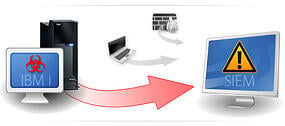
 The Alliance LogAgent Solution for system logging on the IBM iSeries is able to grab log messages out of a variety of places such as your system's audit journal, (QAUDJRN), your history log (QHST), and system operator messages (QSYSOPR) and format them to either a standardized Syslog format, in this case RFC3164 or Common Event Format (CEF). Once formatted, we pass the messages over to the communications module that handles the transmission of the messages to your waiting log collection server using either the UDP, TCP or SSL/TLS protocol.
The Alliance LogAgent Solution for system logging on the IBM iSeries is able to grab log messages out of a variety of places such as your system's audit journal, (QAUDJRN), your history log (QHST), and system operator messages (QSYSOPR) and format them to either a standardized Syslog format, in this case RFC3164 or Common Event Format (CEF). Once formatted, we pass the messages over to the communications module that handles the transmission of the messages to your waiting log collection server using either the UDP, TCP or SSL/TLS protocol.
LogAgent can send to any collection server that is listening for messages. You simply assign either a remote host or IP address of the waiting server as well as the port number. Ideally you would want a SIEM (like from LogRhythm, Solutionary, or SolarWinds, for example) running on that server to read the messages that are received, sort them and send out alarms to your security team when dubious messages arrive.
 More often than not you'll want to use the Syslog format as it is generally accepted. The RFC3164 format that we use is composed of three parts. The first part is called the PRI, the second part is the HEADER, and the third part is the MSG.
More often than not you'll want to use the Syslog format as it is generally accepted. The RFC3164 format that we use is composed of three parts. The first part is called the PRI, the second part is the HEADER, and the third part is the MSG.
The PRI part is the Priority value and begins the log message. Its value is contained within angled brackets and is either two or three digits in length. It is comprised of the Facility value and the Severity level of the message. The Priority value is calculated by first multiplying the Facility number by 8 and then adding the numerical value of the Severity. (Example: <40> )
The second part of the message is the header which will contain a timestamp, and an indication of the hostname or IP address of the device it originated from. The MSG part will fill out the remainder of the syslog packet and contain the generated message and the text of the message.
Here is a quick sample of a log message in RFC 3164 format.
<118> Apr 18 16:32:58 10.0.1.11 QAUDJRN: [AF@0 event="AF-Authority failure" violation="A-Not authorized to object" actual_type="AF-A" jrn_seq="1001363" timestamp="20120418163258988000" job_name="QPADEV000B" user_name="TESTFORAF" job_number="256937" err_user="TESTFORAF" ip_addr="10.0.1.23" port="55875" action="Undefined(x00)" val_job="QPADEV000B" val_user="TESTFORAF" val_jobno="256937" object="AFTEST" object_library="CUS9242" object_type="*FILE" pgm_name="" pgm_libr="" workstation=""]
If you're using a SIEM such as ArcSight who is expecting logs messages in the Common Event Format (CEF) you can easily switch the formatting from the configuration menu of LogAgent to send in this manner. Much like the RFC 3164 version, the message contains a timestamp and hostname or IP address at the beginning. This is followed by the Extension part of the message and is really a placeholder for additional fields. Some common fields you'll find are CEF version, Device Vendor, Device Product Severity and Signature ID just to name a few.
Example of what a CEF formatted log message looks like.
Feb 29 15:47:25 10.0.1.43 CEF: 0|PATownsend|IBM-QAUDJRN|1.28|1007|CO-Create object|4|msg=CO-Create object act=N-Create of new object actual_type=CO-N jrn_seq=102361 timestamp=20120229154725823000 dproc=ICC suser=MVAGANEK job_number=638012 eff_user=MVAGANEK object=X_BIGNUM object_library=ICAPITST object_type=*MODULE object_attrCLE
It's always a good idea to check with the team managing your log collection server to see what format they are expecting log messages to arrive in. Hopefully having a clearer understanding of what your choices are will help make the task of deploying system logging on your AS/400 smoother and easier to satisfy section 10 of PCI DSS compliance. If you haven't yet, download a free 30-day evaluation of our Alliance LogAgent for IBM i system logging software. Our customers have deployed the solution in under an hour from the time they download the evaluation from our website!


 IBM announced recently the end of support date for V5R4. This has prompted many IBM i shops running this older OS to upgrade to a newer release - either V6R1 or V7R1. Traditionally, we have seen that most IBM i administrators upgrade just one release forward. In this particular case, we recommend going to V7R1. Not only is upgrading to V7R1 a fully supported path by IBM, there are security reasons. I recently sat down with Patrick Townsend, Founder & CEO, to discuss IBM i V7R1 and how Townsend Security can help organizations take advantage of FIELDPROC, a new feature that allows companies to encrypt their sensitive data without changing their applications.
IBM announced recently the end of support date for V5R4. This has prompted many IBM i shops running this older OS to upgrade to a newer release - either V6R1 or V7R1. Traditionally, we have seen that most IBM i administrators upgrade just one release forward. In this particular case, we recommend going to V7R1. Not only is upgrading to V7R1 a fully supported path by IBM, there are security reasons. I recently sat down with Patrick Townsend, Founder & CEO, to discuss IBM i V7R1 and how Townsend Security can help organizations take advantage of FIELDPROC, a new feature that allows companies to encrypt their sensitive data without changing their applications.


 Whenever I am asked what Townsend Security does I have to explain that we aren't in the business of deploying security cameras or contracting out shopping mall guards. We are actually a software security vendor for the IBM i (AS/400) platform. It's usually at this point the recipient's eyes glaze over and I am left simply stating that I am in the 'computers' field. On occasion however I will be chatting with a colleague who also works in the tech industry who will scoff when they hear the name AS/400, iSeries, Systemi (take your pick). Often I'll hear, "Whoa, that's legacy technology. You have customers still using that platform?"
Whenever I am asked what Townsend Security does I have to explain that we aren't in the business of deploying security cameras or contracting out shopping mall guards. We are actually a software security vendor for the IBM i (AS/400) platform. It's usually at this point the recipient's eyes glaze over and I am left simply stating that I am in the 'computers' field. On occasion however I will be chatting with a colleague who also works in the tech industry who will scoff when they hear the name AS/400, iSeries, Systemi (take your pick). Often I'll hear, "Whoa, that's legacy technology. You have customers still using that platform?"


 We’ve had an upsurge in interest recently in our
We’ve had an upsurge in interest recently in our 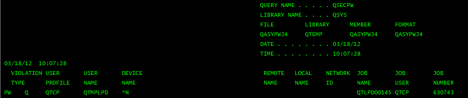
 In today’s environment, most organizations fall under multiple compliance regulations. If you are taking credit cards, you need to meet PCI data security standards. If you are in the health care industry, you have HIPAA and HITECH to work on. If you are in the banking industry or any financial segment, you have the Graham Leech Bliley Act (GLBA) and FFIEC requirements to meet. All of us have to deal with state and federal privacy regulations about protecting data.
In today’s environment, most organizations fall under multiple compliance regulations. If you are taking credit cards, you need to meet PCI data security standards. If you are in the health care industry, you have HIPAA and HITECH to work on. If you are in the banking industry or any financial segment, you have the Graham Leech Bliley Act (GLBA) and FFIEC requirements to meet. All of us have to deal with state and federal privacy regulations about protecting data.
 As more and more organizations are falling under compliance regulations, IT managers are being tasked with finding a secure Managed File Transfer solution to secure and automate data in motion with their trading partners, customers, employees and internal systems. There are a few out there, but how do you decide which is the best for your organization? I recently sat down with Patrick Townsend, Founder & CEO to learn more about the core components of a Managed File Transfer solution. Here is what he has to say:
As more and more organizations are falling under compliance regulations, IT managers are being tasked with finding a secure Managed File Transfer solution to secure and automate data in motion with their trading partners, customers, employees and internal systems. There are a few out there, but how do you decide which is the best for your organization? I recently sat down with Patrick Townsend, Founder & CEO to learn more about the core components of a Managed File Transfer solution. Here is what he has to say: