This last November (Nov. 6-8, 2019) we had a chance to participate in the 21st annual PASS Summit in Seattle as an exhibitor. It was a great time as SQL Server professionals from around the world attended. We had an opportunity to ask them about their company's encryption and key management practices. Below are the results as well as some expert weigh-in on the findings. Enjoy!
The SQL Server Encryption Survey—2019
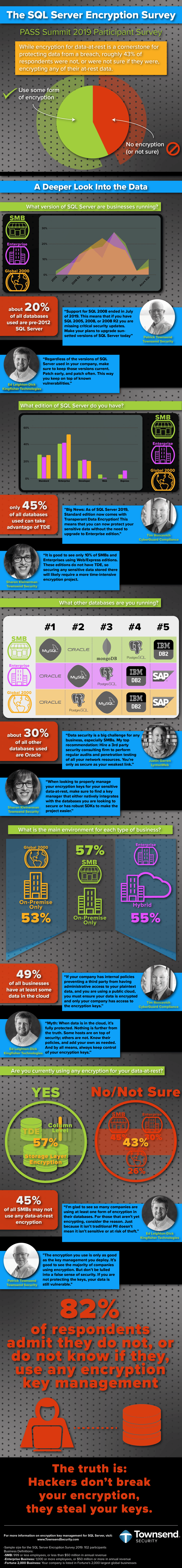
A special thanks to our contributors for their expertise and guidance. You all are clear-minded professionals that have a lot to offer those looking to better secure their data:
-Ed Leighton-Dick, Kingfisher Technologies
-Tim Roncevich, CyberGuard Compliance
-Justin Garren, LyntonWeb
-Sharon Kleinerman, Townsend Security
-Patrick Townsend, Townsend Security
If you are looking to protect your encryption keys for your sensitive data in SQL Server, you need a FIPS 140-2 compliant centralized key manager that:
- Never charges you additional fees for connecting a new end-point.
- Never limits the number of end-points based on the model of the KMS.
- Never limits the number of encryption keys generated or stored.
- Never forces you to pay extra fees for software patches.
- Never forces you to pay extra fees for routine software upgrades.
- Always gives you unmatched customer service.
- Always protects your keys, 24/7.
You need Alliance Key Manager for SQL Server.

