Do you know which of these 3 key regulations apply to you and your company?
 Secure system logging on your IBM i (AS/400) can do more than help you meet compliance requirements, it can also help you stop a data breach before it happens! We will take a quick look at three of the major regulations; PCI DSS, GLBA/FFIEC, HIPAA/HITECH, (keep in mind, there may be other compliance regulations that apply to system logging in your industry as well).
Secure system logging on your IBM i (AS/400) can do more than help you meet compliance requirements, it can also help you stop a data breach before it happens! We will take a quick look at three of the major regulations; PCI DSS, GLBA/FFIEC, HIPAA/HITECH, (keep in mind, there may be other compliance regulations that apply to system logging in your industry as well).
All regulations say about the same thing … you should be collecting system logs, you should be monitoring them, and you should take action based on anomalies that you find in them. It is not enough to assert that you are doing the right thing; you have to be able to prove it with system logs that are independent from the original system files, tamper resistant, and verifiable.
PCI DSS
Section 10 requires logging for anyone who collects credit card data
Requirement 10: “Track and monitor all access to network resources and cardholder data”- 10.1 Establish a process for linking all access to system components (especially access done with administrative privileges such as root) to each individual user.
- 10.2 Implement automated audit trails for all system components to reconstruct the following events:
- 10.3 Record at least the following audit trail entries for all system components for each event:
- 10.4 Using time-synchronization technology, synchronize all critical system clocks and times
- 10.5 Secure audit trails so they cannot be altered.
- 10.6 Review logs for all system components at least daily.
- 10.6.x v3 (Nov 2013) noted this clarification: Clarified the intent of log reviews is to identify anomalies or suspicious activity, and provided more guidance about scope of daily log reviews. Also allowed more flexibility for review of security events and critical system logs daily and other logs events periodically, as defined by the entity’s risk management strategy.
- 10.7 Retain audit trail history for at least one year, with a minimum of three months immediately available for analysis.
GLBA / FFIEC
Recommends data security logs of actions that could affect financial reporting or fraud for financial institutions
- Network and host activities typically are recorded on the host and sent across the network to a central logging facility.
- The logging facility may process the logging data into a common format. That process is called normalization. Normalized data frequently enables timely and effective log analysis.
FFIEC Action Summary
Financial institutions should gain assurance of the adequacy of their risk mitigation strategy and implementation by:
- Monitoring network and host activity to identify policy violations and anomalous behavior
- Monitoring host and network condition to identify unauthorized configuration and other conditions which increase the risk of intrusion or other security events
- Analyzing the results of monitoring to accurately and quickly identify, classify, escalate, report, and guide responses to security events
- Responding to intrusions and other security events and weaknesses to appropriately mitigate the risk to the institution and its customers, and to restore the institution's systems
HIPAA / HITECH ACT
Requires system logs of access to Protected Health Information (PHI) in the medical sector
- Security Management Process - §164.308(a)(1)(ii)(D):
- Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports. - LOG-IN MONITORING (A) - § 164.308(a)(5)(ii)(.c)
…the covered entity must implement: “Procedures for monitoring log-in attempts and reporting discrepancies.” - Access Controls - § 164.312(b)
(section b) Standard: Audit controls. Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic PHI.
System logging is important across all operating systems, however the IBM i is a major target for data theft because of the volume of information that can be managed in the system. Because the IBM i system can handle multiple applications, it doesn’t log information like others do. The IBM i collects logs simultaneously from multiple sources and may deal with large volumes: Up to 3,500 events per second…250 Million of events per day! These events need to be consolidated and correlated in a separate location, usually a Security Information and Event Management (SIEM) console, in order to see the whole picture and understand potential attacks on the system.
Because many unwanted intrusions start with a simple password hack that gives deeper access into your system, there is usually a long trail visible within system logs. What really is driving the need to collect and monitor system logs centers around how often breaches are easily detected with log management (forensics show 69% of breaches were detectable via log evidence). Everything, starting from the original breach, can be detected and identified with proper monitoring of the system logs.
To delve deeper into system logging, we are sharing a resource kit of materials by industry expert Patrick Townsend about logging on the IBM i today and how the capabilities of Alliance LogAgent can provide you with a high performance, affordable solution that will communicate system logs securely between the IBM i and SIEM Console.
Alliance LogAgent from Townsend Security
- Creates real-time logs that ALL SIEM consoles can read
- Forwards important information to your SIEM console in a standard format
- Uses SSL/TLS encryption to secure delivery





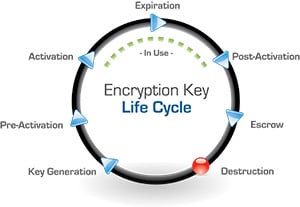
 and the data security requirements that affect Drupal developers or users. When dealing with the healthcare industry, Personally Identifiable Information (PII) is a subset of PHI, and refers to information that is uniquely identifying to a specific individual. Protected Health Information is specific to medical and health-related use and generally refers to demographic information, medical history, test and laboratory results, insurance information and other data that is collected by a healthcare professional to identify an individual and determine appropriate care. To better understand the recent changes in HIPAA/HITECH regulations, here are a few key rules that provide guidance:
and the data security requirements that affect Drupal developers or users. When dealing with the healthcare industry, Personally Identifiable Information (PII) is a subset of PHI, and refers to information that is uniquely identifying to a specific individual. Protected Health Information is specific to medical and health-related use and generally refers to demographic information, medical history, test and laboratory results, insurance information and other data that is collected by a healthcare professional to identify an individual and determine appropriate care. To better understand the recent changes in HIPAA/HITECH regulations, here are a few key rules that provide guidance: