Data protection is only as secure as you make it!
As more companies begin to move data to the cloud, protection of encryption keys become an even more important part of an overall data protection strategy. Three core information security components, becoming better known as the “CIA Triad”, are important elements in a solid data security policy. These core components in the triad are:

Confidentiality:
-
Confidentiality has to do with encrypting data in applications and databases, protecting it from people who should not be seeing that data or accessing it, whether that's in your IT data center or in a cloud environment or in virtualized applications.
Integrity:
-
You have integrity of the encryption key management process itself with connections to the key management HSM to authenticate and retrieve keys or perform on-device encryption operations. Integrity is accomplished through public key infrastructure (PKI) mechanisms.
Availability:
-
Availability is a crucial component especially with encryption key management systems which are mission critical applications. You need redundancy both at the hardware and software level with proper application mirroring and database mirroring in place. You should ensure backups take place at an appropriate interval and that recovery operations are also tested on a regular basis.
These components are achieved with a solid key management solution and the proper managing of the actual encryption keys. The Key Management administrator is responsible for performing a number of functions that must be done, and done properly to meet compliance regulations. The administrator must also follow industry best practices in order to accomplish true encryption key management for their organization and the data they need to protect.
The Encryption Key Life Cycle
One of the first functions the Key Management administrator performs is the actual creation and management of the encryption keys through a key lifecycle. The keys are generated and stored in a secure fashion and then go through the full cycle depicted here to become active, go into use, expire, retire (post-activation), and then be backed up in escrow, and then deleted (the “destruction” phase). 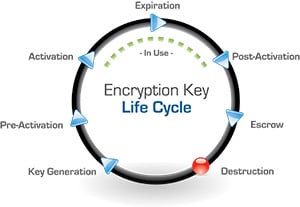 This lifecycle is defined by the National Institute of Standards and Technology (NIST) and also requires that a crypto period be defined for each key. A crypto period is the length of time that a key should be used and is determined by a number of factors based on how much data is being protected and how sensitive that data is. While NIST has defined and provided some parameters on how to establish crypto periods (see special publications 800-57 - there are 3 parts) and provided guidance on best practices. Each Key Management administrator needs to determine how long a particular encryption key should be actively used before it is rotated or retired.
This lifecycle is defined by the National Institute of Standards and Technology (NIST) and also requires that a crypto period be defined for each key. A crypto period is the length of time that a key should be used and is determined by a number of factors based on how much data is being protected and how sensitive that data is. While NIST has defined and provided some parameters on how to establish crypto periods (see special publications 800-57 - there are 3 parts) and provided guidance on best practices. Each Key Management administrator needs to determine how long a particular encryption key should be actively used before it is rotated or retired.
These are a few of the factors that go into establishing the crypto period for a key (which maybe a few days or weeks or longer up to one or two years it really depends on the data that you're trying to protect):
- How is the data being used
- How much data is there
- How sensitive is the data
- How much damage will be done when the data is exposed or the keys are lost
Auditing and Access Controls
Auditing and active monitoring of critical key management systems is a fundamental security concept for protecting critical assets like data in a key management solution. The Key Management administrator also needs to implement access controls to be sure that only the users and applications who should be accessing encryption keys are actually doing so. A general practice of separating encrypting keys across different departments or applications should be in place. For example, you may need to protect employee data in your HR system using an encryption key, but you wouldn’t want to use that same encryption key to protect sales data or where you might have credit cards. You need to segment the usage of encryption keys to particular data so that employees in HR are accessing HR data using one key and salespeople can access sales data using a different key.
For more information, security expert Patrick Townsend goes into greater depth in his latest podcast: Guidelines for Effective Encryption Key Management. He covers how implementing procedural mechanisms like dual control and separation of duties will help ensure your organization is implementing best security practices. Patrick also outlines fundamental components of a strong defense-in-depth approach to data security and how encryption and key management can protect your enterprise. I encourage you to download the 20 minute podcast!

