White Paper: Business Case for Tokenization
|
Tokenizing sensitive data delivers an outstanding return on investment (ROI) to businesses by providing a risk-reduction of losing sensitive data. By tokenizing data, organizations can reduce the chance of losing sensitive information – credit card numbers, social security numbers, banking information, and other types of PII. In some cases tokenization can take an entire server or database application out of scope for compliance regulations. This blog will discuss how tokenization can reduce risks in customer service departments, with outside services, and in BI and Query environments.
Tokenization for Customer Service
Tokenization can reduce risk in the customer service department by removing sensitive data from customer service databases. For out-sourced operations you should tokenize data before sending it to the outside service. A customer service worker can still accept real information on the phone from an end customer, but there is no need to store the actual information in a database that can be stolen. Tokenization services will associate real information with tokenized information for data retrieval. While using tokenization in a customer service environment can’t completely remove the risk of data loss, but it can dramatically reduce the amount of data at risk and help you identify potential problems.
Tokenization for Outside Services
Many retail companies send their Point-Of-Sale transaction information to analytics service providers for trend and business analysis. The service provider identifies trends, spots potential problems with supply chains, and helps evaluate the effectiveness of promotions. In some cases, service providers consolidate information from a large number of companies to provide global trends and analysis. You can avoid the risk of data loss by replacing the sensitive data (names, credit card numbers, addresses, etc.) with tokens before sending the data to the service provider.
Tokenization for Business Intelligence and Query
Many IT departments help their business users analyze data by providing them with business intelligence (BI), query reporting tools, and databases of historical information. These tools and databases have empowered end-users to create their own reports, analyze business trends, and take more responsibility for the business. This practice has decreased workloads and increased efficiency in IT departments.
Unfortunately, these tools and databases open a new point of loss for sensitive information. A database with years of historical information about customers, suppliers, or employees is a high value target for data thieves. Criminals aggregate this type of information to provide a complete profile of an individual, making it easier to steal their identity. When tokens replace names, addresses, and social security numbers, this makes the BI database unusable for identity theft, while maintaining the relational integrity of the data. Tokenizing business intelligence data is an easy win to reduce your risk of exposure.
Download our white paper “The Business Case for Tokenization: Reducing the Risk of Data Loss” to see how tokenization is helping organizations meet their business goals without exposing their sensitive data to loss.


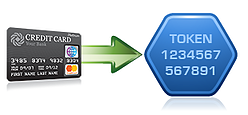 The generation of tokens is an important part of the new PCI SSC guidance on tokenization. Tokens can be generated using a number of techniques including random number generation, encryption, sequential assignment, and indexes. Using tokens to recover the original credit card number must be “computationally infeasible” according to the new guidance.
The generation of tokens is an important part of the new PCI SSC guidance on tokenization. Tokens can be generated using a number of techniques including random number generation, encryption, sequential assignment, and indexes. Using tokens to recover the original credit card number must be “computationally infeasible” according to the new guidance.
 Today the Payment Card Industry Security Standards Council issued some long awaited guidance on tokenization as a method of protecting credit card information (“PAN”, or Primary Account Number in PCI language). This guidance has taken a number of months to produce, and will be very helpful to merchants who want to deploy tokenization solutions to reduce the scope of PCI compliance efforts, for those who have already deployed solutions and need to assess if they meet minimum requirements, and for QSA auditors who have been looking for some guidance in this area.
Today the Payment Card Industry Security Standards Council issued some long awaited guidance on tokenization as a method of protecting credit card information (“PAN”, or Primary Account Number in PCI language). This guidance has taken a number of months to produce, and will be very helpful to merchants who want to deploy tokenization solutions to reduce the scope of PCI compliance efforts, for those who have already deployed solutions and need to assess if they meet minimum requirements, and for QSA auditors who have been looking for some guidance in this area.
 As I talk to Enterprise customers I’m finding a lot of confusion about when to use encryption or tokenization, and how to think about these two data protection technologies. Once you understand how each of these technologies work, you understand that there are no easy answers to which is best for you, or when one is better than another. I want to talk about some general guidelines I’ve developed to help with this conundrum.
As I talk to Enterprise customers I’m finding a lot of confusion about when to use encryption or tokenization, and how to think about these two data protection technologies. Once you understand how each of these technologies work, you understand that there are no easy answers to which is best for you, or when one is better than another. I want to talk about some general guidelines I’ve developed to help with this conundrum.


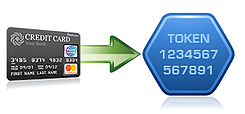 As companies work to meet regulatory requirements to protect Personally Identifiable Information (PII), one option to minimize the risk of loss is to replace sensitive data with a non-sensitive replacement value, or “token.”
As companies work to meet regulatory requirements to protect Personally Identifiable Information (PII), one option to minimize the risk of loss is to replace sensitive data with a non-sensitive replacement value, or “token.”  Encryption and tokenization are the two leading technologies used to protect sensitive data from loss and subsequent breach notification and legal liability. Organizations who try to meet compliance regulations struggle to understand when to use strong encryption and when to use tokenization to protect information. Many organizations will find both technologies helpful in different places in their IT infrastructure.
Encryption and tokenization are the two leading technologies used to protect sensitive data from loss and subsequent breach notification and legal liability. Organizations who try to meet compliance regulations struggle to understand when to use strong encryption and when to use tokenization to protect information. Many organizations will find both technologies helpful in different places in their IT infrastructure. Compliance regulations are moving inexorably towards requiring the protection of sensitive data. The private information of customers, employees, patients, vendors and all of the people we come into contact with as Enterprises, must be protected from loss and misuse. At the same time that regulations are getting more teeth, there is more consensus about the technologies to protect data in our applications and databases. Encryption and tokenization are now the accepted methods of protecting data, and encryption key management is central to both technologies.
Compliance regulations are moving inexorably towards requiring the protection of sensitive data. The private information of customers, employees, patients, vendors and all of the people we come into contact with as Enterprises, must be protected from loss and misuse. At the same time that regulations are getting more teeth, there is more consensus about the technologies to protect data in our applications and databases. Encryption and tokenization are now the accepted methods of protecting data, and encryption key management is central to both technologies.