 One thing that jumped out at me at this year’s RSA conference in San Francisco was the number of new vendors showing off mobile identification solutions. There were at least four new vendors of mobile-based two factor authentication solutions, and one regular exhibitor with a new entry in this area. These vendors didn’t have the biggest booths or the most lavish give-aways, but as a category they certainly made a big splash.
One thing that jumped out at me at this year’s RSA conference in San Francisco was the number of new vendors showing off mobile identification solutions. There were at least four new vendors of mobile-based two factor authentication solutions, and one regular exhibitor with a new entry in this area. These vendors didn’t have the biggest booths or the most lavish give-aways, but as a category they certainly made a big splash.
I think there are really two things responsible for this big change: Two factor authentication is now more important for security, and everyone now carries a cell phone or mobile device. The second part of this is completely obvious. In fact, I often see people carrying multiple cell phones. The ubiquity of the cell phone makes them an ideal platform to deliver a one-time password or PIN code. And phone numbers are a lot easier to manage than hardware tokens.
The first part of this, the change in the security landscape, is not as well known to many people. As we’ve moved to a de-perimeterized security reality, we are more dependent on passwords to authenticate the users of our systems. And security professionals know how weak that dependence is. People who access our systems persist in the use of weak passwords, and the bad guys get better and better at password cracking and harvesting. By itself, password authentication is a poor defense, and that’s why two factor authentication is getting a lot of attention.
So what is two factor authentication? It means that you use two different authentication methods to access a system. Those authentication methods include:
• Something you know (like a password or PIN code)
• Something you are (fingerprint, iris)
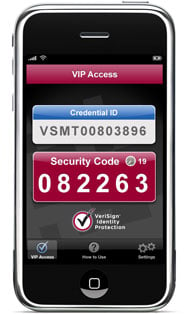
• Something you have (cell phone, HID card, hardware token)
By combining two of these authentication methods during system access you greatly reduce the chance of a security breach. For web applications, you generally find the use of a password with a PIN code generated with a hardware token (something you know, something you have), because it really hard to use a fingerprint reader or iris scanning device (something you are). And that’s why cell phone based two factor authentication is picking up steam.
Don’t be confused by security systems that use one factor twice. I’m sure you’ve seen it at work on banking web sites. First you enter a password, then you answer a personal question (where were you born, the age of your oldest child, etc.). This is one factor authentication (something you know) used twice. This is when 2 times 1 is not equal to 2. The use of one factor authentication twice does not add up to two factor authentication, and does not provide the same level of security.
Cell phones and mobile devices are a great way to deliver that second authentication factor. You have to have your cell phone to get the one time PIN code used for authentication. And everyone has one.
For more information on data security and compliance issues, visit the regulatory compliance section of our website to learn more.
Patrick
