Encryption key management for VMware vSphere, with usage-based licensing, has allowed us to better secure our SMB customers and add a new revenue stream.”
- Don DaRe, President & CEO
Concensus Technologies
The Challenge: Customers Needed Affordable Encryption & Key Management to Meet Security & Insurance Requirements
For Concensus Technologies, an MSP who offers complete cybersecurity, managed IT services, and IAM solutions for businesses, encryption and key management are paramount to keeping their customers’ data secure. Before partnering with Townsend Security, encryption key management was a facet of security that was beyond the budget of their SMB customers who needed to meet regulatory compliance like PCI DSS, HIPAA, etc., as well as purchase cybersecurity insurance.
Don DaRe, President and CEO, helps guide his customers through the process of securing their data, a differentiator for him as an MSP. “If you are an MSP, you need to think about security first, not after there has been a breach. Encryption and key management will help keep your customer’s data safe,” said DaRe.
Whether he is helping them through a cyber-risk insurance audit or meeting compliance requirements, Concensus Technologies partners with their customers to securely meet their technology initiatives. If there is sensitive data on the VM, DaRe helps customers understand the best way to protect it is with encryption and key management.
“Because of stricter data security compliance and cyber- risk insurance requirements, customers began asking for encryption. We quickly realized that a secure data center in the cloud wasn’t enough,” said DaRe.
To ensure data is truly secure, and have predictable costs, Concensus Technologies decided it was best to run their own VMware infrastructure, and partner with a key management vendor. The only problem - finding a key management vendor who would match an MSP’s usage- based business model.
After talking with a few key management vendors who offered solutions for prices that only large enterprises could afford, Don DaRe, President and CEO, found Townsend Security.
“As an MSP, we charge our customers for usage. Having encryption key management that has been through a NIST validation, with usage-based licensing, is key for us - which removes price as a barrier to good security,” continued DaRe.
The Solution
Alliance Key Manager for VMware
Unhappy with the cost and performance of the major cloud service providers (CSPs), Concensus Technologies decided to build their own VMware infrastructure. When moving from the cloud to their own, meeting data security compliance was a top concern.
By deploying Alliance Key Manager for VMware in their VMware vCloud infrastructure, the company was able to meet customer requirements for encryption and key management, as well as create a new revenue stream.
Usage-Based Licensing
Businesses are moving away from paying for perpetual licensing. “Everything is moving towards a subscription/pay for what you use model,” said DaRe. “For most companies we work with, they would rather have the operational expenditure than the capital expenditure.”
“As an MSP, we are always looking for solutions and services that are easy to track and easy to use - and don’t require much maintenance,” said DaRae. “Townsend Security checks all those boxes.”
Plug & Play Security
“Because Alliance Key Manager snaps right in to vCenter, we just make a ‘Click’ and customer data is encrypted. It doesn’t take a lot of engineer time to implement. Between Townsend Security’s support and one of our engineers, we had it up and running in less than an hour,” said DaRe.
By lowering the cost and difficulty barriers of encryption, Concensus Technologies is seeing their customers have a tremendously improved security posture, and realizing new revenue.
“We were able to deploy Alliance Key Manager and offer encryption to our customers all in the same day. It is now a part of all of our quotes.”


 IT Solution Provider Helps Customer Protect vSphere and vSAN Encryption Keys with Alliance Key Manager for VMWare
IT Solution Provider Helps Customer Protect vSphere and vSAN Encryption Keys with Alliance Key Manager for VMWare
 With SEBI’s new cyber security framework, JM Financial Asset Management Ltd turned to Indus Systems for guidance on how to better protect their data. JM Financial Asset Management Ltd, an Indus Systems customer of 10 years, were due for a technology refresh. As part of the project, the company would rely heavily on VMware and protecting private data with vSphere and vSAN encryption.
With SEBI’s new cyber security framework, JM Financial Asset Management Ltd turned to Indus Systems for guidance on how to better protect their data. JM Financial Asset Management Ltd, an Indus Systems customer of 10 years, were due for a technology refresh. As part of the project, the company would rely heavily on VMware and protecting private data with vSphere and vSAN encryption.
 Secrets Management SaaS for CMS Systems Including Drupal and WordPress
Secrets Management SaaS for CMS Systems Including Drupal and WordPress

 Securing Data in MongoDB Enterprise with Alliance Key Manager
Securing Data in MongoDB Enterprise with Alliance Key Manager

 Meeting PCI DSS with Townsend Security's Alliance Key Manager Hardware Security Module (HSM)
Meeting PCI DSS with Townsend Security's Alliance Key Manager Hardware Security Module (HSM)

 Compliance Made Easy - Protecting Private Information with Alliance AES/400 Encryption for IBM i and Alliance Key Manager for VMware
Compliance Made Easy - Protecting Private Information with Alliance AES/400 Encryption for IBM i and Alliance Key Manager for VMware



 One of our customers recently submitted a support ticket related to a question asked by their QSA Auditor. Just a quick background on our customer - they have an all IBM i environment and are using AES/400, our NIST-certified AES encryption among other data privacy solutions we offer. This customer needs to comply with PCI because they are accepting credit cards and store personally identifiable information (PII). The question was: How does your AES encryption software prevent unauthorized substitution of cryptographic keys?
One of our customers recently submitted a support ticket related to a question asked by their QSA Auditor. Just a quick background on our customer - they have an all IBM i environment and are using AES/400, our NIST-certified AES encryption among other data privacy solutions we offer. This customer needs to comply with PCI because they are accepting credit cards and store personally identifiable information (PII). The question was: How does your AES encryption software prevent unauthorized substitution of cryptographic keys?
 As a company that provides NIST-certified encryption and FIPS 140-2 encryption key management, we need to secure data on a number of different platforms. Lately we have been coming into several cases where a customer needs encryption and key management on both Microsoft SQL Server and Oracle databases. Below is an email exchange with a customer who came to us “looking for a product to store, generate and manage keys that we use to encrypt/decrypt credit card information inside both SQL Server and Oracle Databases on Windows and UNIX.” We hope this discussion helps with your encryption project.
As a company that provides NIST-certified encryption and FIPS 140-2 encryption key management, we need to secure data on a number of different platforms. Lately we have been coming into several cases where a customer needs encryption and key management on both Microsoft SQL Server and Oracle databases. Below is an email exchange with a customer who came to us “looking for a product to store, generate and manage keys that we use to encrypt/decrypt credit card information inside both SQL Server and Oracle Databases on Windows and UNIX.” We hope this discussion helps with your encryption project. Key Generation:
Key Generation:
 AES encryption has become the de facto standard for protecting data at rest in databases and unstructured data such as flat files, messages, EDI, and XML documents. As enterprises deploy data security solutions to meet compliance requirements, they are frequently surprised by the performance impacts of encryption. Inadequate attention to encryption performance can lead to increased costs, delayed or failed projects, compliance failure, reduced flexibility to meet competitive challenges, and exposure to legal liability.
AES encryption has become the de facto standard for protecting data at rest in databases and unstructured data such as flat files, messages, EDI, and XML documents. As enterprises deploy data security solutions to meet compliance requirements, they are frequently surprised by the performance impacts of encryption. Inadequate attention to encryption performance can lead to increased costs, delayed or failed projects, compliance failure, reduced flexibility to meet competitive challenges, and exposure to legal liability.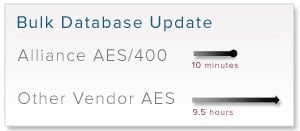 A large multi-brand retailer, that sells its products online and in traditional retail outlets needed to meet PCI Data Security Standards for protecting customer credit card information. After evaluating several different vendors for performance they decided on AES Encryption from Townsend Security. They deployed the Alliance AES/400 Encryption solution to protect sensitive data in DB2 database files and in a variety of unstructured data files and were able to achieve PCI compliance in record time.
A large multi-brand retailer, that sells its products online and in traditional retail outlets needed to meet PCI Data Security Standards for protecting customer credit card information. After evaluating several different vendors for performance they decided on AES Encryption from Townsend Security. They deployed the Alliance AES/400 Encryption solution to protect sensitive data in DB2 database files and in a variety of unstructured data files and were able to achieve PCI compliance in record time.