We all know that in today’s climate of information technology, the steps we take to secure sensitive data must go beyond simply using passwords and firewalls. However, many organizations are still hesitant to adopt encryption and encryption key management, even when it’s mandated by industry regulations and is the strongest safeguard against a data breach. In our new eBook, we’re asking, “What’s preventing you from implementing strong data security?”
 Encryption and encryption key management have a reputation for being costly and difficult. This reputation causes organizations a lot of fear. Many people ask themselves, will an encryption and key management project overtake my time and resources? Will it consume my budget? Will it slow down my systems? The good news is, with evolving technology these fears are now based simply on misconceptions. For many organizations, especially those using the cloud, the cost and ease of an encryption and key management project has been greatly improved due to reduced complexity of the Technology. Also, the idea that encryption and key management severely affect performance is usually a misconception of how encryption and key management work in an IT environment, and with proper key management technology, the fear of losing an encryption key is nearly void.
Encryption and encryption key management have a reputation for being costly and difficult. This reputation causes organizations a lot of fear. Many people ask themselves, will an encryption and key management project overtake my time and resources? Will it consume my budget? Will it slow down my systems? The good news is, with evolving technology these fears are now based simply on misconceptions. For many organizations, especially those using the cloud, the cost and ease of an encryption and key management project has been greatly improved due to reduced complexity of the Technology. Also, the idea that encryption and key management severely affect performance is usually a misconception of how encryption and key management work in an IT environment, and with proper key management technology, the fear of losing an encryption key is nearly void.
To learn how to overcome the top five most common fears of implementing encryption and encryption key management, check out the excerpts from the new eBook below!
1. Will encryption & key management affect performance on my systems?
One of the most common fears about encryption and encryption key management is that encrypting data will severely impact system performance. It’s true that encryption will have some impact on performance, but if done right, encryption should rarely impact your performance more than 2-4%. Performance impacts can also vary based on the amount of data you’re encrypting and whether you’re doing whole disk, column and field level, or application level encryption. Because encrypting data at any level is difficult to get right, many organizations that attempt “do-it-yourself” encryption solutions see a much higher performance impact…
2. Encryption & key management is too complicated
In the past, managing encryption keys was incredibly complicated as well as costly and time consuming. Specialized solutions had to be developed for an organization’s specific IT infrastructure in order to provide access as well as limit control to certain users. These projects would take months of development to complete and be complicated for an administrator to manage.
Today encryption and key management is easy with SDKs, sample language libraries, and ready-to-use client side applications provided by key management vendors. Little-to-no programming is required by the user at all, and keys can be automatically generated so that complex configuration steps are entirely eliminated...
3. What if I lose a key?
One of the greatest fears of encryption is key loss. If an organization encrypts data and then loses the encryption key, unless they’ve made a backup of the key or restore access to the key, the data becomes permanently unusable. This could be a nightmare for those encrypting millions of pieces of data, such as customer credit card information that needs to be read and retrieved daily in order to complete transactions and maintain business continuity.
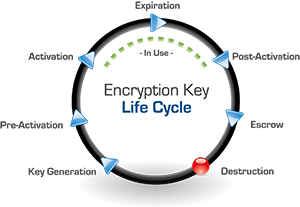
While the fear of losing a key is legitimate, the keystone of a successful encryption solution is encryption key management, which is the primary solution for managing, storing, and most of all, protecting encryption keys...
4. Encryption key management is too expensive
Today, a reputable encryption key management vendor will never overcharge you or have hidden fees or costs, and will provide you with information to help you find the right solution, free of charge.
The climate of data security is always changing. However, one thing we know for sure is that hackers are never going away. Hacking is a profitable and growing industry. Firewalls and strong passwords are no longer considered adequate means for protecting sensitive data...
5. My IT staff is too small!
Another common fear is that an organization’s IT department is too small to handle a project like implementing encryption and encryption key management. Encryption key management has a reputation for being incredibly difficult to implement, and many administrators assume that the time and manpower that must be diverted to complete an encryption key management project isn’t worth doing the project at all.
Although this reputation held true ten years ago, encryption key management today has become so simple that in many scenarios it can be implemented in just a few minutes…
To continue reading, download "Overcome the Top 5 Fears of Encryption and Key Management" today.