VMware has become the most trusted name in on-premise computing infrastructure. Because of its ease of use and administration, reliability and security, VMware is able to provide exceptional services to small and large organizations alike. As these organizations move to the cloud, VMware hosting partners and managed service providers (MSPs) are able to service this market by providing off-premise deployments of VMware and an extensive array of VMware management and administrative services. For more information on how VMware hosting providers can better secure customer data, check out our "Definitive Guide - Encryption Key Management for VMware Cloud Providers" page.
 I recently sat down with Patrick Townsend, Founder and CEO of Townsend Security, to talk about how Townsend Security is helping VMware hosting providers meet the challenge of encryption and encryption key management, while supporting the usage-based business model core to many of these hosting providers. Additionally, Patrick discussed VMware architecture, VMware security, delivering compelling hosting & services, and compliance, standards, and encryption.
I recently sat down with Patrick Townsend, Founder and CEO of Townsend Security, to talk about how Townsend Security is helping VMware hosting providers meet the challenge of encryption and encryption key management, while supporting the usage-based business model core to many of these hosting providers. Additionally, Patrick discussed VMware architecture, VMware security, delivering compelling hosting & services, and compliance, standards, and encryption.
Hi Patrick. In recent years VMware has embraced the movement to the cloud with key partnerships with leading cloud service providers. What is less well known is that VMware has spawned and supports a broad set of hosting providers that serve local and regional markets. These VMware hosting providers also provide the expertise and managed services that many large cloud providers do not.
There are a fair number of VMware hosting providers and MSPs now with their own hosted, or cloud, platforms who are running VMware full stack implementations for their customers. Customers now have many options for managing their VMware infrastructure on premise or at a VMware hosting provider data center. Many of these customers maintain both on-premise and hosted environments to meet their customers’ business needs. The VMware ecosystem is growing and resilient, and an important part of the IT services landscape.
Security has got to be essential for these hosting providers and MSPs. What do you think they are doing well and where could they use a little help?
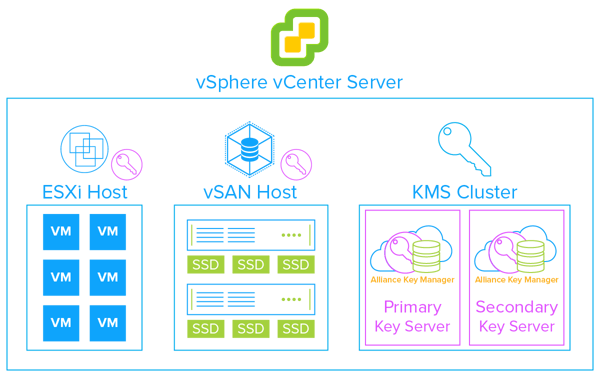
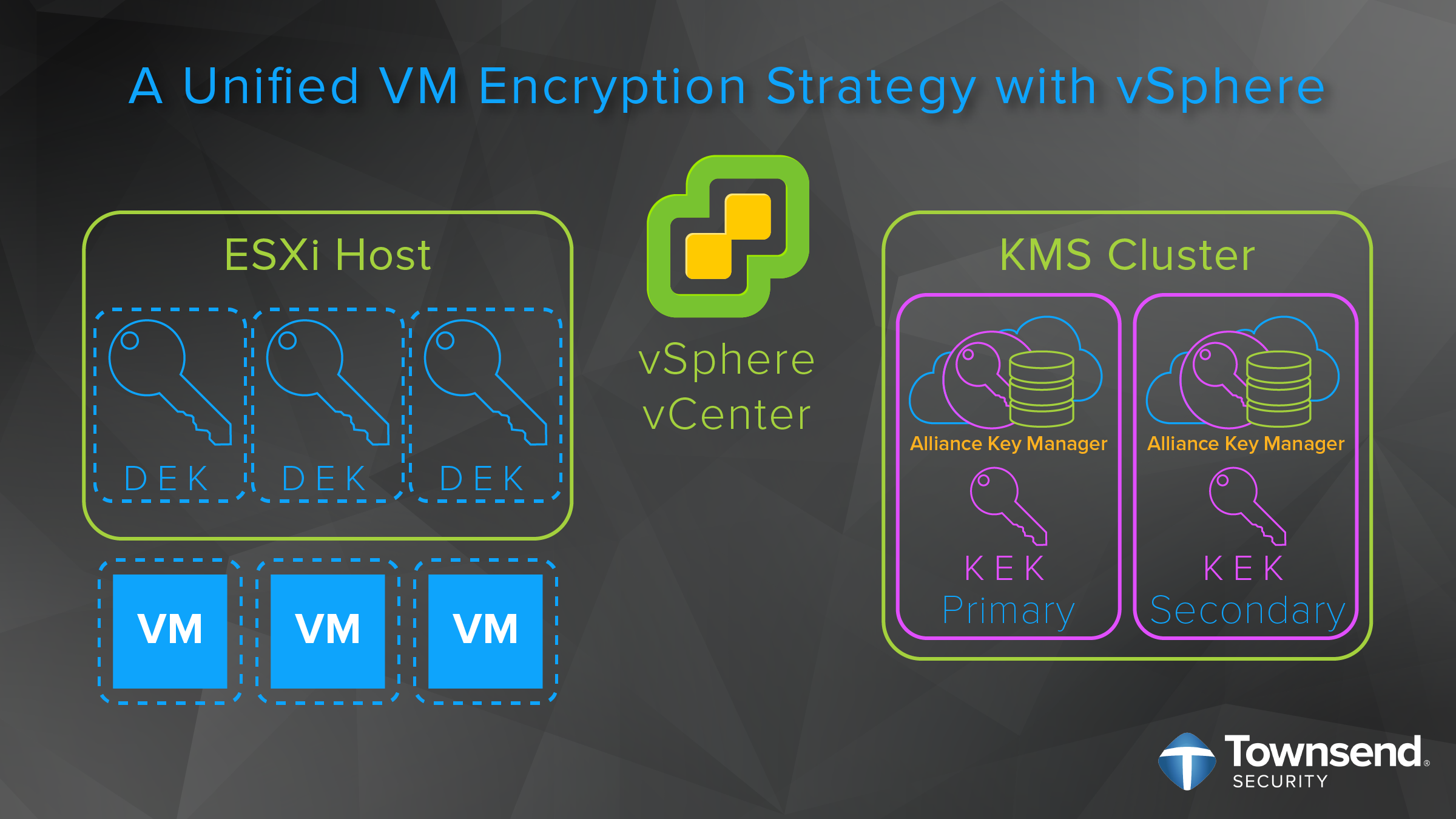
Well, security is a core focus of VMware applications, and the security features have had a lot of time to mature. For example, VMware now offers encryption in several of their products. However, the deployment of proper encryption relies on support from third party KMS vendors. Realizing the importance of key management, VMware adopted the Key Management Interoperability Protocol (KMIP) standard, which allows vendors like Townsend Security to provide key management solutions that allow businesses to store and manage their encryption keys through their entire lifecycle.
Townsend Security is proud to help VMware hosting providers and MSPs implement encryption and do it the right way that matches their business model.
So, let’s spend a minute and discuss delivering compelling hosting and services.
VMware hosting providers and MSPs are rapidly changing the way that VMware customers are managing their IT infrastructure. These VMware partners are filling a services and support gap left by typical, large cloud service providers. Hosted VMware infrastructure, Disaster Recovery as a Service (DRaaS), automated backup and recovery, and expertise on demand provide compelling value to VMware end customers. Amazingly, many of these VMware hosting partners are providing a far more affordable solution than large Cloud Service Providers. Townsend Security’s Alliance Key Manager is filling the KMS gap for VMware hosting providers and MSPs by providing an Enterprise KMS system that matches the way they do business. Gone are the complexities of sourcing, deploying, licensing and administering a KMS for the VMware environment. Townsend Security empowers the VMware hosting provider with on-premise and customer premise solutions for every VMware KMS need.
There are a few strategies that these hosting providers and MSPs can use to secure customer data in VMware environments. For example, data can still reside on-premises or in the cloud and be encrypted in VMs or in vSAN, or even through Virtual Trusted Platform Module (vTPM). First, let’s cover On-Prem and the Cloud.
Sure. Many VMware hosting providers and MSPs often are the experts who manage a customer’s on-premise VMware infrastructure. If you don’t have in-house expertise these partners can step up to help you. This means that the same security tools that are used at the hosting site need to be available at the customer site. This is a core part of the value that a VMware hosting provider and MSP provides to their customers - run VMware on-premise, on their cloud, or combine the two. Some VMware MSPs provide expertise and services to help their customers move to one of the larger cloud platforms.
If you are a VMware hosting provider and you provide this type of service to help customers move to Microsoft Azure VMware Solution, Google VMware Cloud Engine, or IBM Cloud for VMware, or other full-stack VMware cloud service, we can help you with your KMS needs in the same way.
Let’s circle back to how data is being encrypted in VMware
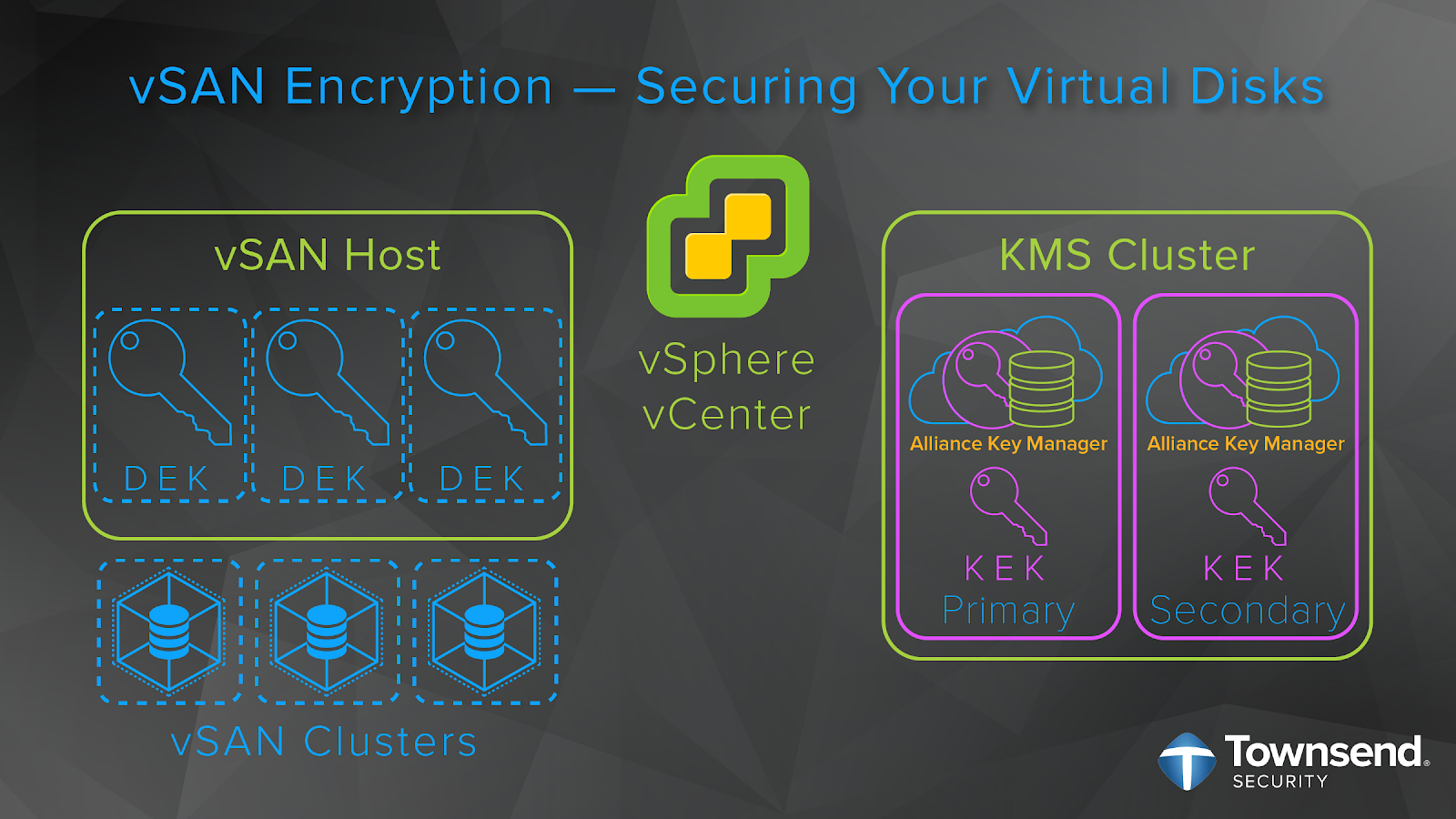
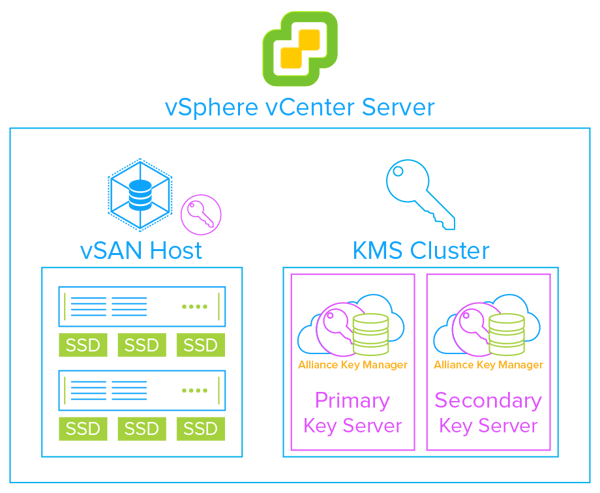
As a VMware hosting provider or MSP, you are able to quickly and easily deploy encryption of VMs for your customers with vSphere encryption. It is important to not forget about also deploying a KMS. The second most popular encryption option in a VMware environment is the encryption of vSAN virtual directories. The VMware architecture for key management for vSAN is the same vSphere KMS cluster configuration used for encrypting VMs. Encryption of vSAN storage is one of the great ways to protect databases in the VMware infrastructure. It can be expensive to upgrade Oracle, SQL Server or MongoDB to get encryption support, but you can easily provide encryption at rest by deploying these databases on encrypted vSAN storage at a fraction of the cost of an upgrade. And you can do encryption at rest for open source databases that do not directly implement encryption or proper key management. This includes MariaDB, PostgreSQL, SQLite and others.
Another option is to use OS encryption through the virtual trusted platform module (vTPM), right?
The Trusted Platform Module (TPM) chip is implemented on many Intel architecture servers and provides an additional level of encryption key protection in traditional server environments. Unfortunately, the TPM architecture works poorly in a VMware environment where workloads can move and migrate between servers. Thankfully, VMware came to the rescue with Virtual TPM (vTPM)! By installing the appropriate vTPM drivers from VMware you can achieve TPM security that works natively with your VMware platform. vTPM also leverages the same vSphere KMS interface, so encryption and proper key management are easy to deploy.
How is Townsend Security helping VMware hosting providers and MSPs with encryption and key management?
Townsend Security has been a VMware partner for many years. Our KMS, Alliance Key Manager, is certified by VMware on all releases of vSphere and vSAN that support encryption. At Townsend Security we have worked hard to create a hosting provider/MSP program that takes the pain out of a KMS partnership. Most notably, if you provide VMware hosting services on a usage-based model, we will help you deliver a KMS for encrypted VMs and vSAN with the same model. For example, if you are charging your customers per virtual machine or per main memory, depending on how much you use, we will snap right in to your environment and help you deliver encryption of VMs and vSAN in the same way.We do this with no upfront fees, no annual license charges or separate maintenance fees, we just make it really simple to deploy and use for the VMware hosting provider.
Is there anything else that you would like to share about your partner program?
First, it is very easy and simple to get started with our partner program. Just visit www.townsendsecurity.com/msp. If you are interested in more information, there is a short form to fill out. We make it extremely cost effective for hosting providers to deploy encryption and key management for their customers. I’d also like to mention that our KMS is certified for every version of vSphere and vSAN that support encryption, is validated for PCI-DSS compliance, and has been through a FIPS 140-2 validation.
You can actually download Alliance Key Manager for VMware directly from our website and immediately load it into VMware. We also have our support team ready to help you get deployed - without a charge. It just takes minutes. We are proud to have lowered the barrier to entry and administrative overhead typically associated with encryption key management - which makes it easier than ever for VMware hosting providers and MSPs to offer better security to their customers.
To hear this conversation in its entirety, download the podcast “Delivering Secure VMware Hosting with Encryption & Key Management” to hear Patrick Townsend, Founder and CEO, further discuss VMware architecture, VMware security, delivering compelling hosting & services, and compliance, standards, and encryption.














![[Podcast] Don't Let Your Application or Database Limit Your Encryption Strategy](https://no-cache.hubspot.com/cta/default/15891/cc299bb8-69c0-431c-9461-d688c516a1b3.png)