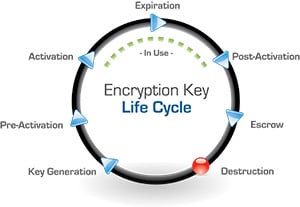
As we discussed in the webinar and latest blog on Encryption & Key Management Everywhere You Need It, sensitive data needs to be protected wherever it resides!
Proper encryption & key management can help you meet compliance requirements, and improve your data security posture across multiple platforms or environments. After the webinar, we had a number of questions asked by attendees and answered by security expert Patrick Townsend. Here is a recap of that Q&A session:
Q: Is there any limit to the number of servers that I can hook up to your encryption key manager?
Patrick: There are no restrictions, and no license constraints on our encryption & key management solution. We don't meter or count the number of client-side platforms that connect to our Alliance Key Manager, so you can hook up as many client side applications, servers, and processors as you need to. This is one of the things I think is different about how we approach encryption and key management with our customers. We also know the applications you are running today may not be the applications you need to be running tomorrow and we really want you to deploy encryption to all your sensitive data and scale up when & where you need it.
Q: With the various platforms that I can deploy an encryption key manager in, how do I know which one is right for me?
Patrick: There are several factors that will come in to play when deciding where you deploy your key management:
Compliance regulations that you need to meet can be a factor in whether you deploy an Hardware Security Module (HSM) or a cloud HSM or a virtualized instance. If you are working with an auditor or going through a QSA audit, you'll want to have a conversation with them to understand their expectation from a compliance point of view around where you deploy your encryption key manager.
Risk tolerance will also come into play. You may have a security group within your organization with strong feelings about how to deploy encryption key management and how to mitigate risk. If you have large amounts of sensitive data to protect you might decide to deploy an HSM in your secure data center. If you're dealing with a very small amount of data and you do not process credit cards or personally identifiable information, your risk assessment may indicate a cloud deployment.
Budget is certainly always a factor to consider. It is important to consider the cost benefits of security however, we all understand that leaving our data in the clear is no longer an option. It is a matter of understanding your industry regulations and risk assessment, then deciding what encryption and key management to deploy.
While they are generally the most secure solution, Hardware Security Modules (HSMs) can be more expensive than a virtual environment, dedicated cloud instance, or virtual private cloud. Once you look at all the factors that affect your company, we will be there with the right solution that will work for your needs.
Q: Does Townsend Security provide guidance on how to get the best performance with my operating environment?
Patrick: Because every enterprise operational environment is different, we provide guidance around performance with our encryption key management solution. With every one of our solutions we offer complimentary 30-day product evaluations and encourage our customers to do proof of concepts with their applications. We are serious about making this process simple, and our customers can download the actual instance in evaluation mode, run it with their applications, test the actual solution, and truly evaluate performance in their specific environment. Performance metrics will be moderated by a number of factors within your specialized environment, your network, and your processing platform.
Q: I have data that needs to be encrypted in a cloud other than Amazon or Windows Azure, can your product help me with this?
Patrick: Yes, we can. First of all, following best practices, you want to keep your encryption keys separate from the data they are protecting. You may have data in a cloud platform, but choose to run your encryption key management solution in a different location or a virtual private cloud. Let’s say you want to run the key manager in a dedicated cloud HSM or even in your data center. Most top-tier cloud vendors truly support multiple environments for running key management, and we find that our solutions work well for customers who are running in the cloud. We suggest you contact us and have a conversation about options and we can provide guidance about how to deploy a secure solution.
Q: How is Alliance Key Manager Priced?
Patrick: We have a wide set of options for our customers, and are dedicated to helping find affordable solutions. We have perpetual license or subscription options for classic HSMs, Cloud HSM, and virtualized environments. Our cloud offerings are true usage-based subscriptions, so if you're used to deploying in Amazon Web Services or Windows Azure, our encryption & key management solutions will fit that same strategy for pricing.
We really believe that the encryption should go everywhere you need it to go! Your key management should work across a wide set of application environments, and it must be affordable, so that we can all get where we need to be in terms of protecting sensitive data. Regardless of where your data is or what platform you are using, there's a solution that can work for you!
View the complete webinar - Encryption & Key Management Everywhere - to learn about:
- Deploying encryption and key management with an HSM, cloud HSM, virtual appliance or in the cloud
- How protecting data properly is now easier and more affordable than ever
- Factors to consider when deciding which option is right for your organization
- What compliance regulations (PCI DSS etc.) say about the different options
- Challenges for applications running in the cloud or virtual environments

If you have further questions, please list them here in the comment section and we will be sure to get you an answer!
 First, a disclaimer: Only IBM can comment in a definitive way on any Heartbleed vulnerabilities in the IBM i. The following are my opinions based on several years of work on the platform.
First, a disclaimer: Only IBM can comment in a definitive way on any Heartbleed vulnerabilities in the IBM i. The following are my opinions based on several years of work on the platform.

 Security researchers have discovered a vulnerability in certain versions of the very popular OpenSSL application that can lead to the loss of critical sensitive information. The vulnerability is called Heartbleed because if affects the TLS heartbeat function in secure, connections. Because OpenSSL is used by so many web applications, and because this vulnerability can be exploited, the severity is very high.
Security researchers have discovered a vulnerability in certain versions of the very popular OpenSSL application that can lead to the loss of critical sensitive information. The vulnerability is called Heartbleed because if affects the TLS heartbeat function in secure, connections. Because OpenSSL is used by so many web applications, and because this vulnerability can be exploited, the severity is very high.