 Some years ago, during an “in between” period of my life, I drove a taxi in Houston, Texas. It was one of those enriching life experiences (this means it left scars), and a recent security newsletter from Bruce Schneier had me thinking about it again.
Some years ago, during an “in between” period of my life, I drove a taxi in Houston, Texas. It was one of those enriching life experiences (this means it left scars), and a recent security newsletter from Bruce Schneier had me thinking about it again.
All of us drivers loved to take a customer to Gilley’s, a famous honky-tonk out in Pasadena. Gilley’s was a huge place with live country music, line dancing, a mechanical bull, a real rodeo arena, and lots of Texans (most with quite a few long necks behind them). It ran well into the early morning hours and was always busy. It was a good distance from downtown Houston or the Houston airport and a ride to or from Gilley’s was going to be a good fare and usually a good tip.
Here’s the security angle – Gilley’s could be a bit dangerous starting from about 10 or 11 at night. There was a whole lot of drinking going on (I know you will be surprised by that), and some roughneck or cowboy or soldier was going to take an unfortunate interest in someone else’s girlfriend. Or maybe someone liked the wrong football team. Or whatever – there was no shortage of things that could cause a fight. A shooting or brawl was not that uncommon at Gilley’s. Every driver I knew carried some type of “protection” under the seat. Mine was a short tire iron. But some carried serious heat. But you never wanted to be in a position of actually having to defend yourself – you were probably going to get some serious hurt on you.
Every night when you were driving taxi you had to make a decision about taking a late night run to Gilley’s. A lot of drivers just wouldn’t go out there after 11pm. Some drew the line at 1pm, or wouldn’t go out there when the place was closing. But if you’ve had a bad day, that run might help you get profitable before sunrise. So, you were always making a security assessment – how much risk were you willing to bear?
Now here is what I was thinking about: When I think of Pasadena, Texas, my impression is still tinged with that original experience. For all I know, Pasadena may have changed into a yuppie paradise with 5-star restaurants and day spas. I’ve seen other neighborhoods transform (good or bad) over time. South of Market in San Francisco now has a Whole Foods, and China Basin is definitely not as dangerous. So things change over time. And a person’s personal security posture will change, too, if there is adequate information about the neighborhood.
 Now let’s bring these chickens home to roost.
Now let’s bring these chickens home to roost.
Things have changed in the world of IT. We used to feel safe behind our firewalls and DLP systems and anti-virus software. We carefully avoided upgrading our operating systems and software to avoid buggy releases. This made complete sense at the time.
But now the attacks come in from infected PDF files and infected web sites. A USB thumb drive can carry the danger. Systems that we thought were relatively safe like Macs, mobile phones, or IBM Mainframes and AS/400s now are as much of a threat as anything outside the firewall. Criminals now routinely use weaknesses in unpatched systems to steal sensitive data. The threat landscape has changed. We need to change, too.
So, when you think about that OS or software upgrade you should give more weight to staying current, and perhaps a little less weight to avoiding some bugs. I know the risks of doing software upgrades, and that you have to make a judgment call. But out of date software is honey to the bad guys. It’s time to re-think the security posture - the neighborhood is not the same.
Patrick
No, I’m not from Texas (Hat tip to Lyle Lovett)
Learn how we have made encryption and key management easier and more affordable than ever with Alliance Key Manager.

 The last few days has seen a number of new reports about a security vulnerability in RSA public/private keys in use on the Internet. The vulnerability has to do with duplicate keys, and not with any weakness in the cryptographic algorithm itself. But it is disturbing information because public/private key encryption is crucial to the security of web sites and a number of other secure applications and services.
The last few days has seen a number of new reports about a security vulnerability in RSA public/private keys in use on the Internet. The vulnerability has to do with duplicate keys, and not with any weakness in the cryptographic algorithm itself. But it is disturbing information because public/private key encryption is crucial to the security of web sites and a number of other secure applications and services. NIST also has a certification program for random number generators and vendors like us can submit our work to independent labs that perform NIST testing. All of our cryptographic solutions have been through this testing. It is also important to note that encryption key management systems that undergo FIPS 140-2 certification also go through full RNG testing. Our
NIST also has a certification program for random number generators and vendors like us can submit our work to independent labs that perform NIST testing. All of our cryptographic solutions have been through this testing. It is also important to note that encryption key management systems that undergo FIPS 140-2 certification also go through full RNG testing. Our 
 I’ve been writing about encryption performance lately because our customers and potential customers have been asking about the impact of encryption on the overall performance on their systems. It’s good that they are asking these questions as a poorly performing encryption library can have severe impact on your application environment. This is especially true on an IBM Enterprise platform like the IBM i (formerly known as AS/400 and iSeries) where customers often run multiple applications.
I’ve been writing about encryption performance lately because our customers and potential customers have been asking about the impact of encryption on the overall performance on their systems. It’s good that they are asking these questions as a poorly performing encryption library can have severe impact on your application environment. This is especially true on an IBM Enterprise platform like the IBM i (formerly known as AS/400 and iSeries) where customers often run multiple applications.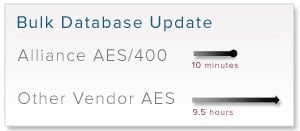 We did a simple little comparison test of encrypting 1 million credit card numbers on an entry level IBM i model 515 server with a single processor. We compared the native IBM AES library with our own AES encryption library which is NIST certified and optimized for encryption. The difference is very large. Our IBM i encryption library clocked in at 116 times faster than the native IBM i library. Note that this is an informal test and not independently verified, but practical experience by our customers is very similar.
We did a simple little comparison test of encrypting 1 million credit card numbers on an entry level IBM i model 515 server with a single processor. We compared the native IBM AES library with our own AES encryption library which is NIST certified and optimized for encryption. The difference is very large. Our IBM i encryption library clocked in at 116 times faster than the native IBM i library. Note that this is an informal test and not independently verified, but practical experience by our customers is very similar.
 Before you deploy an
Before you deploy an 



 Townsend Security hosts a monthly webinar on a wide variety of topics ranging from
Townsend Security hosts a monthly webinar on a wide variety of topics ranging from 