As blockchain technologies make their way towards general acceptance in private and public sector IT systems, the critical issues of governance, risk management and compliance come into play - and blockchain teams are maturing to address these areas. One important gap to fill involves the proper protection of sensitive data in a blockchain deployment. It seems odd to discuss data protection in the context of blockchain. Isn’t blockchain based on cryptography? Yes, it is, but there remains a gap in the area of data protection. Let’s delve into this in more detail.
 Blockchain’s innovative way of linking transactions and guaranteeing their immutability in a distributed ledger is based on well known and respected cryptographic algorithms and processes. The ability to extend this level of assurance across a large number of widely distributed nodes is clearly an amazing extension of modern computing. While there have been security lapses in public blockchain implementations, these have generally been related to improperly securing credentials and mistakes in implementing chaincode. Blockchain methodologies are standing up well to external attacks.
Blockchain’s innovative way of linking transactions and guaranteeing their immutability in a distributed ledger is based on well known and respected cryptographic algorithms and processes. The ability to extend this level of assurance across a large number of widely distributed nodes is clearly an amazing extension of modern computing. While there have been security lapses in public blockchain implementations, these have generally been related to improperly securing credentials and mistakes in implementing chaincode. Blockchain methodologies are standing up well to external attacks.
One important aspect of blockchain is its transparency. That is, everyone has perfect visibility into the transactions on a ledger and their current validity. This transparency is a core feature of blockchain - and that leads to a problem:
Some data that we want to put on the blockchain is sensitive, and we may not want to expose it to others.
There are lots of reasons why we might not want some information on the blockchain ledger to be transparent:
- An organization’s reputation suffers when they lose or expose sensitive information. This is true for both public and private organizations and a significant loss of reputation is difficult to mitigate.
- Even little bits of data in blockchain transactions needs to be protected. When sensitive data in a blockchain ledger are aggregated, it can indicate the direction of a business’s activity and leak important information about strategic developments to it competitors.
- Compliance regulations prevent storing sensitive personal information in the clear. The PCI Data Security Standard mandates that credit card (Primary Account Numbers) be encrypted. The New York Department of Financial Services (23 NYCRR 500) requires the encryption of certain sensitive information. The EU General Data Protection Regulation (GDPR) mandates the protection of sensitive information of “Data Subjects”. here are other regulations that require or recommend protection of sensitive data.
- Digital assets that represent intellectual property need to be protected from cybercriminals and state actors. The loss of key intellectual property can be devastating to a startup or mature enterprise.
Therefore, it is critical for organizations to design proper data privacy into blockchain projects from the very beginning. It is painful and potentially impossible to fix data privacy gaffs after the fact.
 Some blockchain advocates suggest that the solution to this conundrum is to not place sensitive information on the blockchain at all. But this is an impossible goal. Data on a blockchain may not specifically identify an individual, but may contain enough information that it can be combined with previously leaked information to form a full picture of an individual. Remember that hackers are really good at data aggregation. Losing a little sensitive information can lead to an embarrassing loss of a lot of information.
Some blockchain advocates suggest that the solution to this conundrum is to not place sensitive information on the blockchain at all. But this is an impossible goal. Data on a blockchain may not specifically identify an individual, but may contain enough information that it can be combined with previously leaked information to form a full picture of an individual. Remember that hackers are really good at data aggregation. Losing a little sensitive information can lead to an embarrassing loss of a lot of information.
Other blockchain advocates suggest that the answer to this problem is to store sensitive data off of the blockchain altogether. But does this really solve any problem? This approach loses the many advantages of blockchain technology, and doesn’t do anything to solve the data protection puzzle. “Out of sight, out of mind” is not a solution to any problem.
Some blockchain implementations attempt to achieve privacy through “add on” features. Hyperledger channels and collections are two examples of this. These facilities use access controls to attempt to achieve this. As good as these facilities are, access controls will not address the data protection requirements of compliance regulations, nor provide other protections that encryption provides.
For all of the reasons we encrypt sensitive data in traditional databases, we need to encrypt sensitive data on a blockchain. This doesn’t mean that we have to encrypt everything that we put on the blockchain ledger, but it means we have to have the same intelligence in regard to sensitive data on blockchains that we have in the most secure systems today.
Fortunately, we can accomplish data protection on blockchains and maintain their usefulness. In fact, not only CAN we accomplish this, we MUST accomplish this in order to preserve the usefulness of blockchain technology.
If we are going to encrypt data that we put on a blockchain, we have to address a few requirements that are specific to blockchains:
- We have to use industry standard encryption algorithms, such as AES, to meet compliance regulations.
- We have to manage encryption keys using industry standards and best practices. This means storing encryption keys away from the blockchain ledger and doing so in a provably standard and secure way.
- We have to make encryption keys available to the users and smart contracts that need them. This is a challenge in a distributed blockchain environment.
- We must authenticate user’s authority to use encryption keys.
- We must have a mechanism for restricting access to encryption keys, and for granting and revoking access to those keys.
- We know how to accomplish these tasks in a traditional, centralized IT system. Years of work have produced standardized approaches to encryption. But blockchain presents real challenges to meeting these challenges.
Fortunately, innovation in the area of protecting data on a blockchain ledger is advancing.
At BlockNKey we built a key orchestration system architected from the ground up for distributed ledger technology. NIST compliant encryption and key management, a key vault, and key access control are built into each registered blockchain node. Cryptographic keys grant permission to whomever is permitted access to the data, how it’s accessed and when it’s accessible. This enables multi-party access to the appropriate data in real time through verified and validated access points. BlockNKey is compatible with public and private blockchains while enabling proper data security with easy to use REST APIs. It will even help you if you are storing sensitive data “off chain”.
Townsend Security has partnered with BlockNKey to bring an encryption and key management solution to blockchain users. More information here.




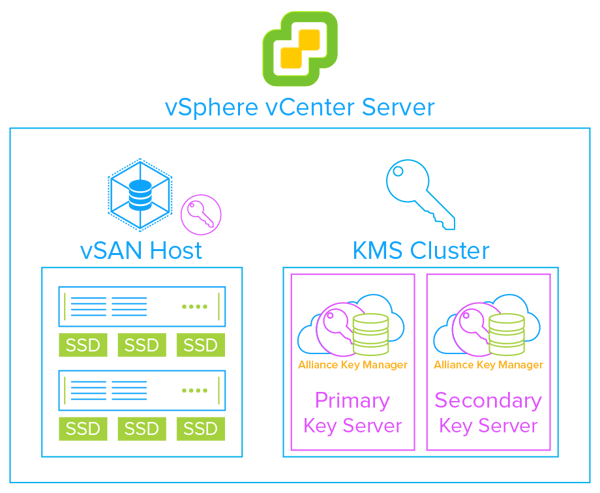


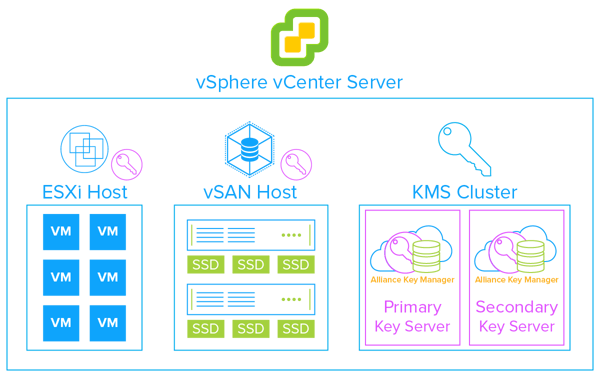
 IT Solution Provider Helps Customer Protect vSphere and vSAN Encryption Keys with Alliance Key Manager for VMWare
IT Solution Provider Helps Customer Protect vSphere and vSAN Encryption Keys with Alliance Key Manager for VMWare
 With SEBI’s new cyber security framework, JM Financial Asset Management Ltd turned to Indus Systems for guidance on how to better protect their data. JM Financial Asset Management Ltd, an Indus Systems customer of 10 years, were due for a technology refresh. As part of the project, the company would rely heavily on VMware and protecting private data with vSphere and vSAN encryption.
With SEBI’s new cyber security framework, JM Financial Asset Management Ltd turned to Indus Systems for guidance on how to better protect their data. JM Financial Asset Management Ltd, an Indus Systems customer of 10 years, were due for a technology refresh. As part of the project, the company would rely heavily on VMware and protecting private data with vSphere and vSAN encryption.