As the world of edge computing becomes more distributed, billions of connected devices live on the edge, which need to be secured, managed and automated. For many businesses, this means deploying a VMware and cloud infrastructure and using VMware vSphere, for example, to encrypt private information. While it is easy enough to encrypt data on the edge, key management has proven to be a challenge.
 I recently sat down with Patrick Townsend, Founder and CEO of Townsend Security to talk about deployments on the edge, achieving a strong security posture with key management, and other ways that businesses can better secure their private data.
I recently sat down with Patrick Townsend, Founder and CEO of Townsend Security to talk about deployments on the edge, achieving a strong security posture with key management, and other ways that businesses can better secure their private data.
Patrick, Townsend Security has had key management solutions for VMware for a number of years. What is special about Edge computing?
Well, Edge computing is fascinating. It isn’t really that different from how we currently think about computing and data security in the cloud or on-premise. By moving applications closer to the end user, Edge computing brings a better, faster user experience to the end user. So, if you are running an application in the cloud, perhaps in a retail or healthcare environment, the delay over the network can degrade the experience or inhibit the ability to collect a lot of data, for example, from IoT devices. Edge computing is a natural evolution of making things more efficient with a better user experience. However, Edge computing also brings new security challenges too. If we are collecting data that is sensitive in nature, it is just as sensitive out on the Edge as it is in our data center.
So what is special or different about Edge computing from a security point of view?
There are a number of challenges. How do we deploy applications in a secure way? How do we do application patching? One of the most important security efforts that we make is to keep everything patched and up to date. When you have Edge computing, there are a lot more environments in distant locations. The security process really becomes more complex when we move to Edge computing. Those challenges can be solved, but they represent things that we really need to pay attention to.
At the same time, as we are pushing applications out to the Edge, compliance regulations are getting more stringent. Just look at the California Consumer Privacy Act (CCPA) and GDPR before it. Both of those are making the protection of sensitive data much more important. The risks of data loss to an organization are escalating, and at the same time, we are pushing data to more and more places - so we have a big security challenge that we need to step up to.
Protecting data data in a centralized IT data center is a challenge, but one that we are used to. Edge computing brings unique problems with it. For example, let’s say you pushed some data out to a dozen Edge computing environments. You’ll need to encrypt that data to meet compliance, but where is the key manager? Is it back at your central on-site data center? If so, you may have just lost the advantage of pushing everything to the Edge. Encryption and key management also need to be pushed out to the Edge in order to meet security best practices, just as you would in on-premise environments.
In terms of the cloud, can you give some examples of Edge environments?
Sure. In the Cloud, we try to deploy applications close to the end-customer which gives us better response times and a better customer experience. So, in AWS or Azure, we can move applications closer to where the end-customer lives. CSPs are making this easier by automating some of the deployment tasks. By pushing applications to the Edge, you get really close to the physical location of the customer. For example, if you live in Sweden, you don’t need to connect to a key manager that is sitting back in Silicon Valley. You should connect to a key manager that is near you. When moving to the Edge, encryption and key management need to move with you.
By the way, you may have noticed that VMware has been working much more closely with Cloud Service Providers to provide true VMware infrastructure on cloud platforms. For example, on Azure, you can deploy a full bare metal stack - VMware in the cloud and managed the way you want. But again, when you push those VMware environments to the Edge, what about the encryption key management? The good news is, that with our new Alliance Key Manager for Edge Computing, we can make that easy and affordable to accomplish.
How about some examples of non-Cloud Edge environments?
Almost all of us use VMware on premise, and it isn’t really all that different to what we are currently doing. Think of a medium or large retail organization with hundreds or thousands of storefronts. When you walk into the store, there is a very good chance that there is a local VMware node out there that is running many applications. Think about a large box store with retail, pharmacy, and automobile services. The VMware environment in a single store might support dozens or hundreds of specialized applications. How do you protect data in that environment? Sometimes when we think of Edge computing we think of “just” the cloud, but this isn’t the case. Again, just like with the Cloud, it doesn’t need to be difficult to push encryption and key management to the Edge, it just needs to get done.
How do compliance requirements impact Edge computing?
Well, compliance requirements, which are getting stronger as we speak, make the challenge of Edge computing even more important to address. If you think about it, when we have centralized IT processing, we have one environment to protect. It may be a very data rich environment with sensitive data that cybercriminals may want to steal - but it something that isn’t that difficult to protect. What if we have 500 of those environments out there across on-prem and cloud locations? The attack surface has been dramatically increased. The data is still important and still a target, but now we have a lot more to deal with. I think people are waking up to the security challenge and need to focus just as much effort on securing data at the Edge as we do at the centralized, on-premise data center. We have to deploy all of our security defenses at the Edge in the same way that we do with core IT systems. The data is the same.
How is Townsend Security trying to help resolve this challenge.
The barriers to getting Edge data protection right are only party technical. Key management vendors have not adapted to the new reality of the Edge. The huge expense of traditional KMS solutions is the primary barrier to protecting data at the Edge. For small businesses, they can even be completely priced out of the market around doing encryption and key management right. Large organizations have been priced out as well. When there are hundreds or thousands of endpoints that need protected, vendors need to step up to help these businesses secure their data.
At Townsend Security, we have two distinct advantages. First, our Alliance Key Manager for Edge Computing solution is virtualized, automated, and VMware Ready. For example, our key management solution has been certified by VMware for vSphere key management - to protect VMs and vSAN storage. We are seeing many organizations deploy VMware at the Edge. Second, we have the ability to flexibly license and price our solutions for the Edge. Enterprises can now deploy full VMware VM encryption and key management at Edge with an affordable solution.
To hear this conversation in its entirety, download our podcast Living on the Edge and hear Patrick Townsend further discuss deployments on the edge, achieving a strong security posture with key management, and other ways that businesses can secure their private data.



![[Podcast] Don't Let Your Application or Database Limit Your Encryption Strategy](https://no-cache.hubspot.com/cta/default/15891/cc299bb8-69c0-431c-9461-d688c516a1b3.png)
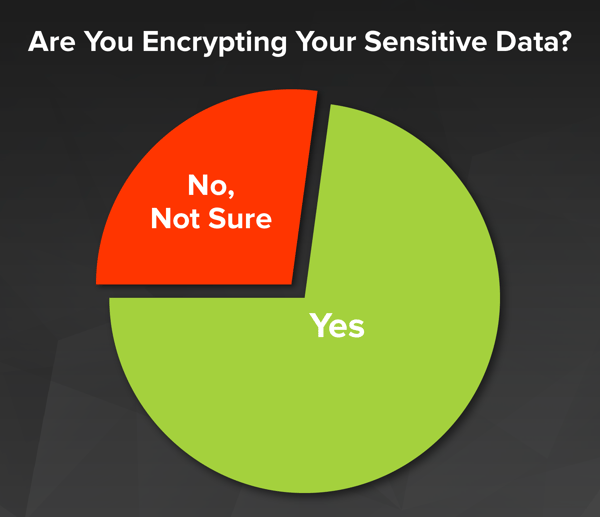
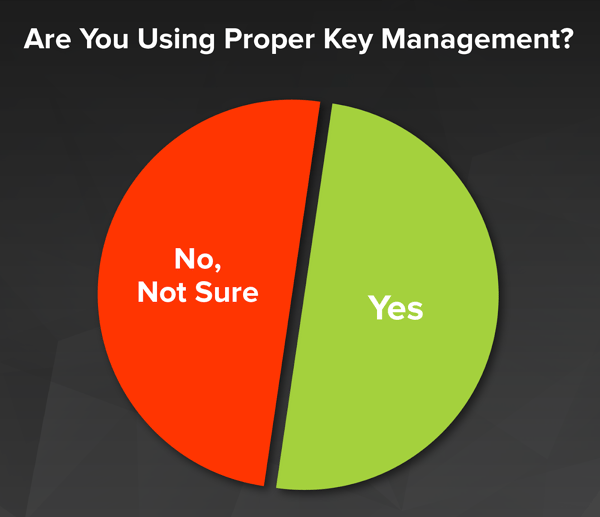
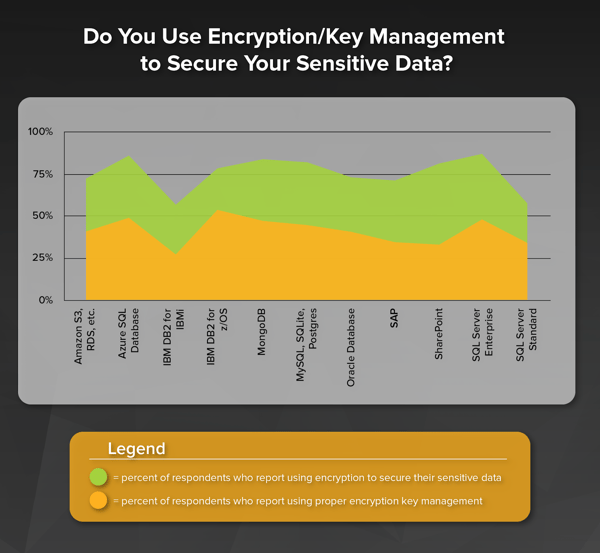

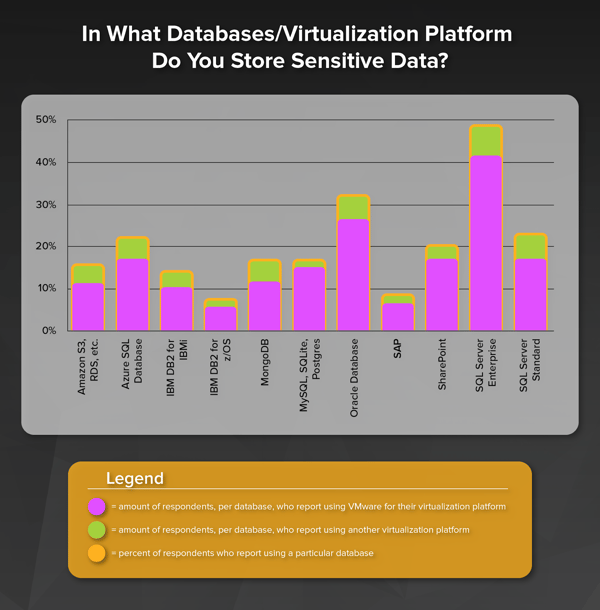








 In April of this year the Payment Card Industry Security Standards Council (PCI SSC) released a new document on cloud guidance called “
In April of this year the Payment Card Industry Security Standards Council (PCI SSC) released a new document on cloud guidance called “
