VMware allows customers to use native vSphere and vSAN encryption to protect VMware images and digital assets. But as we know, to truly protect private data, encryption keys must also be properly stored and managed. I recently sat down with Patrick Townsend, Founder and CEO of Townsend Security, to talk about vSphere and vSAN encryption, deploying multiple, redundant key servers as a part of the KMS Cluster configuration for maximum resilience and high availability, as well as meeting compliance regulations and security best practices for your organization. Additionally, we talked about Alliance Key Manager for VMware and how it is helping businesses protect their sensitive data.
VMware virtualization has been a game-changing technology for IT, providing efficiencies and capabilities that have previously been impossible for organizations constrained within a traditional IT data center world.
It is really great to see VMware, as a company, stepping up to embrace encryption for vSphere and vSAN. Introduced in vSphere 6.5 and vSAN version 6.6, encryption allows users to protect data at rest. Additionally, there is a really great key management interface, which provides an excellent path to store and manage keys. While these versions have been out for a while, many customers are just now getting around to upgrading and can take advantage of VMware's native encryption. With VMware, organizations are able to reduce hardware costs, lower operational cost, and provides a clear a path to move to the cloud. With the addition of encryption, you can deploy secure environments where there is less risk of data loss in the event of a breach.
Let’s dive in a little more and talk about vSphere and vSAN encryption. Can you walk me through how an organization might deploy encryption and key management?
Sure. I think in a typical VMware environment, organizations are already doing some encryption in their applications. For example, they may be running Microsoft SQL Server in a VM and using Transparent Data Encryption (TDE) to protect the data. With the new facilities, you now get the ability to encrypt right in the VMware infrastructure itself. There is one thing that I think VMware did really well, and they have proven this over and over again, is that they have laid out a certification process for key management vendors, which gives VMware customers confidence that they are purchasing and deploying a solution that has been vetted by VMware themselves. Our Alliance Key Manager, for example, has been certified for:
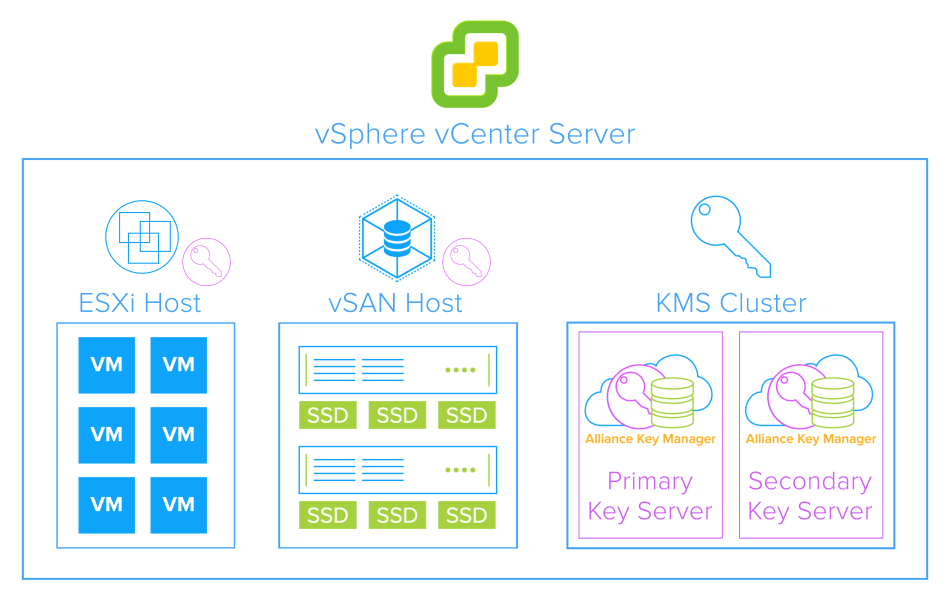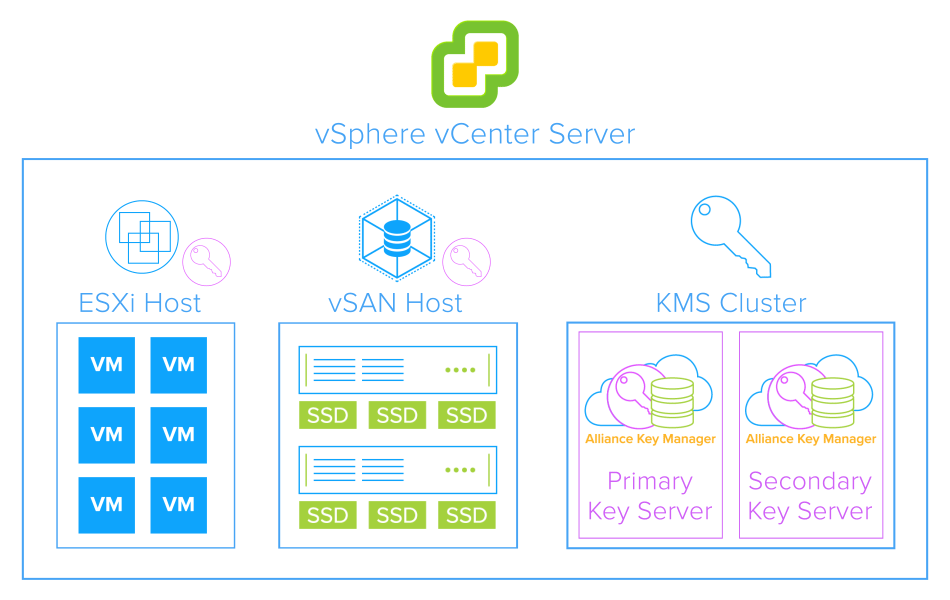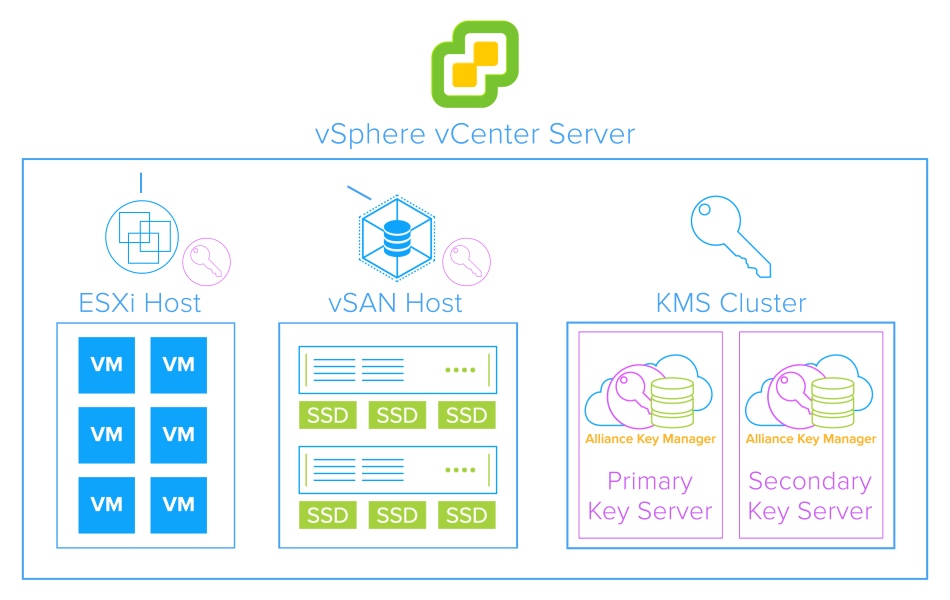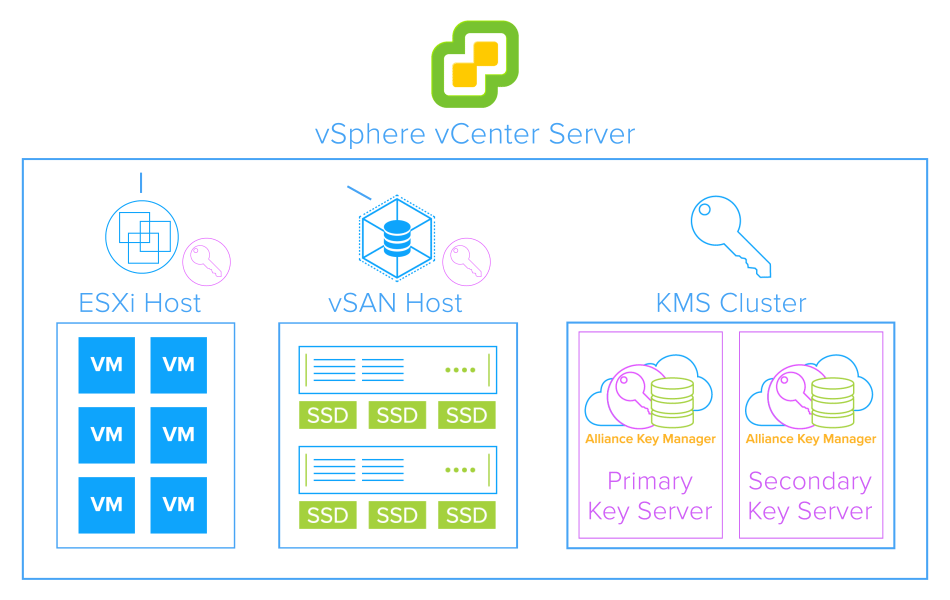
In terms of deploying key management, it is easy. We recommend using both a production key server and a failover key server. vSphere supports KMS cluster configurations which allow you to have a resilient encryption and key management architecture. Aside from just being a security best practice, we are seeing our customers deploy two servers because they never want to lose access to their encrypted data. The servers synchronize in real-time and have automatic failover capabilities.
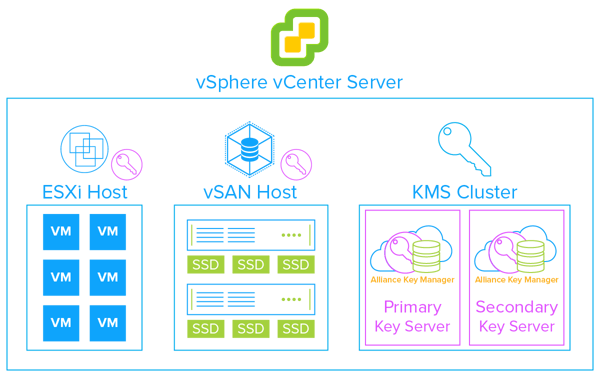
You can’t talk about key management without talking about compliance. Whether it is PCI DSS, GDPR, or state and federal privacy laws, who doesn’t fall under compliance these days?
Yes, good question. That is probably a very short list these days. When you look at all the existing compliance regulations around the world, including the new GDPR, you realize that everyone falls under some compliance regulation, and most of us fall under multiple regulations. Enterprises, big and small, public and private, fall under the same compliance regulations. Additionally, I have heard more from privately held companies that they think they are exempt - which is not true.
So you are correct. Compliance regulations are driving a lot of uptake in encryption and I would say that lately GDPR is driving the most interest. If you look at Article 32 and related recitals, the requirement to protect a data subjects information, there is a clear call for encryption. GDPR has put a new focus on the need to protect private data, as well as to take a broad view at what should be considered sensitive data. It is not just a credit card number or social security number. Information like a phone number or email address can be considered sensitive data.
How is your Alliance Key Manager helping VMware users protect their private data?
Well, we have been helping VMware customers for a number of years who are encrypting at the application level. Our Alliance Key Manager for VMware runs as a virtual software appliance and is binarily the same as our hardware security module (HSM). What is new, is that VMware opened the vSphere and vSAN and products to support encryption key management. Now VMware users can leverage the same key management solution for both application and VMware infrastructure encryption.
People often ask us, “How is your key manager different than your competitors”? One thing that makes us stand out is that we are very diligent about meeting compliance requirements (PCI DSS, GDPR, HIPAA, etc.) and industry standards (FIPS 140-2, KMIP, etc.). Years ago, when we partnered with VMware, one of the first things we did was work with VMware and a QSA auditor to achieve a PCI compliance statement. Customers can now be assured that when they deploy our Alliance Key Manager in VMware that they are meeting PCI compliance.
What else do VMware customers need to know about Alliance Key Manager for VMware?
Alliance Key Manager is a mature product that has been on the market for more than 10 years. It uses the same software that runs inside our Hardware Security Module (HSM), so customers can be confident that they are running exactly the same key management software that is FIPS 140-2 compliant and in use by over 3,000 customers worldwide. Additionally, the security posture that the key manager allows, as well as the reference architecture that VMware provides, really gives VMware customers a road map to doing a secure installation.
The other thing that I think a lot of people might not realize is, that when they deploy Alliance Key Manager, they have our entire library of client side applications, SDKs, and sample code available to them. For example, we have a Microsoft SQL Server TDE encryption component, support for MongoDB via KMIP, and sample SDKs for languages like Java, PHP, Python, etc. All of that comes along with the key manager and makes it easy to address security requirements.
Finally, I’d like to mention our partnership with VMware. We are diligent about maintaining our certifications with Alliance Key Manager. Doing this brings a level of confidence to the product for our customers. Prior to starting an encryption project they may be a little leery of key management because they have heard that it may be complicated. That was true in the past. In fact, today it is actually extremely simple to deploy. Another barrier that we have knocked down is the scalability issue. Our solution works across multiple platforms - AWS, Azure, VMware or as an HSM. They all talk to each other, and if one goes down, another will automatically fail over. That gives VMware customers the ability to be extremely flexible about how they deploy key management. It is not uncommon that our customers will deploy an application in the cloud, deploy a key manager in AWS, and then mirror those keys back to their on-premise VMware infrastructure. All of this is really straightforward and simple to deploy.
To hear this conversation in its entirety, download our podcast Protecting Data with vSphere & vSAN Encryption and hear Patrick Townsend further discuss protecting data in vSphere and vSAN with encryption and key management.





 Secrets Management SaaS for CMS Systems Including Drupal and WordPress
Secrets Management SaaS for CMS Systems Including Drupal and WordPress

 Organizations starting an encryption project always have this question on their minds. It is a simple question, but can be hard to answer. Generally speaking, you should encrypt any information that alone, or when combined with other information, can identify a unique, individual person. This is called Personally Identifying Information, or PII. This should be your starting point, but you may need to address other information depending on the compliance regulations you must meet.
Organizations starting an encryption project always have this question on their minds. It is a simple question, but can be hard to answer. Generally speaking, you should encrypt any information that alone, or when combined with other information, can identify a unique, individual person. This is called Personally Identifying Information, or PII. This should be your starting point, but you may need to address other information depending on the compliance regulations you must meet. Townsend Security is helping the MongoDB community encrypt sensitive data and properly manage encryption keys. Developers who need to protect sensitive data know that
Townsend Security is helping the MongoDB community encrypt sensitive data and properly manage encryption keys. Developers who need to protect sensitive data know that 
 Townsend Security’s support for Authy means that IBM i (iSeries, AS/400) users can now deploy a popular and low-cost two factor authentication product without the expense of back-end hardware servers and hardware tokens. The Authy application installs on your mobile device or in your browser and provides Time-based One Time Passwords (PIN codes) on demand. Since Authy TOTP codes do not require a mobile network connection or an Internet connection, they are immune from gaps in connectivity to the network. Authentication on the IBM i platform simply requires opening the Authy application on your phone, viewing the one time code, and entering it on your IBM i signon screen. Alliance Two Factor Authentication then verifies the code with the Authy service and allows access to the IBM i platform.
Townsend Security’s support for Authy means that IBM i (iSeries, AS/400) users can now deploy a popular and low-cost two factor authentication product without the expense of back-end hardware servers and hardware tokens. The Authy application installs on your mobile device or in your browser and provides Time-based One Time Passwords (PIN codes) on demand. Since Authy TOTP codes do not require a mobile network connection or an Internet connection, they are immune from gaps in connectivity to the network. Authentication on the IBM i platform simply requires opening the Authy application on your phone, viewing the one time code, and entering it on your IBM i signon screen. Alliance Two Factor Authentication then verifies the code with the Authy service and allows access to the IBM i platform.
 Today Townsend Security, a leading authority in data privacy solutions, and MongoDB, the database for modern applications, today announced Alliance Key Manager has certified against MongoDB Enterprise.
Today Townsend Security, a leading authority in data privacy solutions, and MongoDB, the database for modern applications, today announced Alliance Key Manager has certified against MongoDB Enterprise.


 Securing Data in MongoDB Enterprise with Alliance Key Manager
Securing Data in MongoDB Enterprise with Alliance Key Manager

