Secrets Management SaaS for CMS Systems Including Drupal and WordPress
Secrets Management SaaS for CMS Systems Including Drupal and WordPress
“With easy and flexible deployment options, Alliance Key Manager has allowed Lockr to offer affordable secrets management to Drupal and WordPress users.”
- Chris Teitzel, Lockr CEO
Lockr
Lockr is dedicated to removing barriers to implementing sound security practices. By building, and making available, security solutions that are easy to deploy and affordable, Lockr fulfills its commitment to helping companies and organizations, of all sizes, protect the data of their customers, their partners, their employees and their daily operations. Lockr has made secrets management available to the Drupal content-management framework since 2015 and to the WordPress platform since 2016.
The Challenge: OEM, Compliant, Encryption Key Management
 As a company who protects private information for leading companies across all verticals, Lockr knew that the only way they could be confident in their Software as a Service (SaaS) offering was to back it with a FIPS 140-2 compliant encryption key management solution. FIPS compliance meant that the solution was based on industry standards and has undergone a stringent review of the encryption source code and development practices. Further, as a growing organization whose goal was to offer an affordable service, Lockr needed a relationship with a company that offered them a flexible OEM partnership.
As a company who protects private information for leading companies across all verticals, Lockr knew that the only way they could be confident in their Software as a Service (SaaS) offering was to back it with a FIPS 140-2 compliant encryption key management solution. FIPS compliance meant that the solution was based on industry standards and has undergone a stringent review of the encryption source code and development practices. Further, as a growing organization whose goal was to offer an affordable service, Lockr needed a relationship with a company that offered them a flexible OEM partnership.
“Often times, because of the cost and complexity of secrets management solutions, organizations struggle and cross their fingers they don’t experience a data breach. From the inception, Lockr’s mission has been to offer affordable and easy to use security so that even the smallest websites can have the same protection as large enterprises.”
The Solution
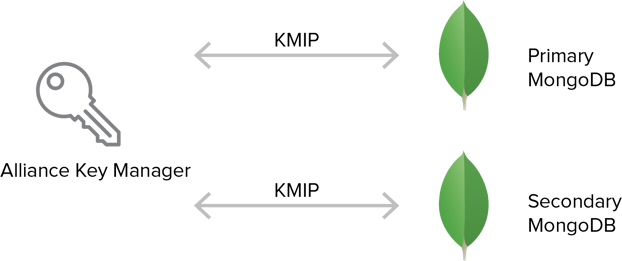
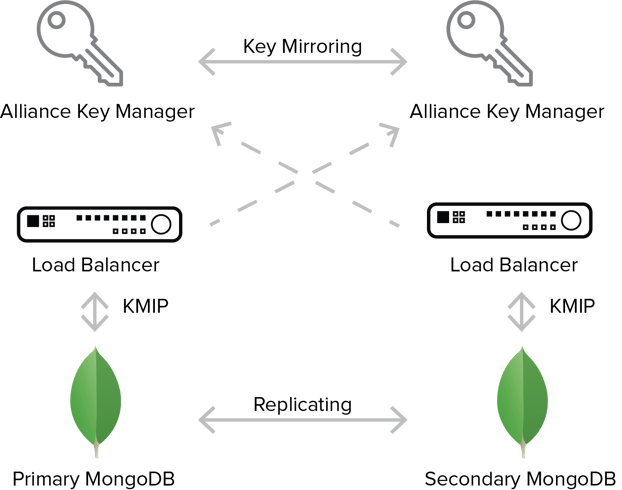
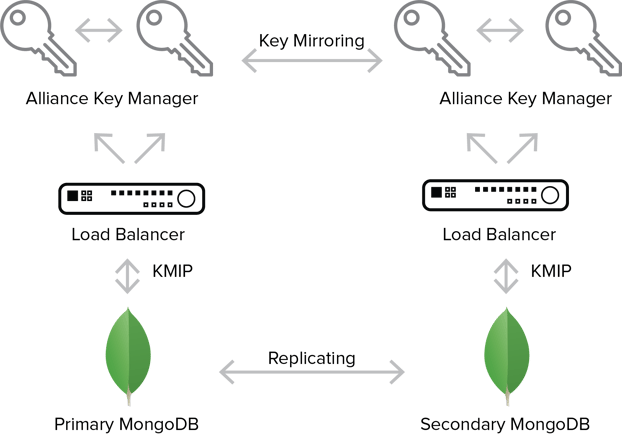
Alliance Key Manager in AWS
As a company that protects secrets (APIs, tokens, applications secrets, and encryption keys), Lockr offers their customers a service to better secure data without the costs associated with purchasing and managing dedicated servers. By partnering with Townsend Security, Lockr was able back their service with a proven solution that is in use by enterprises worldwide.
After choosing Amazon Web Services (AWS) as their cloud service provider (CSP), Lockr rapidly deployed Alliance Key Manager in AWS in regions all over the globe. “The combination of Alliance Key Manager and AWS allows Lockr to offer SLAs and support plans that the most demanding organizations require. Working with Alliance Key Manager in AWS is painless - we just launch an AMI and can instantly begin developing and testing. Even though our infrastructure is in AWS, our service is multi-cloud and multi-platform.”
Integration with CSP and Hosting Providers
Lockr provides secrets management to Drupal and WordPress environments hosted anywhere - Pantheon, Acquia, or even self-hosted. Businesses often turn to CSPs and hosting providers because they don’t want to manage another piece of infrastructure or have the expertise. Now they can improve security by turning to Lockr for secrets management as a service.
“While a hosting provider can ensure that their infrastructure is safe, it doesn’t extend to the applications that you run on top of it.” Because of this, providers are starting to refer Lockr to their customers, especially those in finance, healthcare and higher education industries. “When you look at reasons people chose to work with a hosting company, they are looking for people to do all the DevOps work - including security - that they don’t know how to do. Site developers know they need to be safe and Lockr, backed by Alliance Key Manager from Townsend Security, makes that happen.”
Better Securing eCommerce
When businesses deploy eCommerce solutions like Commerce Guys in Drupal or WooCommerce in WordPress to take themselves “out of the sensitive data realm” they are often surprised to learn they are collecting personally identifiable information (PII) such as email address, name, and zip code that they ARE responsible for protecting. Further, services like these use an API to connect to the CMS that needs to be protected. With Lockr’s architecture, it is easy for eCommerce providers to give their users comprehensive security, beyond a credit card transaction.
“The type of SMBs that deploy eCommerce services have a high need for security, but often a small budget. These companies make up a large portion of the web, but often enterprise security solutions are out of reach due to their technical capabilities and cost. They need to have a solution that scales with them.” By calling the APIs offered in Alliance Key Manager, Lockr is able to provide their users with the added security they require to prevent a data breach.










 With all of the security breaches you hear of in the news and the occurrence of these incidents becoming more widespread, how can you be sure your customer’s credit card information remains secure? This is the purpose of PCI DSS (Payment Card Industry Data Security Standards) as it pertains to all merchants who accept credit cards, irrespective of their annual revenue and credit card transaction volume. Even with this mandatory requirement, a vast majority of organizations are still struggling to maintain PCI compliance, and the process is costing companies a great deal in consulting fees to address the root cause of PCI audit failures. By being proactive in assessing the areas of weakness when undergoing a PCI Audit, especially for the first time, companies can avoid the frustrations of a failed audit and be well on their way to continued PCI compliance.
With all of the security breaches you hear of in the news and the occurrence of these incidents becoming more widespread, how can you be sure your customer’s credit card information remains secure? This is the purpose of PCI DSS (Payment Card Industry Data Security Standards) as it pertains to all merchants who accept credit cards, irrespective of their annual revenue and credit card transaction volume. Even with this mandatory requirement, a vast majority of organizations are still struggling to maintain PCI compliance, and the process is costing companies a great deal in consulting fees to address the root cause of PCI audit failures. By being proactive in assessing the areas of weakness when undergoing a PCI Audit, especially for the first time, companies can avoid the frustrations of a failed audit and be well on their way to continued PCI compliance.