What is MySQL Encryption for Data-at-Rest?
MySQL Enterprise encryption for data-at-rest enables the encryption of tablespaces with transparent data encryption (TDE). It is relatively easy to set up and with the use of a compliant key management server (KMS)—secure.
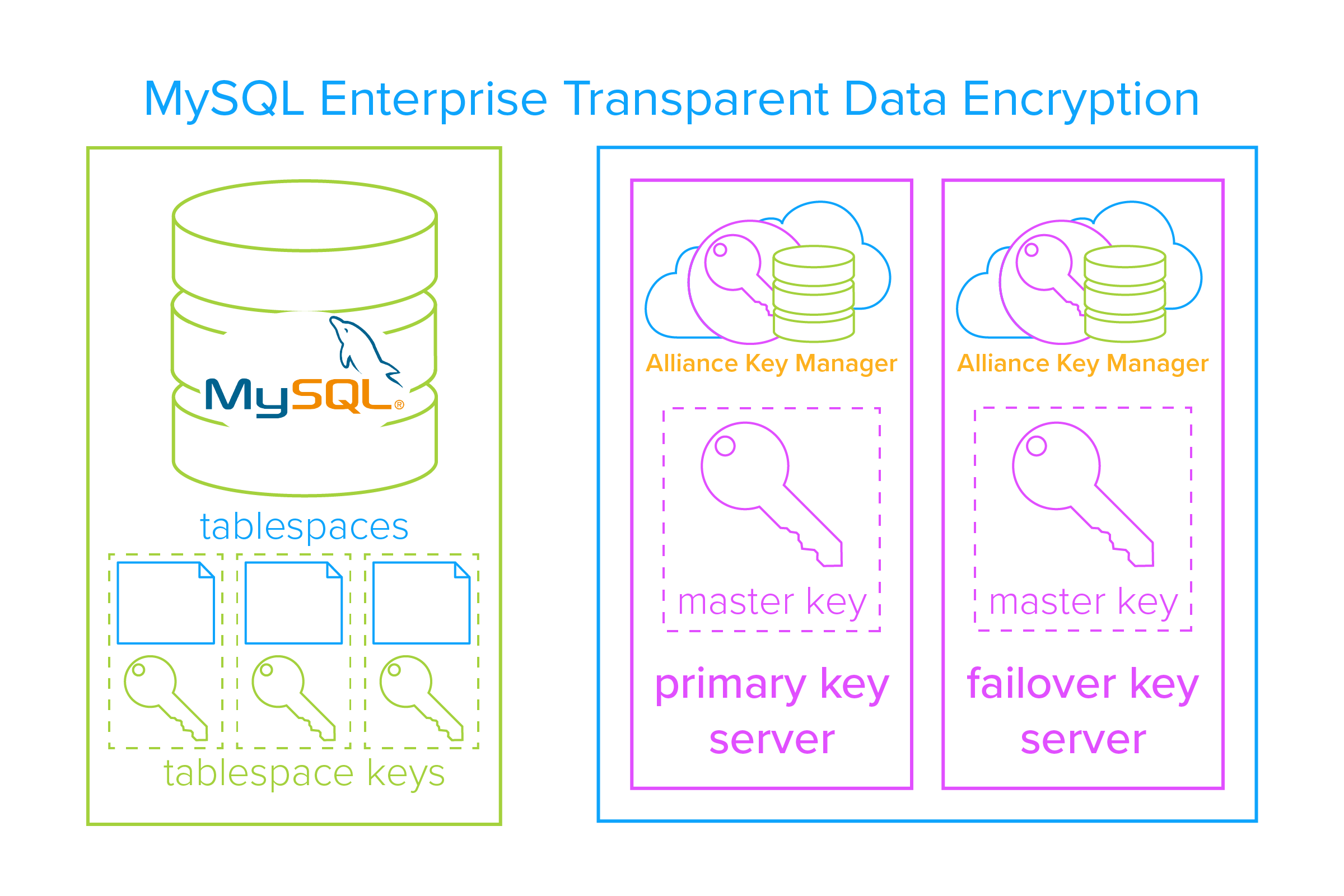
InnoDB, MySQL’s storage engine, offers transparent data encryption (TDE) for your sensitive data-at-rest. It secures the tablespaces via a “two tier encryption key architecture” that consists of:
- Tablespace encryption keys that encrypt the tablespaces.
- A master encryption key that encrypts the tablespace keys.
 The only thing that you must add is a trusted, third-party encryption key manager. But more on that later.
The only thing that you must add is a trusted, third-party encryption key manager. But more on that later.
With these items in hand, the system works like this:
- A tablespace is encrypted, generating a tablespace encryption key.
- The tablespace key is encrypted via the master key.
- The encrypted tablespace key is stored locally in the tablespace header.
- The master key is stored in a trusted, third-party encryption key manager.
- The master key’s full lifecycle is managed via the encryption key manager.
In this way, when a user or application needs to access the encrypted data, they just need to authenticate that they are authorized to access the data. From there, InnoDB uses the master key to decrypt the tablespace key and tablespace key is used to decrypt the data. The end user never sees this process, it is transparent to them.
Advantages of Using MySQL Encryption
Meets Compliance Regulations
Organizations are under increasing pressure to comply with a patchwork of compliance regulations. The good news, MySQL Enterprise edition uses standards based AES encryption for data-at-rest and is also KMIP compatible, so centralized key managers can plug-in to properly manage the master keys. Here are a few compliance regulations that MySQL Enterprise encryption helps you comply with:
Payment Card Industry Data Security Standard (PCI DSS)
Nick Trenc, IT Security Architect at Coalfire Labs, had this to say about encryption and PCI DSS compliance:
One of the key components to the protection of cardholder data at any merchant location is the use of strong cryptography along with just-as-strong cryptographic key management procedures. PCI DSS Requirement 3 outlines what the PCI council believes to be the baseline for strong cryptographic key management procedures and is a key element of any PCI DSS audit.
General Data Protection Regulation (GDPR)
According to GDPR, your security controls must be adequate to account for the risk of accidental, unlawful, or unauthorized disclosure or loss of personal data. If you are not adequately prepared to fend off attacks from hackers or unscrupulous employees and prevent a data breach, you could face stiff fines and lawsuits. Only proper encryption and centralized key management will ensure that should an attack occur, the data will be useless to the attacker.
California Consumer Privacy Act (CCPA)
Here is what Patrick Townsend said about encryption and CCPA:
If you want to avoid the risk of direct or class action litigation related to data loss you should encrypt the sensitive data. Individual and class action litigation only applies to unencrypted sensitive data that is disclosed or lost, for whatever reason. The CCPA is clear on the need for encryption. If you lose unencrypted sensitive data this is direct evidence that you violated your duty to provide reasonable security procedures and practices to protect the sensitive information.
The good news: enabling MySQL Enterprise encryption, coupled with encryption key management, will help keep you in compliance with these regulations. If you are protecting cardholder data, consumer data, or just internal HR records, encrypting that data with MySQL’s TDE will help you meet compliance and keep that sensitive data safe.
Easy to Deploy
MySQL encryption is easy to configure. Entire databases can be encrypted with just a few command line edits. Here are some selected examples from MySQL’s Reference Manual:
- To enable encryption for a new file-per-table tablespace:
- mysql> CREATE TABLE t1 (c1 INT) ENCRYPTION='Y';
- To enable encryption for an existing file-per-table tablespace:
- mysql> ALTER TABLE t1 ENCRYPTION='Y';
- To disable encryption for file-per-table tablespace:
- mysql> ALTER TABLE t1 ENCRYPTION='N';
Alliance Key Manager also makes this process easy. Since we are fully integrated with MySQL Enterprise, the configuration process is pretty straight forward. Many times, you can be up and running in a matter of minutes.
KMIP Compatible
As MySQL Enterprise encryption is KMIP 1.1 compatible, you can easily deploy your prefered key manager to manage your encryption keys. This means you are able to use a FIPS 140-2 compliant encryption key manager, like our Alliance Key Manager.
How It Works
MySQL Enterprise has made protecting your sensitive data easy. What’s more, setting up Alliance Key Manager for MySQL is easy as well. Here’s how it works:
- First, install and set up the primary and failover Alliance Key Manager servers.
- Download the admin authentication certificates from the Alliance Key Manager server to create a secure TLS connection and perform authentication.
- Then, create a directory to store your KMIP config file and store certificates needed for the Alliance Key Manager admin / client connection.
- Next, you will need to specify your primary key server and high availability failover key server.
- Finally, create a master key in Alliance Key Manager and use that to encrypt your tablespace keys in MySQL.
That's it, you have successfully encrypted your MySQL Enterprise database and properly managed the keys! To learn how Alliance Key Manager can help you easily protect your sensitive data in MySQL.
Final Thoughts
Encrypting your sensitive data in with MySQL’s Enterprise encryption has these advantages:
- It’s standards based AES-256 encryption. This means that your data is secured with the encryption algorithm that NIST recommends.
- It’s KMIP compliant. Your encryption is only strong if your keys are secure. With a trusted third-party key manager protecting your master keys, your encryption will remain strong.
- The encryption is transparent to users and applications. No manual processes are needed to access the databases. The data is there, on demand, for all authorized users and applications.
If you haven’t taken advantage of MySQL encryption, now is the time. MySQL encryption makes it simple. Alliance Key Manager makes it secure. Talk to us today.



