This is the third part in our series looking at recent announcements by Amazon, Microsoft and other cloud service providers regarding new encryption and key management services. Let’s talk about log collection and active monitoring as a security best practice, and as a requirement to meet PCI DSS security requirements. Since the PCI DSS guidelines implement common security best practices, they are a good starting point for evaluating the security of any application and platform that processes sensitive data. Following the practice of the first part of this series we will use the PCI document “PCI DSS Cloud Computing Guidelines, Version 2.0” as our reference point, and add in some other sources of security best practices. Even if you don’t have to meet PCI data security requirements, this should be helpful when evaluating your security posture in the cloud.

Collecting system logs and actively monitoring them is a core component of every cyber security recommendation. Cybercriminals often gain access to IT systems and go undetected for weeks or months. This gives them the ability to work on compromising systems and stealing data over time. Active monitoring is important in the attempt to detect and thwart this compromise.
Here is what PCI says about active monitoring in Section 10 of the PCI DSS (emphasis added):
Review logs and security events for all system components to identify anomalies or suspicious activity.
Many breaches occur over days or months before being detected. Checking logs daily minimizes the amount of time and exposure of a potential breach. Regular log reviews by personnel or automated means can identify and proactively address unauthorized access to the cardholder data environment. The log review process does not have to be manual. The use of log harvesting, parsing, and alerting tools can help facilitate the process by identifying log events that need to be reviewed.
In recognition of the importance of ongoing, active monitoring the National Institute of Standards and Technology (NIST) provides this guidance in their Special Publication 800-137 “Information Security Continuous Monitoring (ISCM)” guidance:
The Risk Management Framework (RMF) developed by NIST, describes a disciplined and structured process that integrates information security and risk management activities into the system development life cycle. Ongoing monitoring is a critical part of that risk management process. In addition, an organization’s overall security architecture and accompanying security program are monitored to ensure that organization-wide operations remain within an acceptable level of risk, despite any changes that occur. Timely, relevant, and accurate information is vital, particularly when resources are limited and agencies must prioritize their efforts.
And active monitoring is a component of the SANS Top 20 security recommendations:
Collect, manage, and analyze audit logs of events that could help detect, understand, or recover from an attack.
Deficiencies in security logging and analysis allow attackers to hide their location, malicious software, and activities on victim machines. Even if the victims know that their systems have been compromised, without protected and complete logging records they are blind to the details of the attack and to subsequent actions taken by the attackers. Without solid audit logs, an attack may go unnoticed indefinitely and the particular damages done may be irreversible.
Because of poor or nonexistent log analysis processes, attackers sometimes control victim machines for months or years without anyone in the target organization knowing, even though the evidence of the attack has been recorded in unexamined log files.
Deploy a SIEM (Security Incident and Event Management) or log analytic tools for log aggregation and consolidation from multiple machines and for log correlation and analysis.
This is why actively collecting and monitoring system and application logs is critical for your security strategy.
Implementing this critical security control in a cloud environment presents some special challenges. Here is what the PCI cloud guidance says:
Additionally, the ability to maintain an accurate and complete audit trail may require logs from all levels of the infrastructure, requiring involvement from both the CSP and the client. For example, the CSP could manage system-level, operating-system, and hypervisor logs, while the client configures logging for their own VMs and applications. In this scenario, the ability to associate various log files into meaningful events would require correlation of client-controlled logs and those controlled by the CSP.
It is not enough to collect logs from a few selected points in your cloud application environment. You need to collect all of the logs from all of the components that you deploy and use in your cloud application. This is because the effectiveness of active monitoring depends on the correlation of events across your entire application, database, and network and this includes the cloud providers systems and infrastructure. Here is what ISACA says about security event correlation:
Correlation of event data is critical to uncover security breaches because security incidents are made up of a series of events that occur at various touch points throughout a network--a many-to-one process. Unlike network management, which typically is exception-based or a one-to-one process, security management is far more complex. An attack typically touches a network at multiple points and leaves marks or breadcrumbs at each. By finding and following that breadcrumb trail, a security analyst can detect and hopefully prevent the attack.
Your encryption key management system is one of those critical system components that must be monitored and whose events should be aggregated into a unified view. Key management logs would include encryption key establishment and configuration, encryption key access and use, and operating system logs of every component of the key management service. You should be able to collect and monitor logs from all parts of your applications and cloud platform.
Unfortunately, current key management services from cloud providers only provide a very limited level of access to critical component logs. You might have access to a limited audit trail of your own access to encryption keys, but no access to the key service system logs, HSM access logs, HSM audit logs, or HSM operating system logs. Without access to the logs in these components it is not possible for you to implement an effective log collection and active monitoring strategy. You are working in the dark, and without full access to all logs on all components of your cloud key management service you can’t comply with security best practices for log collection, correlation, and active monitoring.
Since key management systems are always in scope for PCI audit and are extensions of your application environment it is difficult to see how these new cloud key management services can meet PCI DSS requirements for log collection and monitoring as currently implemented.
Does this mean you can’t implement security best practices for key management in the cloud? I don’t think so. There are multiple vendors, including us (see below), who offer cloud key management solutions that provide full access to key management, configuration, key usage, application, and operating system logs. You can deploy a key management service that fully supports security best practices for log collection and monitoring.
In part 4 of this series we’ll look at the topic of key custody and multi-tenancy and how it affects the security of your key management solution in the cloud.
Patrick
Resources
Alliance Key Manager for AWS
Alliance Key Manager for Azure
Alliance Key Manager for VMware and vCloud
Alliance Key Manager for Drupal

 We don’t have a solution for IBM Mainframe customers, but I am happy to report that our partner CorreLog does! IBM System z Mainframe users can deploy the CorreLog solution and get the same types of security event collection and SIEM integration that we provide in Alliance LogAgent. The two products are not exactly the same in terms of features, but CorreLog will give you the security event collection and SIEM integration that you need.
We don’t have a solution for IBM Mainframe customers, but I am happy to report that our partner CorreLog does! IBM System z Mainframe users can deploy the CorreLog solution and get the same types of security event collection and SIEM integration that we provide in Alliance LogAgent. The two products are not exactly the same in terms of features, but CorreLog will give you the security event collection and SIEM integration that you need. CorreLog provides their own SIEM solution, but they also integrate with a wide variety of other SIEM vendor solution. You can deploy CorreLog to send security events to IBM Security QRadar, LogRhythm, HP ArcSight, Dell SecureWorks, RSA Envision, and many other SIEM solutions! This also means that you are not locked into any one SIEM vendor and can easily migrate to a new solution if or when you want to.
CorreLog provides their own SIEM solution, but they also integrate with a wide variety of other SIEM vendor solution. You can deploy CorreLog to send security events to IBM Security QRadar, LogRhythm, HP ArcSight, Dell SecureWorks, RSA Envision, and many other SIEM solutions! This also means that you are not locked into any one SIEM vendor and can easily migrate to a new solution if or when you want to.



 PCI DSS. HIPAA/HITECH. State Privacy Laws. What do all these compliance regulations have in common? They require you to be collecting and monitoring your system logs. To give an example of how logging works, if someone tries to sign into an IBM i (or any server) and for whatever reason and the username or password is invalid, that event is logged in the system log. Why is this important? Because if you were to look at this system log in real-time and notice several invalid username and password events, you would say “Hey, our system is being attacked. We need to take action on this now.”
PCI DSS. HIPAA/HITECH. State Privacy Laws. What do all these compliance regulations have in common? They require you to be collecting and monitoring your system logs. To give an example of how logging works, if someone tries to sign into an IBM i (or any server) and for whatever reason and the username or password is invalid, that event is logged in the system log. Why is this important? Because if you were to look at this system log in real-time and notice several invalid username and password events, you would say “Hey, our system is being attacked. We need to take action on this now.” 


 We’ve had an upsurge in interest recently in our
We’ve had an upsurge in interest recently in our 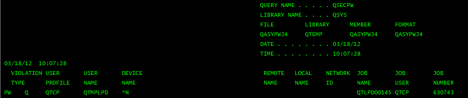
 In our final installment on system logging on the IBM i series, Patrick Townsend, Founder & CTO, discusses what to look for when selecting and deploying a logging solution. As we found out in
In our final installment on system logging on the IBM i series, Patrick Townsend, Founder & CTO, discusses what to look for when selecting and deploying a logging solution. As we found out in  System logging is also important for meeting compliance regulations too, right?
System logging is also important for meeting compliance regulations too, right? 
 As a company that works hard to protect your data, we get a lot of questions – from people wanting to know the ins and outs of our products to IT professionals who are new to the world of meeting compliance regulations. Luckily, our company has several experts to answer these questions. One topic that we often get questions regarding is system logging on the IBM i (AS/400). Logging on the IBM i is different than logging on other platforms. I recently sat down with Patrick Townsend, Founder & CEO, to pick his brain on what system logging is, and why it is so unique on the IBM i.
As a company that works hard to protect your data, we get a lot of questions – from people wanting to know the ins and outs of our products to IT professionals who are new to the world of meeting compliance regulations. Luckily, our company has several experts to answer these questions. One topic that we often get questions regarding is system logging on the IBM i (AS/400). Logging on the IBM i is different than logging on other platforms. I recently sat down with Patrick Townsend, Founder & CEO, to pick his brain on what system logging is, and why it is so unique on the IBM i. As “The Encryption Company,” we often blog about meeting PCI DSS with encryption and key management. Our NIST-certified technologies will help your organization satisfy Section 3 of PCI DSS, as well as other privacy regulations. But there is another section of PCI DSS that Townsend Security can help you with – Section 10.
As “The Encryption Company,” we often blog about meeting PCI DSS with encryption and key management. Our NIST-certified technologies will help your organization satisfy Section 3 of PCI DSS, as well as other privacy regulations. But there is another section of PCI DSS that Townsend Security can help you with – Section 10.