Recently, we here at Townsend Security had the opportunity to poll the fans of our Newsletter to see how folks are doing with encryption and key management for their data-at-rest. We conduct this survey, and surveys like it, so that the larger InfoSec community can get a snapshot of how businesses, in general, are doing in securing their sensitive data. Below are a few key findings, hope you enjoy!
Overall Results
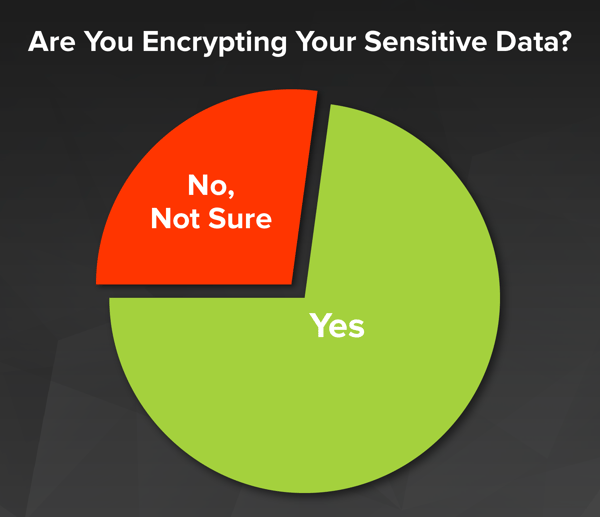
First, the good news: 73% of respondents report that they encrypt their sensitive data while at-rest. This makes sense as all the respondents are fans of our Newsletter; the group is a little self-selecting in that they have already expressed an interest in data security. Of course, we would like to see the number at 100%, but that would mean our work is already done—and we know we still have a long way to go.
To give a bit of perspective, we conducted two additional surveys that represent a more general audience that we published, here and here. In those two surveys the adoption rate for encryption is closer to 50%. So, hats off to our fans for being above the curve!
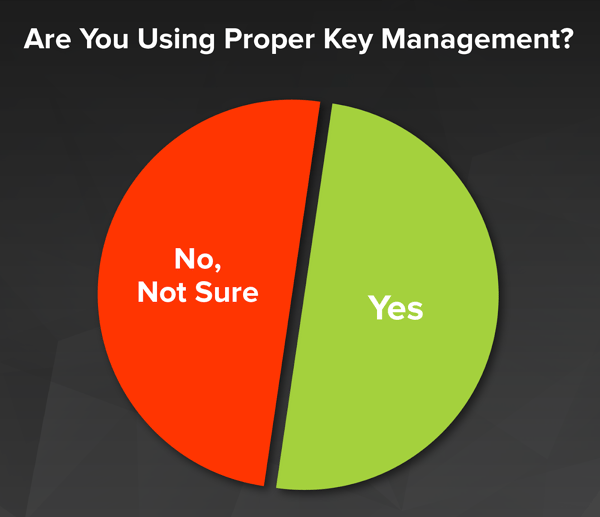
Now, the bad news: Only 50% of respondents say that they use proper key management to secure their encrypted data-at-rest (again, a little self-selecting in that, as part of the reason they like our Newsletter is that they are learning more about key management). Interestingly, even if you adjust the data to only look at those who replied that they do use encryption, the number only jumps to 66%.
As a comparison with the wider community, only about 30% of respondents in our other two polls (referenced above) said that they use encryption key management to securely manage their keys.
Expert Weigh-In: Patrick Townsend, CEO of Townsend Security
"Encryption is not enough. In order for encryption to be secure, the keys must be properly managed—100% of the time. If you don’t properly manage your encryption keys, it is like placing your house keys under your welcome mat. Every good thief knows to look in the obvious places for easy entry. Hackers do as well."
Encryption and Key Management Use, per Database/Blob Storage
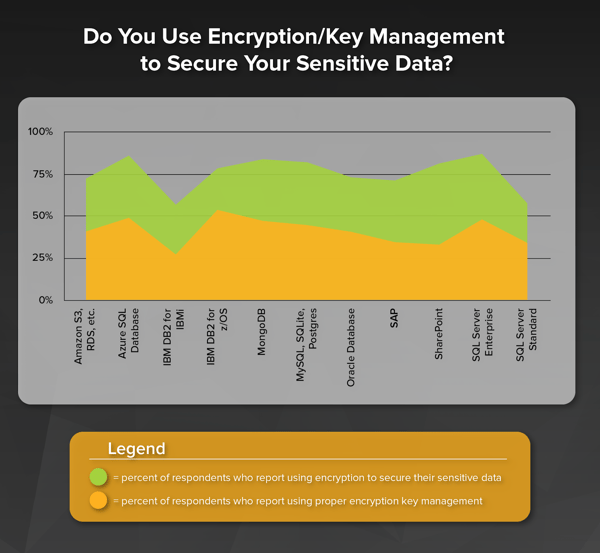
It is no surprise to see that, overall, if a database/blob storage reports a rise/fall in the use of encryption, there is also a corresponding rise/fall in the use of proper key management. What is interesting, however, is the databases/blob storage where the respondents reported the widest gap in adoption of key management in comparison to the adoption of encryption. Here are the top five databases and their corresponding adoption gaps:
| Database | Gap in Encryption to Key Management Adoption |
| SharePoint: | 40% |
| SAP: | 28% |
| SQL Server Enterprise Edition: | 26% |
| MySQL, SQLite, PostgreSQL, etc: | 26% |
| MongoDB: | 24% |
 What may or may not be surprising is that SharePoint leads the pack in lack of key management adoption (compared to encryption adoption) and SQL Server Enterprise Edition comes in third. SharePoint is built on top of Microsoft SQL Server as its datastore (for structured data, at least). For SQL Server 2008 Enterprise edition and up, you now have the ability to not only take advantage of SQL Server’s Transparent Data Encryption (in SharePoint and SQL Server), but you also can leverage the power of a third-party encryption key manager using Extensible Key Management (EKM). This means it is incredibly easy to not only deploy encryption but also proper manage the encryption keys.
What may or may not be surprising is that SharePoint leads the pack in lack of key management adoption (compared to encryption adoption) and SQL Server Enterprise Edition comes in third. SharePoint is built on top of Microsoft SQL Server as its datastore (for structured data, at least). For SQL Server 2008 Enterprise edition and up, you now have the ability to not only take advantage of SQL Server’s Transparent Data Encryption (in SharePoint and SQL Server), but you also can leverage the power of a third-party encryption key manager using Extensible Key Management (EKM). This means it is incredibly easy to not only deploy encryption but also proper manage the encryption keys.
What is less surprising is the other three that made the top of the list. All these come with free editions that do not come with encryption libraries, let alone the ability to properly manage the keys. So anyone spinning up a free version of these databases will, by their very nature, not be able to secure their data.
Expert Weigh-In: Tim Roncevich, Partner at CyberGuard Compliance
"Many Enterprise editions of databases come with robust AES encryption and a way for a third-party vendor to manage the encryption keys. If you are storing sensitive data in an open-source, or free, version of a database, upgrade today. Hacks similar to the Cathay Pacific breach of 2018 were due to the company not upgrading to the Enterprise edition to take advantage of the encryption and key management that were available to them."
What Virtualization Do You Use?
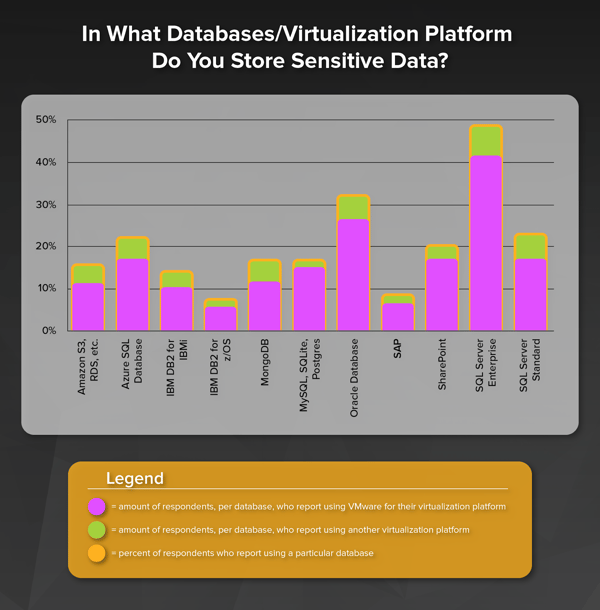
About three-quarters of respondents said that they use VMware in their environment. The other quarter reported using Hyper-V, Red Hat Virtualization, Citrix Hypervisor, or KVM. Less than 10% said they used multiple virtualization platforms.
This is great news for the majority of businesses, then, in terms of encryption and key management. VMware’s vSphere 6.5 and up come with encryption ready to use. Not only that, but using a third-party encryption key manager is easy to set up and deploy.
Expert Weigh-In: Sharon Kleinerman, Director of Sales at Townsend Security
"For those organizations struggling to secure their data-at-rest with encryption and key management, doing so has never been easier. If you have VMware 6.5 and above, you simply set up your third-party key manager through vSphere’s KMS Cluster KMIP interface, tell vSphere which VMs you want encrypted, and your data is encrypted. Same with vSAN. It really is easy to encrypt with VMware as your virtual environment."
Backup & Recovery Solutions
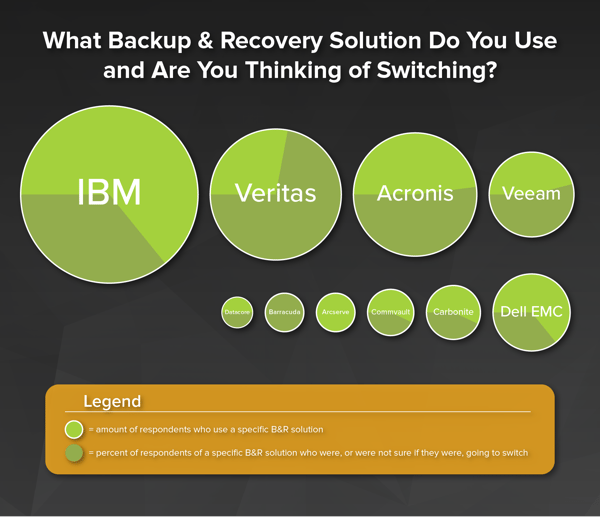
Backup and recovery solutions are an integral part of business continuity. In fact, Allied Market Research estimates that the market will grow by almost 25% year over year through 2023. In the next few years, however, Gartner estimates that 50% of companies will augment or replace their current backup solution with another.
Our findings fall roughly in line with Gartner’s research. According to our survey, about 40% of respondents say they will, or don’t know if they will, replace their current backup and recovery solution.
Expert Weigh-In: Steve Brown, Partner at Rutter Networking Technologies
"For those thinking of switching your B&R solution, it is important to make sure that the solution you are switching to provides encryption and a way to manage your encryption keys. Encryption should not be an afterthought. Instead, it should be one of the main drivers as to why you would either stay with your current solution or look farther afield."
Conclusion
The rate at which data breaches are happening is not slowing down. We all know this. But the adoption rate of best practices is still lagging. While it is heartening to see our blog’s fanbase beating the overall average for using encryption and key management to secure sensitive data-at-rest, We still have a long way to go.
The good news, it is easier than ever to adopt best practices. If you are thinking about truly defending yourself with a defense-in-depth strategy, talk to us today.

