
As compliance regulations start mandating encryption and key management, we are seeing more and more companies stepping up their data security policies. One important thing to realize is, that just because you are implementing encryption, it doesn’t necessarily mean that you are doing it correctly and will meet regulations such as PCI DSS, HIPAA/HITECH, State Privacy Laws, etc.
We have compiled a list of the top ten encryption pitfalls that your enterprise needs to be aware of.
1) Encryption Key Management
Encryption requires a proper key management strategy. This means protecting and isolating encryption keys from the data that they protect. For most companies this means using a proper key management solution across all of their servers and applications. Townsend Security offers Alliance Key Manager to help meet key management and compliance regulations.
2) Completeness and Compatibility
It’s not uncommon for some encryption solutions to only implement a partial specification of AES encryption. There are nine encryption modes (five for business data) that can be used with AES encryption. An incomplete solution that encrypts with one mode — such as CBC — will leave you unable to decrypt with another mode like ECB. This incompatibility makes transferring encrypted data from one server to another difficult or impossible. Townsend Security’s Alliance AES Encryption is NIST-certified on all five modes for business data.
3) NIST Certification
As regulators refine the requirements for encryption and key management, the certification of products to NIST standards is more important. The recent 2009 HITECH Act makes specific reference to the NIST standards for encryption and key management. Many vendors of encryption solutions ignore NIST certification leaving their customers exposed to these evolving regulations.
4) Performance
The impact of encryption on servers and applications is often an unpleasant surprise as companies implement their data security plans. There are large differences in the performance of vendor solutions. The performance impact of encryption can delay or derail data security efforts.
5) Application Modifications
Implementing encryption at the database level often involves some application redesign and modification. This requires work by companies and their vendors. This work is often unplanned and unbudgeted, causing financial and human resource problems. It is important to make sure your application modifications are minimal.
6) Quality Assurance and UAT Testing
When applications and databases are modified to implement encryption, there is a need to re-certify them for accuracy, reliability and performance. Many companies find this effort larger than the effort to implement encryption.
7) Data Leakage to QA and Test Environments
Every company that maintains business applications must keep a set of data available to the developer and user acceptance teams so that changes can be adequately tested. Often the data used in these test environments contains sensitive information. Good practice requires proper protection of this information using encryption, masking, or tokenization.
8) System and Compliance Logging
A common question asked by auditors is “How do you know who decrypted a credit card number?” Unless your encryption solution has integrated compliance logging, you may not know who is viewing sensitive data in your database systems. Compliance logging is often overlooked by vendors of encryption systems, leaving companies perplexed in the event of a data loss. Townsend Security offers Alliance LogAgent for the IBM i or Syslog-ng as both an application or appliance.
9) Key Access Controls
Encryption and key management access controls are essential to an encryption strategy. Can you specify who has access to the HR encryption key for payroll processing? The ability to restrict the use of encryption to specific users and groups is an essential security control.
10) Virtual and Cloud Platforms
Encryption and Key Management in VM and Cloud environments pose special challenges. The PCI SSC virtualization group indicates that security concerns are much higher in these environments. Currently there is no standard for implementing key management in the cloud environment.
In conclusion, there are many factors involved when choosing the right encryption and key management solution for your enterprise. Additionally, once chosen, it is also important to make sure that it is implemented correctly. For more reading on encryption and PCI, we have written a white paper titled Encryption Key Management Requirements for PCI.


 Your Encryption Project Just Get Easier!!
Your Encryption Project Just Get Easier!! I invited a partner to come down from Seattle to learn about our key management appliance, Alliance Key Manager. It started innocently enough, we planned to meet on February 21st and discuss our encryption, key management and system logging solutions in the context of PCI compliance. A week later, I received a call from an Australian partner asking to come by our office for training on Feb 21st. They were going to be in Seattle after the RSA Conference. I told them they were in luck, we were coincidentally conducting a training session on that very day, come to our office, we would love to host them.
I invited a partner to come down from Seattle to learn about our key management appliance, Alliance Key Manager. It started innocently enough, we planned to meet on February 21st and discuss our encryption, key management and system logging solutions in the context of PCI compliance. A week later, I received a call from an Australian partner asking to come by our office for training on Feb 21st. They were going to be in Seattle after the RSA Conference. I told them they were in luck, we were coincidentally conducting a training session on that very day, come to our office, we would love to host them.  Townsend Security heartily supports non-profit organizations in our community. So it comes as no surprise that several Townsend Security employees were spotted at the annual United Way “Power of the Purse” fundraiser last week.
Townsend Security heartily supports non-profit organizations in our community. So it comes as no surprise that several Townsend Security employees were spotted at the annual United Way “Power of the Purse” fundraiser last week. It was a great time of year to be in Anaheim, California last week for the IBM System z Mainframe SHARE user conference. The rains had just passed through and the weather was balmy. The Anaheim convention center is right next door to Disneyland, a place that was paradise to me growing up in Southern California. The juxtaposition was not lost on anyone – Mainframes being the really serious computing platform, and Disneyland being the silliest and most fun place on planet Earth. But there was fun at the SHARE conference, too.
It was a great time of year to be in Anaheim, California last week for the IBM System z Mainframe SHARE user conference. The rains had just passed through and the weather was balmy. The Anaheim convention center is right next door to Disneyland, a place that was paradise to me growing up in Southern California. The juxtaposition was not lost on anyone – Mainframes being the really serious computing platform, and Disneyland being the silliest and most fun place on planet Earth. But there was fun at the SHARE conference, too. Now that the new version of the PCI Data Security Standard (PCI DSS version 2.0) is in effect, many IBM i (AS/400, iSeries) customers are getting dinged on their PCI compliance in the area of encryption key management. The renewed focus on "Dual Control" and "Separation of Duties" by QSA auditors is forcing many IBM i customers to move from homegrown key management to a better method of securing keys. This is even happening for IBM i customers who use IBM’s Master Key and key database facility. Why is this? There is just no way to properly implement effective security controls for the QSECOFR user, or for any user with All Object (*ALLOBJ) authority. Thus no "Dual Control" and no "Separation of Duties." And QSA auditors have figured this out.
Now that the new version of the PCI Data Security Standard (PCI DSS version 2.0) is in effect, many IBM i (AS/400, iSeries) customers are getting dinged on their PCI compliance in the area of encryption key management. The renewed focus on "Dual Control" and "Separation of Duties" by QSA auditors is forcing many IBM i customers to move from homegrown key management to a better method of securing keys. This is even happening for IBM i customers who use IBM’s Master Key and key database facility. Why is this? There is just no way to properly implement effective security controls for the QSECOFR user, or for any user with All Object (*ALLOBJ) authority. Thus no "Dual Control" and no "Separation of Duties." And QSA auditors have figured this out.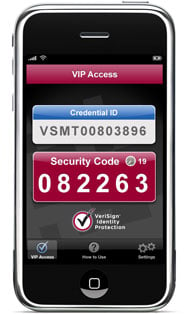 One thing that jumped out at me at this year’s RSA conference in San Francisco was the number of new vendors showing off mobile identification solutions. There were at least four new vendors of mobile-based two factor authentication solutions, and one regular exhibitor with a new entry in this area. These vendors didn’t have the biggest booths or the most lavish give-aways, but as a category they certainly made a big splash.
One thing that jumped out at me at this year’s RSA conference in San Francisco was the number of new vendors showing off mobile identification solutions. There were at least four new vendors of mobile-based two factor authentication solutions, and one regular exhibitor with a new entry in this area. These vendors didn’t have the biggest booths or the most lavish give-aways, but as a category they certainly made a big splash. I just listened to a discussion of database security hosted by Oracle that was very well done. At one point the discussion turned to current threats and how the Enterprise has lost the ability to use perimeter protection for sensitive data. This has been a topic of much discussion in the security area for the last few months. Perimeter protection is based on the use of Firewall and similar technologies to keep the bad guys out, but this approach is failing with the advance of more sophisticated attacks, the use of social media by large organizations, the advance of mobile technologies, insider threats, and the migration of applications to cloud platforms. The trend is called “de-perimeterization” and represents a bit of a challenge to organizations that need to protect sensitive data.
I just listened to a discussion of database security hosted by Oracle that was very well done. At one point the discussion turned to current threats and how the Enterprise has lost the ability to use perimeter protection for sensitive data. This has been a topic of much discussion in the security area for the last few months. Perimeter protection is based on the use of Firewall and similar technologies to keep the bad guys out, but this approach is failing with the advance of more sophisticated attacks, the use of social media by large organizations, the advance of mobile technologies, insider threats, and the migration of applications to cloud platforms. The trend is called “de-perimeterization” and represents a bit of a challenge to organizations that need to protect sensitive data. As day three of the RSA Conference 2011 begins, it marks the half-way point through the largest data security tradeshow that the industry has to offer. Walking into the show you would be hard pressed to tell whether you walked into a security show or a grown up play-yard. Look to left you see sumo wrestlers, looking ahead there are unicycles weaving the crowd, and to the right are pirates handing out candy. And to top it all off, each night ends with beer, wine, and appetizers for all attendees. Who wouldn’t want to attend the RSA Conference 2011??!!
As day three of the RSA Conference 2011 begins, it marks the half-way point through the largest data security tradeshow that the industry has to offer. Walking into the show you would be hard pressed to tell whether you walked into a security show or a grown up play-yard. Look to left you see sumo wrestlers, looking ahead there are unicycles weaving the crowd, and to the right are pirates handing out candy. And to top it all off, each night ends with beer, wine, and appetizers for all attendees. Who wouldn’t want to attend the RSA Conference 2011??!!