In a business world that is moving more towards virtualization and cloud environments, the need for strong encryption and proper key management is critical. Due to all the recent and well-publicized data breaches, we all know about the ways your brand can be damaged if you don’t encrypt your data. Let’s look at the benefits of encryption, and three of the ways it can have a positive effect on your business.

Customer Confidence = Loyalty: When it all boils down, building trust in your business is what will make or break relationships with your customers, business partners, and potential investors. After major retail breaches in 2013, a study conducted on 700 consumers showed that the three occurrences that have the greatest impact on brand reputation are data breaches, poor customer service, and environmental disasters. These three incidents were selected ahead of publicized lawsuits, government fines, and labor or union disputes. By being transparent about the ways that you will store and protect their sensitive data (required to operate your business) you will build a level of confidence and trust with your current and potential clients and customers. Using encryption to protect your customers sensitive information is the best way to keep any unauthorized user from successfully using the data if it is accessed. Properly deploying encryption, means you will be sure to use an encryption key manager that separates and securely stores the encryption keys away from the encrypted data. Let your clients know you take data security seriously, and let the would-be thieves know “move along, there is nothing to see here”!
Cloud = Cost Savings: Encryption can help your business move successfully to cloud and virtual environments. Because of the multi-tenant nature, cloud solutions can offer a significant cost savings to most organizations… but what about those other “tenants”, are they able to gain access to your information? What about the treasure trove of information that is attracting more and more hackers? Encryption can make it possible to leverage the benefits and cost savings of the cloud while ensuring the privacy of your sensitive data.
- By using encryption, you can make sure your information is secure when it is “at rest” or “in motion”.
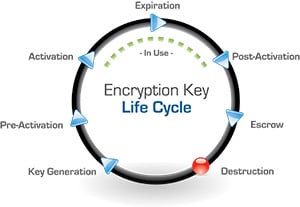
- By properly handling encryption keys with an encryption key manager, you make sure you are the only one able to access your encryption keys.
- By keeping your encrypted data and your encryption keys in separate locations, you remain in control even when your data has left the building.
Customer Compliance = Competitive Advantage: Keeping data secure is the law for many commercial and private organizations. If any sensitive information is stolen or lost, your company may suffer some serious consequences, especially if that information is not encrypted. Using industry standard encryption also helps you meet various compliance regulations and data security standards. Depending on what industry your business is in, different regulations will come into play. As an example, all companies that take credit card payments fall under the Payment Card Industry Data Security Standard (PCI DSS). We all use credit cards and we want assurance that our information is safe. Would you shop online with a company that didn’t take measures to protect your account information?
If a data breach occurs and personally identifiable information is lost, the breached company must notify all their customers who are impacted. Did you know that there are data breach notification laws in 46 of the 50 states? Some regulations have a safe harbor clause, protecting companies from public notification if the stolen data is encrypted and if the encryption keys are not compromised. Along with the frequency, the cost of these breaches continues to escalate: The average cost to an organization for a data breach is up 15% with an average cost of 3.5 million dollars (2014 Ponemon Report). So using encryption to protect data and properly handling key management could save you millions of dollars in the event of a breach. Given the high cost of breach notification doesn't encryption just make sense?
Whether you choose a designated hardware security module (HSM), something designed specifically for virtualized environments (VMware), or data storage in the cloud, encryption and key management solutions can help you:
- Gain competitive advantage and build loyalty by protecting your customers data against access by unauthorized users
- Reduce hardware costs by leveraging virtual environments in the cloud
- Significantly improve your data security strategy while satisfying data compliance and privacy requirements
Overall, data encryption offers many benefits and provides solid protection against potential threats or theft. In addition to the many benefits, encryption is also efficient, easy to use, and affordable! Want to learn more about encryption? Download our eBook “The Encryption Guide”: