 This week brings part two of the "Data Privacy for the Non-Technical Person" series. Last week we determined what constitutes personal information that needs to be protected. This week Patrick Townsend, Founder & CTO, talks about how organizations are protecting sensitive information, how encryption and key management relate to each other, and what happens when encryption is not done correctly. If you are jumping in mid-stream, you can read part one here. Additionally, you can download our podcast titled "Data Privacy for the Non-Technical Person" to hear our conversation in its entirety.
This week brings part two of the "Data Privacy for the Non-Technical Person" series. Last week we determined what constitutes personal information that needs to be protected. This week Patrick Townsend, Founder & CTO, talks about how organizations are protecting sensitive information, how encryption and key management relate to each other, and what happens when encryption is not done correctly. If you are jumping in mid-stream, you can read part one here. Additionally, you can download our podcast titled "Data Privacy for the Non-Technical Person" to hear our conversation in its entirety.
How do organizations protect sensitive information?
They use a number of techniques. Some of them are pretty obvious. Businesses use anti-virus software and software to detect intrusions on their network, as well as making sure they have a secure web site if they are taking sensitive information from you over the internet. And then they do some things that most people might not be aware of. A business that is trying to protect your personal information will do some things that are procedural in nature – for example a lot of companies will now make sure all new employees have a background check.
Companies are also doing things that help make their data very difficult to steal. Encryption, which is the process of taking a credit card or social security number and turning it into and encrypted value, makes stealing data near impossible.
Companies who are really trying hard to protect information of their customers and employees are deploying a variety of tools. Encryption is probably one of the more important ones and it is one of the more difficult technologies to deploy, but certainly all of the major companies that you might do business with over the Internet will be using encryption to protect your data.
Encryption and key management have been talked about a lot lately. How do they relate to each other?
Encryption and key management go together. They are very complimentary technologies. When you encrypt a credit card number, you have an encryption algorithm that takes your credit card number and turns it into something totally different. But another important input into that process is a secret key. Many people think that the encryption algorithm itself is some kind of secret mechanism, which isn’t the case. Encryption is well understood. There are standards for it and it is readily available. What is really the secret that prevents losing data is the encryption key – just like the key to your front door is what protects your house. An encryption key works very much in the same way. Companies that use encryption really have to create a key that is very unique and very strong, and they have to protect it so that it doesn’t escape into the wild. Anyone that has the encrypted data and the encryption key, really can get the sensitive data back. In the real world of protecting data with encryption, measures are taken to protect the encryption key – that is the real secret that people are trying to protect in a business environment.
What happens when encryption is not done correctly?
There are many ways that encryption can be done poorly or incorrectly. We see that sometimes around the area of encryption key management. For example, storing an encryption key on the same platform where the data that it is protecting is just bad practice. Sometimes you hear the term “integrated key management” or people say “we are storing the encryption key in a database file and we have locked that database file down.” These are really poor practices and, in fact, cannot meet compliance regulations about encryption key management. So, that is just one example of encryption that is done badly.
Other examples are just using non-standard or proprietary encryption. The CUSP mode of AES encryption, for example, is not a standard mode and is a proprietary protocol that can’t be a part of true compliance. It is just another example of running off the rails in terms of best practice for encryption. A company that is purchasing encryption technologies should really examine their vendors carefully. I always point back to NIST certification because it is the bottom-line indication you have that the encryption product is a good quality solution.
Here is another interesting thing that I think people sometimes forget. If you have a data loss, it is going to be your problem, not the vendors problem. Even though you may have acquired a solution that is not right, it is still going to fall on you. It is going to be your headache to solve, your customers that are upset, and your financial loss when data gets out. The loss of trust from your customers and employees is also difficult too. For all these reasons, I think paying attention to encryption technologies is a good idea.
Stay tuned for our next and final installment in this series. Download our podcast “Data Privacy for the Non-Technical Person” to hear more of this conversation.

 Microsoft defines an interface for external key management systems with their SQL Server Extensible Key Management (EKM) architecture, but does not define how encryption key management vendors should communicate between the Windows server and the encryption key manager. This is important because the communications over the TCP network must be secure, and access to the client side certificate credentials also has to be secure.
Microsoft defines an interface for external key management systems with their SQL Server Extensible Key Management (EKM) architecture, but does not define how encryption key management vendors should communicate between the Windows server and the encryption key manager. This is important because the communications over the TCP network must be secure, and access to the client side certificate credentials also has to be secure.

 Yes. There are quite a number of laws, and they cross over each other too. Many find themselves having to work with several regulations when protecting data. If you take credit cards, you fall under the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is a private regulation promoted by the card brands (Visa, MasterCard, etc.). If you are a bank or engaged in the banking industry you fall under the Gramm-Leach-Bliley Act (GLBA) and FFIEC regulations for protecting information. Those are specific to the banking industry. If you go to the doctor or are a doctor/medical clinic or any place in the medical industry, you fall under the HIPAA/HITECH Act to protect patient’s medical information. There are also other regulations too. The government is moving laws through congress to define protections for PII. So there are a number of regulations affecting data that needs to be protected.
Yes. There are quite a number of laws, and they cross over each other too. Many find themselves having to work with several regulations when protecting data. If you take credit cards, you fall under the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is a private regulation promoted by the card brands (Visa, MasterCard, etc.). If you are a bank or engaged in the banking industry you fall under the Gramm-Leach-Bliley Act (GLBA) and FFIEC regulations for protecting information. Those are specific to the banking industry. If you go to the doctor or are a doctor/medical clinic or any place in the medical industry, you fall under the HIPAA/HITECH Act to protect patient’s medical information. There are also other regulations too. The government is moving laws through congress to define protections for PII. So there are a number of regulations affecting data that needs to be protected.
 This week brings part two of the "Data Privacy for the Non-Technical Person" series. Last week we determined what constitutes personal information that needs to be protected. This week Patrick Townsend, Founder & CTO, talks about how organizations are protecting sensitive information, how encryption and key management relate to each other, and what happens when encryption is not done correctly. If you are jumping in mid-stream, you can read part one
This week brings part two of the "Data Privacy for the Non-Technical Person" series. Last week we determined what constitutes personal information that needs to be protected. This week Patrick Townsend, Founder & CTO, talks about how organizations are protecting sensitive information, how encryption and key management relate to each other, and what happens when encryption is not done correctly. If you are jumping in mid-stream, you can read part one  It was fascinating to read the headlines this week about the terrible flaw that was discovered in the Advanced Encryption Standard (AES). It sounded like the end of security as we know it. I read blogs and articles that headlined “AES Broken” and “Fatal Flaw in AES”. It was fun reading, but completely misleading. So, what really happened?
It was fascinating to read the headlines this week about the terrible flaw that was discovered in the Advanced Encryption Standard (AES). It sounded like the end of security as we know it. I read blogs and articles that headlined “AES Broken” and “Fatal Flaw in AES”. It was fun reading, but completely misleading. So, what really happened?
 As I attend industry events, it is surprising how many times we hear questions like “what constitutes personal information that needs to be protected?” I recently sat down with Patrick Townsend, our Founder and CTO to discuss data privacy for the non-technical person.
As I attend industry events, it is surprising how many times we hear questions like “what constitutes personal information that needs to be protected?” I recently sat down with Patrick Townsend, our Founder and CTO to discuss data privacy for the non-technical person.  As “The Encryption Company,” we often blog about meeting PCI DSS with encryption and key management. Our NIST-certified technologies will help your organization satisfy Section 3 of PCI DSS, as well as other privacy regulations. But there is another section of PCI DSS that Townsend Security can help you with – Section 10.
As “The Encryption Company,” we often blog about meeting PCI DSS with encryption and key management. Our NIST-certified technologies will help your organization satisfy Section 3 of PCI DSS, as well as other privacy regulations. But there is another section of PCI DSS that Townsend Security can help you with – Section 10.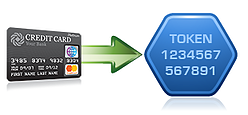 The generation of tokens is an important part of the new PCI SSC guidance on tokenization. Tokens can be generated using a number of techniques including random number generation, encryption, sequential assignment, and indexes. Using tokens to recover the original credit card number must be “computationally infeasible” according to the new guidance.
The generation of tokens is an important part of the new PCI SSC guidance on tokenization. Tokens can be generated using a number of techniques including random number generation, encryption, sequential assignment, and indexes. Using tokens to recover the original credit card number must be “computationally infeasible” according to the new guidance.
 Today the Payment Card Industry Security Standards Council issued some long awaited guidance on tokenization as a method of protecting credit card information (“PAN”, or Primary Account Number in PCI language). This guidance has taken a number of months to produce, and will be very helpful to merchants who want to deploy tokenization solutions to reduce the scope of PCI compliance efforts, for those who have already deployed solutions and need to assess if they meet minimum requirements, and for QSA auditors who have been looking for some guidance in this area.
Today the Payment Card Industry Security Standards Council issued some long awaited guidance on tokenization as a method of protecting credit card information (“PAN”, or Primary Account Number in PCI language). This guidance has taken a number of months to produce, and will be very helpful to merchants who want to deploy tokenization solutions to reduce the scope of PCI compliance efforts, for those who have already deployed solutions and need to assess if they meet minimum requirements, and for QSA auditors who have been looking for some guidance in this area.