Last week we posted part one of our two-part series covering XML & Web Services. This second half covers how organizations are currently using web services, how the technology can increase revenue, and how the technology can reduce costs. For even more information, we have made a recorded webinar available titled "XML & Web Services - How to Win More Business."
How are organizations currently using web services?
There are lots of ways web services are being used to help companies do business and make business work well. Definitely in back-office processing, we see orders being placed via web services -- shipment requests, notification of order status, all types of business transactions that you can imagine are quite easily implemented as a web service. So, sort of that fundamental day-to-day operational side of web services are there. And then you see some really creative kind of things. You see things like Microsoft SharePoint which provides a web service based collaboration tool that helps people share information and collaborate on documents. These are powerful technologies that can really be used in a number of different ways. So, really, almost any interaction that you have that involves information is quite susceptible to being engineered through web services.
How can the technology increase revenue?
Well, think of new business. Sometimes, when you want to bring onboard a new customer there is going to be some data interchange that you have to do with that customer. Web services can make that really easy and fast to do. Web services can really be an enabling technology to on-board entirely new sets of customers – perhaps in lateral opportunities. In terms of increasing revenue, that is probably the main way we see XML and web services being deployed.
You mentioned that this technology can also reduce costs. Can you explain?
In today’s world there can still be a lot of manual work as we move data through our various applications. Web services can automate that. We can gain efficiency within our own organizations by automating a lot of these processes. So, again, XML and web services can be the transport mechanism or the enabling technology for these processes to happen automatically. We push out inefficiencies, we automate processes, we make data flow faster, which then can improve customer service. So XML and web services can be an important efficiency tool within an organization as well.
Are there any specific cost savings for our listeners who implement a SharePoint server?
A SharePoint server is a Microsoft server based product that is a collaboration tool and it really lets people in geographically different locations share information in real-time. So you can push a document up to a SharePoint server, someone else can get notified that the document is available, and then immediately take a look and work on it. This is all done with a web services type of implementation. Or imagine you are on an IBM Mainframe where you are running back-office applications. What if your daily reports could automatically be published to a SharePoint server and made immediately available to the people who need them? You can now reduce printing costs, time for the information delivery, and you make that information much easier to share. So this technology is really helpful for pushing cost out of an organization.
Are there any companies we might recognize using your XML?
Sure! PotteryBarn is using the RightNow CRM and they needed a way to do bulk data transfers to a SharePoint server hosted by RightNow. Our Alliance XML/400 was able to do that. In this case, the payload was an Excel CSV file that had to be shared between PotteryBarn and RightNow. Our technology made this sharing take place.
How complex is the implementation of XML and web services technology?
That’s a good question. Let me take that in two parts. XML and web services technologies have a fair amount of complexity in them. You have issues of security with HTTP/HTTPS implementations and you have the complexities of dealing with XML payloads - they have to be parsed properly to extract data and make it useable.
Encryption and encoding becomes an integral part of this technology, so there are a fair amount of really complex technologies integrated into a web services solution. However, the actual solutions that get deployed don’t have to be complex.
For example, in Alliance XML/400 we make the implementation of the client and server applications very simple. They are natural native interfaces on the IBM i that any developer can use if they wish. So in our solution we tried to hide the complexities of all these technologies in the solution itself, so that our customers don’t have to deal with that. I think that deploying XML and web services with our product is a very straightforward and easy thing to do.
We have had people in a very short period of time get up and running with integration with their customers – in as little as a couple of days. This is something that can be deployed quickly. Good solutions hide those complexities so that people can get on with doing business and not spend their time fussing around with the technology itself.
This has been some great information. Is there anything else you would like to say before we are done?
XML and web services are really enabling tools. We are living today in a difficult economic time and yet the most successful companies are moving forward. They are working to engage new opportunities, to reduce cost out of their organizations, and XML and web services technologies can help with this process. So, being positive and looking for opportunities and being sure to look at the payback for web services as part of the whole picture is really important.
For more information on XML & Web Services, view our webinar titled "XML & Web Services - How to Win More Business."




 Much like going to the gym, not many people wake up in the morning and say that they want to start an encryption project. It can take a little knowledge and some hard work to be done correctly. But the results of both provide benefits far beyond their initial investment.
Much like going to the gym, not many people wake up in the morning and say that they want to start an encryption project. It can take a little knowledge and some hard work to be done correctly. But the results of both provide benefits far beyond their initial investment.

 With the growing demand for regulatory compliance and concern for data privacy, organizations are taking advantage of encryption as a way to provide a "defense in depth" solution. This approach is often impractical using only database encryption management tools alone. Townsend Security has addressed this with their Alliance Key Manager Hardware Security Module (HSM). Alliance Key Manager is a FIPS 140-2 certified solution that stores encryption keys on a hardware appliance. This is a more secure approach and better meets compliance requirements because encryption keys do not reside with the encrypted data.
With the growing demand for regulatory compliance and concern for data privacy, organizations are taking advantage of encryption as a way to provide a "defense in depth" solution. This approach is often impractical using only database encryption management tools alone. Townsend Security has addressed this with their Alliance Key Manager Hardware Security Module (HSM). Alliance Key Manager is a FIPS 140-2 certified solution that stores encryption keys on a hardware appliance. This is a more secure approach and better meets compliance requirements because encryption keys do not reside with the encrypted data.
 Last week we hosted a well-attended webinar titled "
Last week we hosted a well-attended webinar titled " When encrypting data, the most widely accepted cryptographic standard is the Advanced Encryption Standard (AES).
When encrypting data, the most widely accepted cryptographic standard is the Advanced Encryption Standard (AES). There are several potential problems related to the use of the CUSP mode of AES encryption.
There are several potential problems related to the use of the CUSP mode of AES encryption.
 System logging has become one of the most essential tasks of contemporary corporate IT. Several IT standards and regulations, primarily in the interest of traceability (e.g.: PCI-DSS, SOX, etc.) now require it.
System logging has become one of the most essential tasks of contemporary corporate IT. Several IT standards and regulations, primarily in the interest of traceability (e.g.: PCI-DSS, SOX, etc.) now require it.

 The Advanced Encryption Standard (AES) is the standard for data encryption adopted by the NIST in 2001. This encryption standard replaced the earlier Data Encryption Standard (DES). The DES encryption standard became weaker due to the advancing power of computer systems. The NIST began a process in the late 1990’s to find a replacement for DES. After a lengthy examination of several alternatives, the AES standard for encryption was adopted and codified as FIPS-197. AES encryption is now the de-facto standard for strong data encryption.
The Advanced Encryption Standard (AES) is the standard for data encryption adopted by the NIST in 2001. This encryption standard replaced the earlier Data Encryption Standard (DES). The DES encryption standard became weaker due to the advancing power of computer systems. The NIST began a process in the late 1990’s to find a replacement for DES. After a lengthy examination of several alternatives, the AES standard for encryption was adopted and codified as FIPS-197. AES encryption is now the de-facto standard for strong data encryption. The modern Enterprise uses a wide variety of server platforms from a number of different vendors. In addition, data is exchanged with customers, vendors, and service provides outside the organization. To meet these challenges the
The modern Enterprise uses a wide variety of server platforms from a number of different vendors. In addition, data is exchanged with customers, vendors, and service provides outside the organization. To meet these challenges the 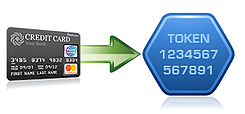 As companies work to meet regulatory requirements to protect Personally Identifiable Information (PII), one option to minimize the risk of loss is to replace sensitive data with a non-sensitive replacement value, or “token.”
As companies work to meet regulatory requirements to protect Personally Identifiable Information (PII), one option to minimize the risk of loss is to replace sensitive data with a non-sensitive replacement value, or “token.” 