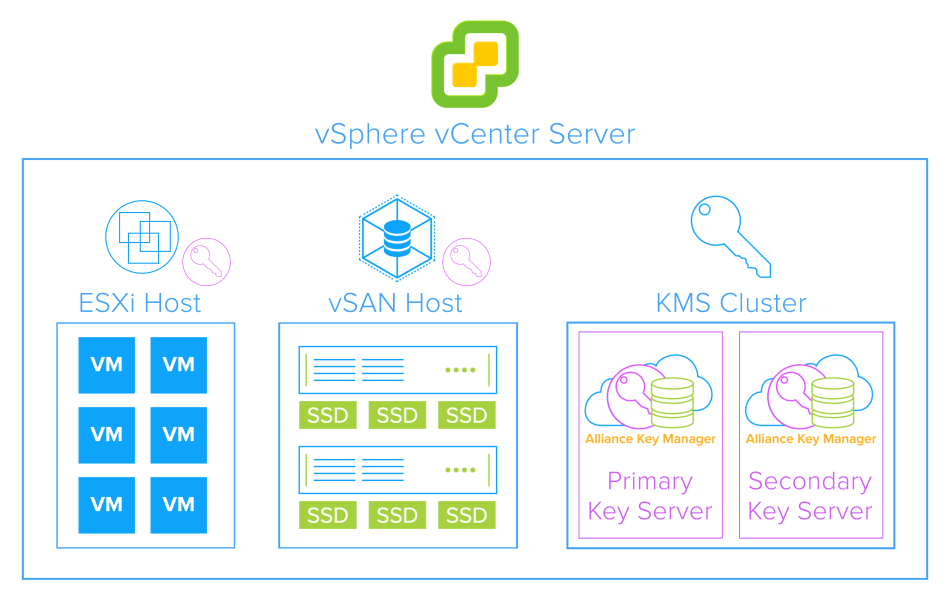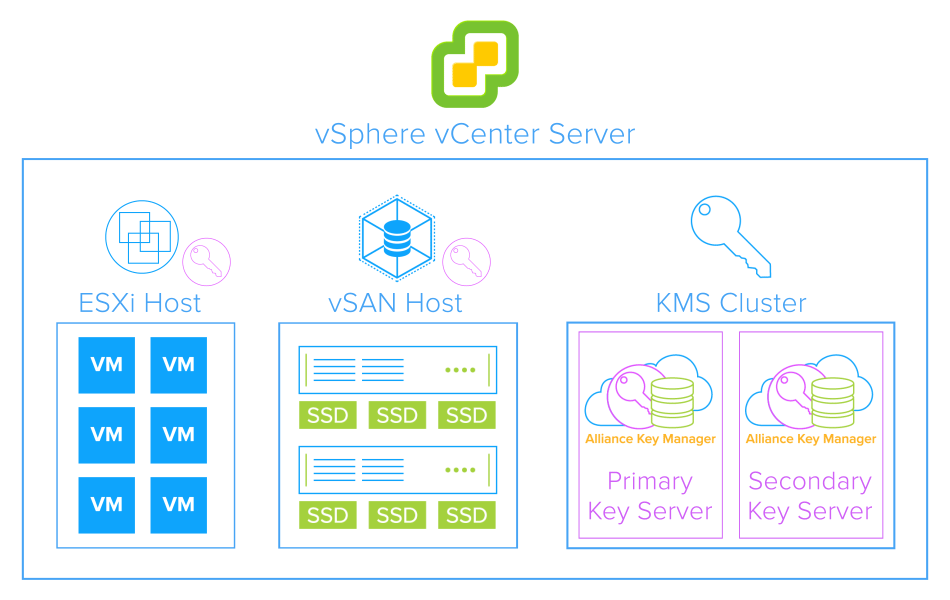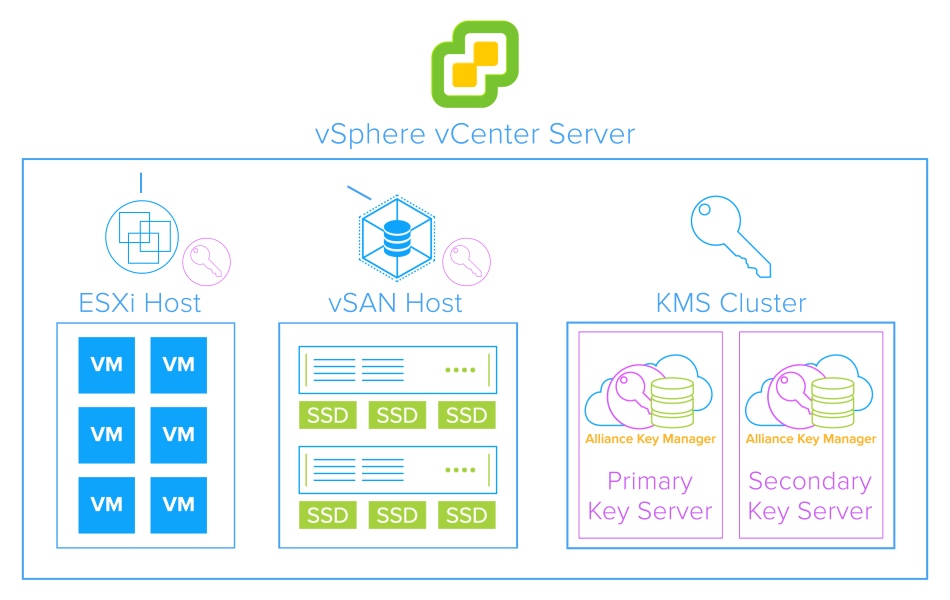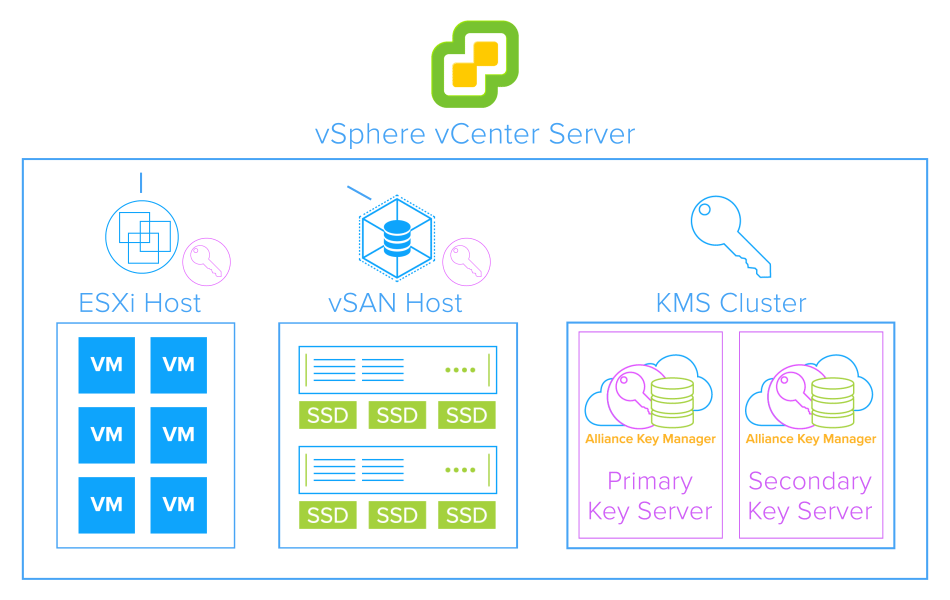
For applications that require the highest level of security, developers can use the on-board, NIST-compliant encryption and decryption services on Alliance Key Manager, rather than encrypting at the application or database level. Under this strategy, encryption keys never leave the key manager. With on-board encryption services, small chunks of data, such as credit card numbers, Social Security numbers, e-mail addresses, etc are encrypted on the server (physical HSM, VMware, or virtual appliance in the cloud). Because data is securely transferred to the key manager for encryption, it is recommended for smaller amounts of data. For larger amounts of data, it is still recommended to encrypt at the database or application level.
Using an Encryption Service
Businesses can use onboard encryption effectively to improve their security posture and reduce their attack surface. This strategy is helpful in situations where they don’t want to expose the encryption key in their application or server environment. For businesses who have their data in the cloud, this also alleviates the risk of exposure of the encryption key in cloud memory.
Encryption Service Performance
The performance of an encryption service is one of the biggest concerns that businesses have when taking this approach to protecting data. To shed some light on these concerns, we did some testing using our Java SDK on small blobs (<16KB) and with our .NET Key Client for large blobs.
Small Blob Performance
Quant. | avg enc/dec | avg rate
< 1KB | 48ms | 21 ops/sec
3KB | 50ms | 20 ops/sec
5KB | 51ms | 20 ops/sec
7KB | 52ms | 19 ops/sec
10KB | 53ms | 19 ops/sec
16KB | 55ms | 18 ops/sec
As a general metric, it is fair to say that for small pieces of data, the average latency for AES encryption (using CBC mode) is 50ms, yielding a rate of 20 operations per second.
Large Blob Performance
The results of testing with the .NET Key Client for large blob:
Quant | Avg. enc. time
1MB | 462 ms
2MB | 535 ms
5MB | 949 ms
7MB | 1.16 s
10MB | 1.74 s
15MB | 2.34 s
25MB | 3.61 s
50MB | 7.60 s
70MB | 10.65 s
This can be represented as a graph:
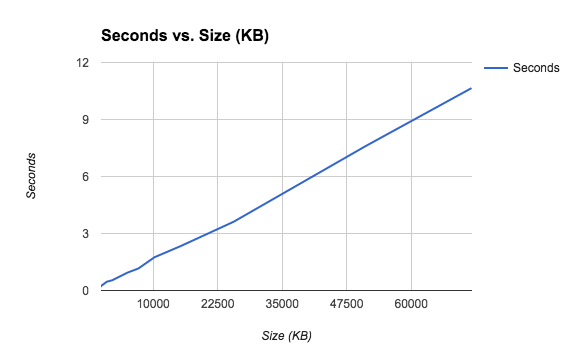
Taking this data and calculating the rate at which Alliance Key Manager is encrypting data, we were able to generate this graph:
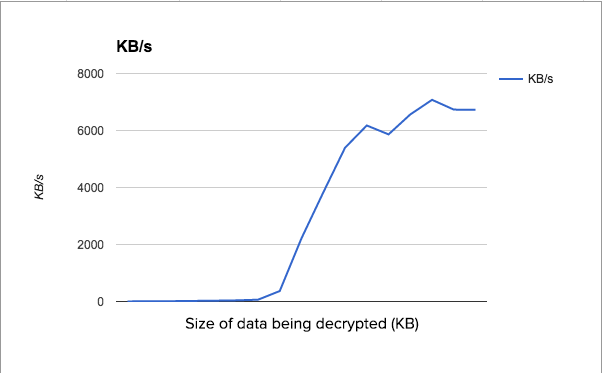
The horizontal axis is the size of the data being encrypted--the larger the file, the more likely it will approach maximum speed. For encrypting small pieces of data, the process of establishing a connection to Alliance Key Manager and sending the data vastly outweighs the actual encryption, so the rate shows as very low. It spikes up to about 6.5 MB/s when the size of the data is around 5MB--larger than that, and the time to encrypt can be predicted using that rate.
The major take-away: encrypting large blobs on AKM using the .NET Key Client occurs at a rate of 6.5MB/s. It is likely that the Java SDK, and other SDKs, would have about the same level of performance. This data was compiled on an AKM with 1CPU and 2GB of memory. Doubling those resources yields a small increase in performance--up to 6.9 MB/s .
Conclusion
While there are performance impacts when encrypting large amounts of data with an encryption service (as opposed to encrypting an entire database or column within), it does provide improved security on smaller amounts of data for business wanting to minimize their encryption key exposure. Further, by utilizing Townsend Security’s encryption service, businesses can have confidence that they are protecting their data with NIST-compliant AES encryption. NIST compliance means that the encryption implementation has been reviewed by an independent testing lab who reports the results to NIST for validation.






 Secrets Management SaaS for CMS Systems Including Drupal and WordPress
Secrets Management SaaS for CMS Systems Including Drupal and WordPress

 Securing Data in MongoDB Enterprise with Alliance Key Manager
Securing Data in MongoDB Enterprise with Alliance Key Manager

 Meeting PCI DSS with Townsend Security's Alliance Key Manager Hardware Security Module (HSM)
Meeting PCI DSS with Townsend Security's Alliance Key Manager Hardware Security Module (HSM)

 Compliance Made Easy - Protecting Private Information with Alliance AES/400 Encryption for IBM i and Alliance Key Manager for VMware
Compliance Made Easy - Protecting Private Information with Alliance AES/400 Encryption for IBM i and Alliance Key Manager for VMware


