 We’ve had an upsurge in interest recently in our Alliance LogAgent solution for the IBM i (AS/400) platform. This solution sends security events from the IBM i in real time to log collection servers and SIEM solutions. As I’ve talked to IBM i customers, I am beginning to appreciate how difficult it is to get IBM i security information into a usable format so that events can be collected and monitored. The challenges are big:
We’ve had an upsurge in interest recently in our Alliance LogAgent solution for the IBM i (AS/400) platform. This solution sends security events from the IBM i in real time to log collection servers and SIEM solutions. As I’ve talked to IBM i customers, I am beginning to appreciate how difficult it is to get IBM i security information into a usable format so that events can be collected and monitored. The challenges are big:
- Data format – IBM security events are in internal IBM format, not syslog format.
- Multiple sources – Security events get collected in a variety of locations, almost always in an internal and proprietary IBM format.
- Timeliness – Tools are lacking to collect security events in real-time, increasing the security exposure.
- Communications – There are no native syslog UDP, TCP or SSL TCP communications facilities.
- Data completeness – While it is possible to print security information using IBM tools, critical information is missing from reports.
Here is a really good example of this last point. I can use the Display Audit Journal Entry command (DSPAUDJRNE) to print a report of user ID and password failures. Here is a bit of what that report looks like:
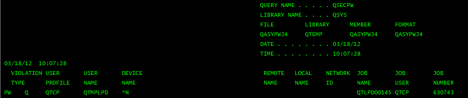
Can you imagine a SIEM solution or poor network administrator trying to get useful information from this? Fields are not easily identified and extracted, and most SIEM query tools would have a really hard time extracting the meaning from this report. There are user ID and password failures here, but hard to parse them out.
And one of the most important pieces of information is missing. Can you see what it is?
Right, the IP address of the originator of the error. SIEM solutions are good at correlating events if they know where they are coming from. The IP address is critical for accomplishing this. This report could probably tell you when you are under attack, but not where it is coming from and certainly not in real-time.
Our Alliance LogAgent solution solves all of these problems. Events are extracted from all of the relevant sources, in real time, converted to standard syslog format, and communicated using your choice of UDP, TCP, or secure TLS communications to your log server. And, Yes, the IP address is in the event! Here is an example of a PW event as it is processed by Alliance LogAgent:
<118>Sep 20 15:47:11 S10125BA QAUDJRN:[PW@0 event="PW-Invalid user or password" event_type="Q-Signon failed profile disabled" user_profile="QTCP" device="*N" jrn_seq="002273092" timestamp="20120120154711021000" job_name="QTLPD00145" user_name="QTCP" job_number="630743" ip_addr="10.0.1.205" port="15427"]
This is caviar to your SIEM solution! Real time alerts, event queries, and forensics become a snap when you get the right data into your SIEM solution. And real time system monitoring is one of the top recommendations by security professionals to keep your IBM i (AS/400) safe.
I’m proud of our system logging solution for the IBM platform. Our customers have deployed the solution in under an hour starting from the time they do the download from our web site.
Patrick

 In our final installment on system logging on the IBM i series, Patrick Townsend, Founder & CTO, discusses what to look for when selecting and deploying a logging solution. As we found out in
In our final installment on system logging on the IBM i series, Patrick Townsend, Founder & CTO, discusses what to look for when selecting and deploying a logging solution. As we found out in 
 System logging is also important for meeting compliance regulations too, right?
System logging is also important for meeting compliance regulations too, right? 
 As a company that works hard to protect your data, we get a lot of questions – from people wanting to know the ins and outs of our products to IT professionals who are new to the world of meeting compliance regulations. Luckily, our company has several experts to answer these questions. One topic that we often get questions regarding is system logging on the IBM i (AS/400). Logging on the IBM i is different than logging on other platforms. I recently sat down with Patrick Townsend, Founder & CEO, to pick his brain on what system logging is, and why it is so unique on the IBM i.
As a company that works hard to protect your data, we get a lot of questions – from people wanting to know the ins and outs of our products to IT professionals who are new to the world of meeting compliance regulations. Luckily, our company has several experts to answer these questions. One topic that we often get questions regarding is system logging on the IBM i (AS/400). Logging on the IBM i is different than logging on other platforms. I recently sat down with Patrick Townsend, Founder & CEO, to pick his brain on what system logging is, and why it is so unique on the IBM i.