Wherever your sensitive data resides - client side applications, secure data centers, or in the cloud - Encrypt it!
 “Sensitive data” is not just credit card numbers and expiration dates anymore. Because of recent data breaches, we know that loyalty information like names, e-mail, physical addresses, phone numbers; personal data like birthdate, social security number... so much information today... now constitutes what we call personally identifiable information (PII) and must be properly protected with encryption no matter it is stored.
“Sensitive data” is not just credit card numbers and expiration dates anymore. Because of recent data breaches, we know that loyalty information like names, e-mail, physical addresses, phone numbers; personal data like birthdate, social security number... so much information today... now constitutes what we call personally identifiable information (PII) and must be properly protected with encryption no matter it is stored.
When it comes to protecting data, look to well-defined industry standards for an encryption algorithm that is reviewed and vetted by cryptographers around the world. Advanced Encryption Standard or AES is the most commonly used encryption algorithm to protect sensitive data. Validated by the National Institute of Standards and Technology (NIST), this standard is referenced in a wide variety of compliance regulations either as a requirement or as a recommendation. However, the AES algorithm is not the secret that we have to defend. Think of encryption as the lock that you put on your front door, and the encryption key is your house key. You don’t tape your house key right next to the lock when you leave in the morning, you take it with you and you protect it from loss or theft. Your unique encryption key is THE secret that you must protect, which can be accomplished using a secure, certified key management solution. Getting encryption key management right is in fact the biggest challenge customers and organizations run into when they start their encryption projects.
When you look at what it takes to properly protect sensitive data with encryption, you immediately find standards (NIST) & best practices for key management, and industry compliance regulations (PCI DSS, HIPAA/HITECH, FFIEC, and state privacy laws) that require proper key management. They all say the same thing: “Do Not Store the Encryption Key on the Same Server as the Encrypted Data”.
Encryption key management is a well-defined process with standards and best practices around managing encryption keys and a formal definition of the encryption key lifecycle.
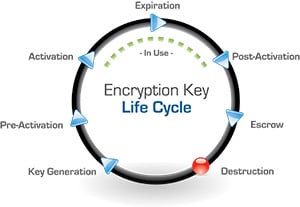
When an encryption key is first generated, or established, it may not be used for some time so it waits in a pre-activation status until it is being actively used. The key will expire after use or based on a set definition and then will go into escrow after post-activation. After that period, the key is generally destroyed.
One way to destroy data is to destroy the encryption key that's protecting it, because if the key is not recoverable neither is that data. Auditors will want to know if you have a process for managing the encryption key through the entire lifecycle, and this is one of the things that a key management solution does for you in a provable way. Beyond the encryption key lifecycle, the key management solution provides access controls for users and groups, in-depth audit trails and system logging with the ability to integrate across multiple platforms, and they must implement a mechanism for dual control and separation of duties to really meet compliance regulations as well as defensible security best practices.
It is also very important for an encryption key manager to provide the option of onboard encryption. The core function of the encryption key management solution is to generate, protect, and distribute encryption keys to authenticated users. If you have a web application or a more exposed cloud environment, retrieving an encryption key may seem risky to you in terms of having that key in your operating environment. With an onboard encryption solution you can send your data to the key manager, name a key, and get that data encrypted or decrypted strictly within the confines of that key management solution. Avoiding the risk of losing encryption keys in a more exposed environment is an important component in a compliance strategy.
Even 10 years ago, encryption key management solutions were very expensive specialized hardware devices and very difficult and time consuming projects. Thankfully, encryption and key management is no longer the development or cost headache it once was. Since IT infrastructures have become very complex environments using different technologies and platforms (60% of Microsoft SQL Server customers are also running Oracle someplace in the organization), a key management solution also needs to address these complexities and protect data wherever it may be. There are still hardware security modules (HSMs) and now there are new options for deployment of cloud-based HSMs, virtual appliances, and true cloud instances of encryption and key management.
Hardware Security Module (HSM) is a physical appliance or security device that is protected and tamper evident. Built for high resiliency and redundancy it has hot swappable rated disc drives, dual power supplies, dual network interfaces, and is deployed in your IT data center.
Cloud HSM is a physical appliance hosted in a secure cloud with real-time encryption key and access policy mirroring. Dedicated HSMs are hosted in geographically dispersed data centers under an ITIL-based control environment and are independently validated for compliance against PCI DSS and SOC frameworks. No access is available to the cloud vendor or any unauthorized user.
Virtual Appliances are the exact same key management solution - the same binary software that runs inside the hardware HSM - available as a VMware instance.
In the Cloud - If you're running on Microsoft Windows Azure or vCloud, the encryption key manager can run as a true cloud instance in a standard cloud or deploy in a virtual private cloud for added data protection for sensitive applications.
Because encryption and key management is so important, we offer all of the options listed above as NIST validated and FIPS 140-2 compliant solutions. We also want to make sure encryption is available everywhere you need it, so at Townsend Security we have a very different philosophy and approach:
-
We think that when you buy an encryption key manager, you should be able to easily deploy the solution, get all your encryption projects done properly, and have very affordable and predictable costs.
-
We understand that we live in a world where budget matters to our customers, so we do not charge client-side fees.
-
We understand that IT resources are limited and have done a huge amount of work to make our solutions easy with out-of-the-box integrations, simplified deployments, and also provide along with our solution ready-made client-side applications, encryption libraries, source code samples, as well as SDKs for developers who need them to get their projects done very quickly.
To learn more about key management and how to properly encrypt sensitive data anywhere you store it, download our latest webinar featuring data security expert Patrick Townsend:

