 While FIELDPROC was introduced nearly two years ago with IBM i V7R1, it is becoming new to administrators who are finally upgrading to the latest IBM i OS. Lucky for you newbies, we have plenty of experience with this release and can share a wealth of knowledge for your encryption project. FIELDPROC allows us to bring you automatic encryption – encryption with no application changes! We recently hosted a webinar titled “Automatic Encryption on the IBM i” and received some great questions. Patrick Townsend, Founder & CTO, recently took some time to answer a few questions that we received during the webinar. If you have any further questions on FIELDPROC and how your organization can implement automatic encryption with no application changes, send them our way.
While FIELDPROC was introduced nearly two years ago with IBM i V7R1, it is becoming new to administrators who are finally upgrading to the latest IBM i OS. Lucky for you newbies, we have plenty of experience with this release and can share a wealth of knowledge for your encryption project. FIELDPROC allows us to bring you automatic encryption – encryption with no application changes! We recently hosted a webinar titled “Automatic Encryption on the IBM i” and received some great questions. Patrick Townsend, Founder & CTO, recently took some time to answer a few questions that we received during the webinar. If you have any further questions on FIELDPROC and how your organization can implement automatic encryption with no application changes, send them our way.
When you back up encrypted data to tape, does it back it up un-encrypted?
No. Data that is encrypted by FIELDPROC, when you do a backup, is going to be encrypted on the backup tape. If you a put a file under FIELDPROC control and you back it up, you can then just dump that tape and see that the data is encrypted on the tape. Backup operations do not trigger FIELDPROC decryption and you can securely back up a file on to tape for it to be protected. That is a part of the built-in capabilities within FIELDPROC. However, if you copy a file with the “copy” command, the database WILL trigger FIELDPROC and decrypt that data.
Can masking be done by group profile or only by a specific user?
Good question. Yes, you can use group profiles for user access controls and masking. We understand that a lot of our customers have a large number of users and have leveraged using group profiles. We fully support group profiles around both access controls and masking. It is important to note that we do not use native object authority for our user access controls and masking. Instead we use a white-list approach that allows you to control and monitor QSECOFR and any user with All Object (*ALLOBJ) authority.
Are there any performance impacts of using encrypted data as indexes, as far as reads or chains, or other I/O functions?
IBM has done a great job of implementing FIELDPROC in terms of how it gets called and when it gets called. There is no particular performance impact for reads, as opposed to writes. We have done tests with encryption and decryption and they are both very efficient and very effective. There is a tiny measureable difference between encryption and decryption, and that has to do with key scheduling, but believe me, it is extremely insignificant. I think you will find about equivalent performance with both encryption and decryption.
View our webinar “Automatic Encryption on the IBM i” for more information about FIELDPROC and how your organization can easily meet compliance regulations that require encryption – with no application changes!


 Last week we hosted a webinar titled “
Last week we hosted a webinar titled “




 Townsend Security hosts a monthly webinar on a wide variety of topics ranging from
Townsend Security hosts a monthly webinar on a wide variety of topics ranging from 

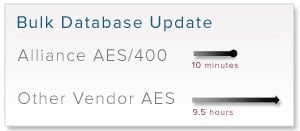 I think this is a pretty good baseline of minimum performance our customers will see with our
I think this is a pretty good baseline of minimum performance our customers will see with our 