If you are an IBM i security administrator you know how hard it can be to determine a user’s true level of privilege on your system. IBM has given us a very flexible scheme to grant and restrict privileges to groups of users. And this flexibility can lead to unexpected security exposures. Let’s delve into this a bit deeper with an example (names are made up for this example):
JANICE
Janice is regional manager in the sales team. She’s exceptionally effective at her job and has taken on a number of tasks that help her support her team and the sales goals of her region. Let’s take a look at her user profile:
| User Profile . . . . . . . . . . . . . . . . . . . : | JANICE |
| Special authority . . . . . . . . . . . . . . . : | *SPLCTL |
| Group profile . . . . . . . . . . . . . . . . . . : | SALES |
| Supplemental groups . . . . . . . . . . . : | HRUSER PAYROLL REPORTING |
| INVENTORY MANAGERS … |
 At first glance it would seem that Janice has a normal user level of special authorities. In fact the only special authority is spool file control (*SPLCTL) which would be reasonable for a manager who needs to run and print reports. It also seems appropriate that Janice has a Group Profile of SALES. You would imagine that this probably gives her the ability to access the company sales management application.
At first glance it would seem that Janice has a normal user level of special authorities. In fact the only special authority is spool file control (*SPLCTL) which would be reasonable for a manager who needs to run and print reports. It also seems appropriate that Janice has a Group Profile of SALES. You would imagine that this probably gives her the ability to access the company sales management application.
The first hint of concern is the long list of supplemental groups. If you’ve met effective managers like Janice it won’t surprise you that they have access to a number of applications. She probably has responsibility for approving time off for her department’s employees, and has responsibilities for reporting to management. But what privileges are hidden in that Group Profile and in those Supplemental Groups?
Let’s take a look.
SALES (Group profile)
When we display the SALES user profile we find these special authorities:
| User Profile . . . . . . . . . . . . . . . . . . . : | SALES |
| Special authority . . . . . . . . . . . . . . . : | *SPLCTL |
| *JOBCTL | |
| Group profile . . . . . . . . . . . . . . . . . . : | *NONE |
| Supplemental groups . . . . . . . . . . . : |
Janice already had authority to spool files, but notice the job control value of *JOBCTL. This means that Janice has now inherited additional authority to manage jobs. This is not a severe uplift in privileges, but it shows how privilege escalation works.
Now, what about those supplemental groups? Do we have to look at every one?
Yes we do. Let’s look at the HRUSER profile next
HRUSER (Supplemental Group)
When we display the HRUSER user profile we see these authorities:
| User Profile . . . . . . . . . . . . . . . . : | HRUSER |
| Special authority . . . . . . . . . . . . : | *SPLCTL |
| *JOBCTL | |
| *SECADM | |
| Group profile . . . . . . . . . . . . . . . : | *NONE |
| Supplemental groups . . . . . . . . : |
Wow, the HRUSER has the special authority of security administration (*SECADM). That’s a bit worrying. If we had to guess there is probably third party HR package requirement for this, or this authority was just granted out of convenience. But now Janice has much more authority.
Let’s continue our exploration of those supplemental group profiles:
PAYROLL (Supplemental Group)
Let’s take a look at the PAYROLL user profile:
| User Profile . . . . . . . . . . . . . . . . : | PAYROLL |
| Special authority . . . . . . . . . . . . : | *SPLCTL |
| *JOBCTL | |
| *ALLOBJ | |
| Group profile . . . . . . . . . . . . . . . . : | *NONE |
| Supplemental groups . . . . . . . . . : |
Whoops, the PAYROLL user has All Object authority (*ALLOBJ). Bingo! This is the mother load of privilege. A user with All Object authority basically has the keys to the kingdom. It is pretty much equivalent to being the QSECOFR security officer (“root” for you Linux nerds). Once you have All Object authority you can manage other user profiles, grant yourself additional authority, and basically access any data on the IBM i server.
If I am an attacker and I can steal Janice’s credentials for the IBM i server I now have all of the authority I need to infiltrate sensitive data.
Did you notice how much work it was to track down Janice’s true privilege level? As an IBM i security administrator you probably know how to fix this problem. You need to analyze the real need for the All Object authority and revoke it. But imagine that you managed a system with hundreds or thousands of users. And imagine if you needed to check this at least monthly in order to detect any changes since the last time you inspected your users? It would truly be impossible to keep up with this task, and as the security administrator you might have other things you need to do, right?
So, is there any hope?
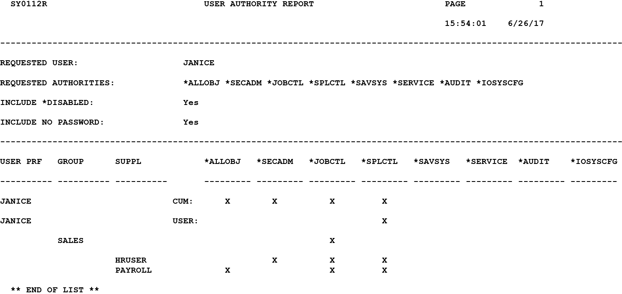
Sure there is. Our Alliance LogAgent solution will do this work for you. You can run the User Authorization report and Alliance LogAgent will track down these authorities for you. It will tell you the overall inherited authority of any (or all) users, and where they are getting the authority. Here is an example of the output for Janice:
Notice that all of Janice’s cumulative authorities are listed right on the top line of the report detail. Then notice that the Group Profile and all Supplemental Group profiles are listed with their authorities. The PAYROLL user is clearly identified as having the All Object authority. Now you can go to work.
The Alliance LogAgent report can be executed for all users, or for a group of users. And you can filter it so that you first get a list of all users who have inherited All Object authority. Then run it with additional authorities. In a few seconds you can find your privileged users, discover where they get that authority, and create a work plan to fix the problems.
However, Alliance LogAgent goes even further. As it is processing events from the security journal QAUDJRN, it can resolve in real time the true privilege of each user signing on to the IBM i server, tag job start events where the user has elevated privileges, and send them to your SIEM for monitoring. In real time.
I think that’s pretty powerful, don’t you?
Patrick