 We’ve had an upsurge in interest recently in our Alliance LogAgent solution for the IBM i (AS/400) platform. This solution sends security events from the IBM i in real time to log collection servers and SIEM solutions. As I’ve talked to IBM i customers, I am beginning to appreciate how difficult it is to get IBM i security information into a usable format so that events can be collected and monitored. The challenges are big:
We’ve had an upsurge in interest recently in our Alliance LogAgent solution for the IBM i (AS/400) platform. This solution sends security events from the IBM i in real time to log collection servers and SIEM solutions. As I’ve talked to IBM i customers, I am beginning to appreciate how difficult it is to get IBM i security information into a usable format so that events can be collected and monitored. The challenges are big:
- Data format – IBM security events are in internal IBM format, not syslog format.
- Multiple sources – Security events get collected in a variety of locations, almost always in an internal and proprietary IBM format.
- Timeliness – Tools are lacking to collect security events in real-time, increasing the security exposure.
- Communications – There are no native syslog UDP, TCP or SSL TCP communications facilities.
- Data completeness – While it is possible to print security information using IBM tools, critical information is missing from reports.
Here is a really good example of this last point. I can use the Display Audit Journal Entry command (DSPAUDJRNE) to print a report of user ID and password failures. Here is a bit of what that report looks like:
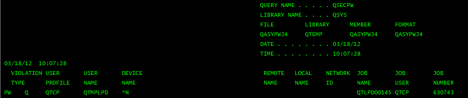
Can you imagine a SIEM solution or poor network administrator trying to get useful information from this? Fields are not easily identified and extracted, and most SIEM query tools would have a really hard time extracting the meaning from this report. There are user ID and password failures here, but hard to parse them out.
And one of the most important pieces of information is missing. Can you see what it is?
Right, the IP address of the originator of the error. SIEM solutions are good at correlating events if they know where they are coming from. The IP address is critical for accomplishing this. This report could probably tell you when you are under attack, but not where it is coming from and certainly not in real-time.
Our Alliance LogAgent solution solves all of these problems. Events are extracted from all of the relevant sources, in real time, converted to standard syslog format, and communicated using your choice of UDP, TCP, or secure TLS communications to your log server. And, Yes, the IP address is in the event! Here is an example of a PW event as it is processed by Alliance LogAgent:
<118>Sep 20 15:47:11 S10125BA QAUDJRN:[PW@0 event="PW-Invalid user or password" event_type="Q-Signon failed profile disabled" user_profile="QTCP" device="*N" jrn_seq="002273092" timestamp="20120120154711021000" job_name="QTLPD00145" user_name="QTCP" job_number="630743" ip_addr="10.0.1.205" port="15427"]
This is caviar to your SIEM solution! Real time alerts, event queries, and forensics become a snap when you get the right data into your SIEM solution. And real time system monitoring is one of the top recommendations by security professionals to keep your IBM i (AS/400) safe.
I’m proud of our system logging solution for the IBM platform. Our customers have deployed the solution in under an hour starting from the time they do the download from our web site.
Patrick

 It is increasingly apparent how much smaller the world is getting. As long as there has been human civilization, technology has decreased the vast uncertainty of our universe. We are a far cry from the 15th century, when the European elite didn’t know North America existed. Bell invented the telephone, and suddenly months of correspondence could be condensed into a five minute chat. Then came the personal computer and opportunities for seemingly everything in the world were endless. As the complete paradigm shift to cyber data happened, the increasing dependability on what is put on the net became a way of life.
It is increasingly apparent how much smaller the world is getting. As long as there has been human civilization, technology has decreased the vast uncertainty of our universe. We are a far cry from the 15th century, when the European elite didn’t know North America existed. Bell invented the telephone, and suddenly months of correspondence could be condensed into a five minute chat. Then came the personal computer and opportunities for seemingly everything in the world were endless. As the complete paradigm shift to cyber data happened, the increasing dependability on what is put on the net became a way of life.
 In today’s environment, most organizations fall under multiple compliance regulations. If you are taking credit cards, you need to meet PCI data security standards. If you are in the health care industry, you have HIPAA and HITECH to work on. If you are in the banking industry or any financial segment, you have the Graham Leech Bliley Act (GLBA) and FFIEC requirements to meet. All of us have to deal with state and federal privacy regulations about protecting data.
In today’s environment, most organizations fall under multiple compliance regulations. If you are taking credit cards, you need to meet PCI data security standards. If you are in the health care industry, you have HIPAA and HITECH to work on. If you are in the banking industry or any financial segment, you have the Graham Leech Bliley Act (GLBA) and FFIEC requirements to meet. All of us have to deal with state and federal privacy regulations about protecting data.


 In June 2010, a computer worm called “Stuxnet” made worldwide news when it infiltrated Iranian science labs. Many of Iran’s industrial facilities including Natanz, were seriously harmed as a result of this worm. Uranium enrichment is a project that many global nuclear outfits are working on. The idea is to create a higher concentration of the Uranium isotope U-238 to make for a more reactive metal. The source codes for all of these machines are stored on computers, so they are run by what the computers are instructing them to do. When the bug hit, the sophisticated centrifuges began spinning too fast causing the machines to self-destruct.
In June 2010, a computer worm called “Stuxnet” made worldwide news when it infiltrated Iranian science labs. Many of Iran’s industrial facilities including Natanz, were seriously harmed as a result of this worm. Uranium enrichment is a project that many global nuclear outfits are working on. The idea is to create a higher concentration of the Uranium isotope U-238 to make for a more reactive metal. The source codes for all of these machines are stored on computers, so they are run by what the computers are instructing them to do. When the bug hit, the sophisticated centrifuges began spinning too fast causing the machines to self-destruct.
 Some years ago, during an “in between” period of my life, I drove a taxi in Houston, Texas. It was one of those enriching life experiences (this means it left scars), and a recent security newsletter from Bruce Schneier had me thinking about it again.
Some years ago, during an “in between” period of my life, I drove a taxi in Houston, Texas. It was one of those enriching life experiences (this means it left scars), and a recent security newsletter from Bruce Schneier had me thinking about it again.
 As more and more organizations are falling under compliance regulations, IT managers are being tasked with finding a secure Managed File Transfer solution to secure and automate data in motion with their trading partners, customers, employees and internal systems. There are a few out there, but how do you decide which is the best for your organization? I recently sat down with Patrick Townsend, Founder & CEO to learn more about the core components of a Managed File Transfer solution. Here is what he has to say:
As more and more organizations are falling under compliance regulations, IT managers are being tasked with finding a secure Managed File Transfer solution to secure and automate data in motion with their trading partners, customers, employees and internal systems. There are a few out there, but how do you decide which is the best for your organization? I recently sat down with Patrick Townsend, Founder & CEO to learn more about the core components of a Managed File Transfer solution. Here is what he has to say:

 This is what a Database Administrator said to me recently when I attended a SQL Saturday event on the Microsoft campus in Redmond, Washington. And I’m hearing that a lot from IT directors and CIOs in the financial and medical sectors. Microsoft SharePoint is a wonderful collaboration tool, and it supports a number of versions and deployment options. These options run the gamut from free versions that ship with Windows Server, to versions tailored to the Microsoft Office suite of applications, to web portals. And an industry has grown up around installing, customizing, and hosting SharePoint.
This is what a Database Administrator said to me recently when I attended a SQL Saturday event on the Microsoft campus in Redmond, Washington. And I’m hearing that a lot from IT directors and CIOs in the financial and medical sectors. Microsoft SharePoint is a wonderful collaboration tool, and it supports a number of versions and deployment options. These options run the gamut from free versions that ship with Windows Server, to versions tailored to the Microsoft Office suite of applications, to web portals. And an industry has grown up around installing, customizing, and hosting SharePoint.