Download Podcast |
Today, data security is more important than ever. We live in world now where organizations of every size - from small companies to large global companies – need to make sure their sensitive data is safe. The bad guys are getting much better with more sophisticated attacks. Even mid-sized companies are now targets. So, with the most up-to-date security features included in IBM i 7.1 (V7R1), why would you still be using or consider using the V6R1 release? I recently sat down with Patrick Townsend, Founder & CEO, to discuss the latest IBM i OS and the security reasons a company who is on an upgrade path from V5R4 should bypass V6R1 and install V7R1.
What do you have to say to the company who traditionally moves up just one release? For example the company that would just upgrade to V6R1 because they feel that it has all the kinks worked out.
Well, I understand that motivation and I have been in that seat before. OS upgrades are always something you want to be very cautious about - whether you are talking about your IBM i or even your Linux, UNIX, and Windows servers. You know that a certain number of bugs will get worked out after a new release has come into the market and you tend to be a little cautious about applying the latest release upgrade. Having been released for over a year, V7R1 is now pretty mature and I haven’t heard of any significant upgrade problems.
IBM i users that are on V5R4 know that IBM recently announced the end of support date for that release (which means maintenance and support will stop in about a year) and people will need to upgrade. There are two reasons it is a good idea to jump past V6R1 straight and to V7R1. First, it is a fully supported path by IBM. Second, there are security benefits to making that jump. You are getting significant new security features in V7R1 that you won’t see in V6R1. I know that there are external factors that sometimes influence moving forward on releases. Some software vendors may not be ready for V7R1 and this can represent a significant barrier in terms of getting to the latest release of the operating system. If you have not yet begun a discussion with your software vendors on whether they have certified their software on V7R1, now is the time to do that. IBM makes it very easy for a software vendor to test their software on a pre-release version of the operating system. We do that, and your other software vendors should be doing that too, well before IBM releases a new version of the operating system. This is one time that you should balance the security benefits of V7R1 against the cautionary approach of going only to V6R1, which will be just one step for many people.
Download our podcast “IBM i Security: Skip V6R1 and Upgrade to V7R1” for more information on the security reasons that you should go straight to V7R1. Additionally, we will discuss how Townsend Security can help you take advantage of FIELDPROC, a new addition to V7R1, which allows companies to encrypt their sensitive data without changing their applications.



 In June 2010, a computer worm called “Stuxnet” made worldwide news when it infiltrated Iranian science labs. Many of Iran’s industrial facilities including Natanz, were seriously harmed as a result of this worm. Uranium enrichment is a project that many global nuclear outfits are working on. The idea is to create a higher concentration of the Uranium isotope U-238 to make for a more reactive metal. The source codes for all of these machines are stored on computers, so they are run by what the computers are instructing them to do. When the bug hit, the sophisticated centrifuges began spinning too fast causing the machines to self-destruct.
In June 2010, a computer worm called “Stuxnet” made worldwide news when it infiltrated Iranian science labs. Many of Iran’s industrial facilities including Natanz, were seriously harmed as a result of this worm. Uranium enrichment is a project that many global nuclear outfits are working on. The idea is to create a higher concentration of the Uranium isotope U-238 to make for a more reactive metal. The source codes for all of these machines are stored on computers, so they are run by what the computers are instructing them to do. When the bug hit, the sophisticated centrifuges began spinning too fast causing the machines to self-destruct.


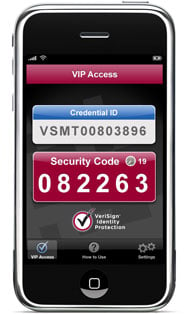 One thing that jumped out at me at this year’s RSA conference in San Francisco was the number of new vendors showing off mobile identification solutions. There were at least four new vendors of mobile-based two factor authentication solutions, and one regular exhibitor with a new entry in this area. These vendors didn’t have the biggest booths or the most lavish give-aways, but as a category they certainly made a big splash.
One thing that jumped out at me at this year’s RSA conference in San Francisco was the number of new vendors showing off mobile identification solutions. There were at least four new vendors of mobile-based two factor authentication solutions, and one regular exhibitor with a new entry in this area. These vendors didn’t have the biggest booths or the most lavish give-aways, but as a category they certainly made a big splash.