 Data Privacy Day (January 28, annually) is an annual international celebration designed to encourage awareness about privacy and education on best privacy practices. Sponsored by companies such as Intel, eBay, and Google, the day is designed to promote awareness on the many ways personal information is collected, stored, used, and shared, as well as education about privacy practices that will enable individuals to protect their personal information.
Data Privacy Day (January 28, annually) is an annual international celebration designed to encourage awareness about privacy and education on best privacy practices. Sponsored by companies such as Intel, eBay, and Google, the day is designed to promote awareness on the many ways personal information is collected, stored, used, and shared, as well as education about privacy practices that will enable individuals to protect their personal information.
As a data privacy company, this day is almost like our birthday – a day for the IT world to focus on our slice of the pie (can we celebrate Data Privacy Day with pie too?). It also is a time to reflect on some of the data breaches that made news headlines in the previous year – “is my organization making some of the same mistakes?”
In honor of Data Privacy Day, StaySafeOnline.org has published a document titled “Stop. Think. Connect” that gives tips and advice on keeping your personal information safe. Here is some of their advice:
Protect Your Personal Information
- Secure your accounts: Ask for protection beyond passwords. Many account providers now offer additional ways for you verify who you are before you conduct business on that site.
- Make passwords long and strong: Combine capital and lowercase letters with numbers and symbols to create a more secure password.
Connect with Care
- Get savvy about Wi-Fi hotspots: Limit the type of business you conduct and adjust the security settings on your device to limit who can access your machine.
- Protect your $$: When banking and shopping, check to be sure the sites is security enabled. Look for web addresses with “https://” or “shttp://”, which means the site takes extra measures to help secure your information. “http://” is not secure.
Keep a Clean Machine
- Keep security software current: Having the latest security software, web browser, and operating system are the best defenses against viruses, malware, and other online threats.
- Automate software updates: Many software programs will automatically connect and update to defend against known risks. Turn on automatic updates if that’s an available option.
By following these few tips your personal information/data will be more secure than ever. We also urge you to think about who you give your personal information. Do you think twice about whether it is being properly protected?
For more information on data privacy, download our podcast Data Privacy for the Non-Technical Person. Patrick Townsend, our Founder & CTO, discusses what PII (personally identifiable information) is, what the most effective methods for protecting PII, as well as the first steps your company should take towards establishing a data privacy strategy.


 During our monthly webinars we receive some great questions that we like to share with our blog readers. Our most recent webinar titled “
During our monthly webinars we receive some great questions that we like to share with our blog readers. Our most recent webinar titled “
 Meeting compliance regulations on your IBM i for securing data in motion doesn’t need to be difficult. They all have the same overlying theme – encryption. PCI DSS requires encryption when transferring files over the internet and WiFi networks. HIPAA/HITECH says that encryption is the only Safe Harbor from a data breach. While failing to comply with these regulations can financially impact your organization, the good news is that with just a few core encryption components, you can easily satisfy these requirements.
Meeting compliance regulations on your IBM i for securing data in motion doesn’t need to be difficult. They all have the same overlying theme – encryption. PCI DSS requires encryption when transferring files over the internet and WiFi networks. HIPAA/HITECH says that encryption is the only Safe Harbor from a data breach. While failing to comply with these regulations can financially impact your organization, the good news is that with just a few core encryption components, you can easily satisfy these requirements.
 As the social revolution moves into the business world, protecting your data is more important than ever. This was a key takeaway for attendees of the recent “Dreamforce to You” event in Seattle, WA, hosted by Salesforce.
As the social revolution moves into the business world, protecting your data is more important than ever. This was a key takeaway for attendees of the recent “Dreamforce to You” event in Seattle, WA, hosted by Salesforce. We couldn’t agree more. As a security company, this is something we have been saying since the beginning. We have offered NIST-validated AES encryption for all the major enterprise platforms for over ten years, been securing managed file transfers with PGP encryption, and recently stepped up our game with a FIPS 140-2 compliant encryption key management HSM. Simply put, we are helping organizations protect their sensitive information and meet compliance regulations with certified encryption solutions.
We couldn’t agree more. As a security company, this is something we have been saying since the beginning. We have offered NIST-validated AES encryption for all the major enterprise platforms for over ten years, been securing managed file transfers with PGP encryption, and recently stepped up our game with a FIPS 140-2 compliant encryption key management HSM. Simply put, we are helping organizations protect their sensitive information and meet compliance regulations with certified encryption solutions.
 AES Encryption
AES Encryption 
 I’ve been writing about encryption performance lately because our customers and potential customers have been asking about the impact of encryption on the overall performance on their systems. It’s good that they are asking these questions as a poorly performing encryption library can have severe impact on your application environment. This is especially true on an IBM Enterprise platform like the IBM i (formerly known as AS/400 and iSeries) where customers often run multiple applications.
I’ve been writing about encryption performance lately because our customers and potential customers have been asking about the impact of encryption on the overall performance on their systems. It’s good that they are asking these questions as a poorly performing encryption library can have severe impact on your application environment. This is especially true on an IBM Enterprise platform like the IBM i (formerly known as AS/400 and iSeries) where customers often run multiple applications.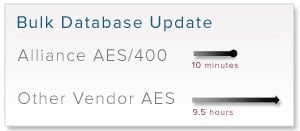 We did a simple little comparison test of encrypting 1 million credit card numbers on an entry level IBM i model 515 server with a single processor. We compared the native IBM AES library with our own AES encryption library which is NIST certified and optimized for encryption. The difference is very large. Our IBM i encryption library clocked in at 116 times faster than the native IBM i library. Note that this is an informal test and not independently verified, but practical experience by our customers is very similar.
We did a simple little comparison test of encrypting 1 million credit card numbers on an entry level IBM i model 515 server with a single processor. We compared the native IBM AES library with our own AES encryption library which is NIST certified and optimized for encryption. The difference is very large. Our IBM i encryption library clocked in at 116 times faster than the native IBM i library. Note that this is an informal test and not independently verified, but practical experience by our customers is very similar.
 Recently, Townsend Security hosted a donation drive for the YWCA’s “The Other Bank”. The Other Bank provides items to low income families in Thurston County, where Townsend Security is headquartered. They collect a variety of things to help families in need - for example; diapers, toilet paper, dish soap, deodorant, etc. From the The Other Bank’s website:
Recently, Townsend Security hosted a donation drive for the YWCA’s “The Other Bank”. The Other Bank provides items to low income families in Thurston County, where Townsend Security is headquartered. They collect a variety of things to help families in need - for example; diapers, toilet paper, dish soap, deodorant, etc. From the The Other Bank’s website: Without organizations like The Other Bank, there are a lot of people that would go without. In an earlier blog post this year, I mentioned how great it is to work at a company where the community is so important. It is great to work at a company that not only says they want to make their community better - they actually do it and encourage all of its employees to do the same. Working at Townsend Security has inspired me to be a volunteer at the YWCA and I have put in over 20 hours these past few weeks.
Without organizations like The Other Bank, there are a lot of people that would go without. In an earlier blog post this year, I mentioned how great it is to work at a company where the community is so important. It is great to work at a company that not only says they want to make their community better - they actually do it and encourage all of its employees to do the same. Working at Townsend Security has inspired me to be a volunteer at the YWCA and I have put in over 20 hours these past few weeks. I recently attended a webinar for accountants on the importance of IT security. The webinar discussed findings from the newly released 2012 Global State of Information Security Survey®, a worldwide study conducted by Pricewaterhouse Coopers, CIO Magazine and CSO Magazine. They used the information from the survey to make two important points
I recently attended a webinar for accountants on the importance of IT security. The webinar discussed findings from the newly released 2012 Global State of Information Security Survey®, a worldwide study conducted by Pricewaterhouse Coopers, CIO Magazine and CSO Magazine. They used the information from the survey to make two important points Periodically people ask me about hashes and why the use of a salt value with a hash is recommended. Let’s have a look at this topic in our last blog for 2011!
Periodically people ask me about hashes and why the use of a salt value with a hash is recommended. Let’s have a look at this topic in our last blog for 2011! Well, take the example of your banking PIN code. It might be 4 or 5 digits in length. From the point of view of modern computers, that is a really small set of numbers to test against a SHA-256 algorithm. Only 9,999 values for a 4-digit banking PIN code. That is going to take less that a second to run through all of the possibilities. So this is where a salt value can come in handy. If you are creating a hash value of very small bit of data, you can append a salt value to the original data and make it really hard to attack that hash value. And that’s why using salt with your hashes is often a recommended security practice.
Well, take the example of your banking PIN code. It might be 4 or 5 digits in length. From the point of view of modern computers, that is a really small set of numbers to test against a SHA-256 algorithm. Only 9,999 values for a 4-digit banking PIN code. That is going to take less that a second to run through all of the possibilities. So this is where a salt value can come in handy. If you are creating a hash value of very small bit of data, you can append a salt value to the original data and make it really hard to attack that hash value. And that’s why using salt with your hashes is often a recommended security practice.


 At Townsend, we have a lot of conversations with customers and prospects about data privacy, compliance requirements and best practices for IT security in general. We have written numerous articles on these topics and posted them on our blog. As the end of 2011 quickly approaches, we thought it would be worthwhile to list out our most read articles of the year.
At Townsend, we have a lot of conversations with customers and prospects about data privacy, compliance requirements and best practices for IT security in general. We have written numerous articles on these topics and posted them on our blog. As the end of 2011 quickly approaches, we thought it would be worthwhile to list out our most read articles of the year.