Encryption key management is the cornerstone of an effective encryption strategy. Without key management, encryption stands alone as only half of a solution. When you leave the keys to unlock your sensitive business and customer data exposed, then you expose your entire organization to the risk of data loss or theft. Luckily, MongoDB was born in the age of modern data security and developed their no-SQL database with the forethought and insight to incorporate strong encryption and key management solutions. This means that today, with MongoDB Enterprise, MongoDB customers can meet encryption and key management best practices fairly easily through implementing native encryption and deploying a third-party enterprise key management solution.
 In order to enable customers to seamlessly implement enterprise encryption key management, MongoDB integrated a universal encryption key management protocol called the Key Management Interoperability Protocol (KMIP). Unlike many other legacy databases who have floundered over the years trying to help customers do strong key management, MongoDB enables customers to protect encryption keys out of the door with a number of tested and validated enterprise key management partners. To know if you’re encryption key management solution is compatible with MongoDB, check to see that it has implemented KMIP.
In order to enable customers to seamlessly implement enterprise encryption key management, MongoDB integrated a universal encryption key management protocol called the Key Management Interoperability Protocol (KMIP). Unlike many other legacy databases who have floundered over the years trying to help customers do strong key management, MongoDB enables customers to protect encryption keys out of the door with a number of tested and validated enterprise key management partners. To know if you’re encryption key management solution is compatible with MongoDB, check to see that it has implemented KMIP.
What is Enterprise Encryption Key Management?
Enterprise encryption key management includes both technological and policy-based controls that integrate to provide the highest level of security of an organization’s encryption keys. Both types of controls are important to protecting encryption keys.
On a technological and physical level, encryption keys should be stored in a logically or physically separate hardware or virtual key server, dedicated to performing key generation, storage, and distribution. Keys should be generated with a FIPS 104-2 validated pseudo-random number generator and stored in a secure key database. Keys used for encrypting data (data encryption keys, or DEKs) should be key-wrapped and encrypted using key encryption keys (KEKs)--these keys are only used to encrypt DEKs inside the secure key database.
Once encryption keys are generated and in use, they should be distributed for use over a secure Transport Layer Security (TLS) session using certificates to authenticate the user requesting the encryption key. An enterprise key management server should use the most recent, recommended version TLS--1.2--as vulnerabilities were discovered in TLS 1.1 and TLS 1.0.
Lastly, enterprise key managers should perform real-time backup and high availability functions to prevent downtime and ensure business continuity. This means that each key server should perform active-active mirroring to one or more high availability server as well as perform routine, automated backups to secure storage drives.
All of these functions are critical to meeting best practices and securing encryption keys. However, beyond the technology, an enterprise key manager should implement user rules and administrative options that enforce particular policies and policy-based best practices.
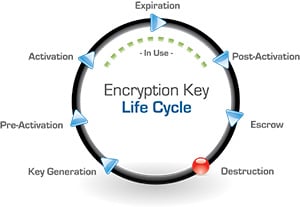 A critical administrative component to encryption key management is the ability to manage the complete encryption key life cycle. The encryption key lifecycle is defined by the National Institute of Standards and Technology (NIST), which outlines all aspects of a key’s life including key generation, pre-activation, activation, distribution, revocation, post-activation, backup, and deletion.
A critical administrative component to encryption key management is the ability to manage the complete encryption key life cycle. The encryption key lifecycle is defined by the National Institute of Standards and Technology (NIST), which outlines all aspects of a key’s life including key generation, pre-activation, activation, distribution, revocation, post-activation, backup, and deletion.
The administrative console that allows access to these functions should also give the IT or security administrator the option to designate key users or user groups as well as set keys to automatically rotate after a certain number of days, months, or years. This is just one requirement for organizations who fall under security standards for some regulated industries such as the payment card industry. The Payment Card Industry Data Security Standard (PCI DSS) outlines key management requirements for card holders or processors that can typically only be met using an enterprise-level encryption key management solution.
To learn more about PCI-DSS and encryption key management, view this webinar.
Beyond managing the key lifecycle, an enterprise key manager should actively audit and log all activity and functions performed on the key management server and record these logs to an external event monitoring or logging server so that malicious activity can be detected in real time. Your key management solution should be compatible with common event monitoring solutions and export logs in standardized formats in real time.
Lastly, your key management solution should inherently enforce policy-based security functions that meet key management best practices such as separation of duties and dual control. Separation of duties ensures that no single person is in control of multiple key management procedures such as the client request and subsequent distribution of an encryption key. The person requesting the key and the person distributing the key should be two different people. Dual control prevents any key management process to be controlled by a single person; for example, two security administrators should be needed to authenticate access to the key server. While these policy-based controls are sometimes optional, they should always be available and easy to implement in your encryption key management solution.
MongoDB Likes Centralized Key Management
When MongoDB decided to implement KMIP, the decision was likely a deliberate strategy to help users to either leverage the enterprise key management solution they already have, or to use common key management solutions that are KMIP-compatible. The power of KMIP is that it enables users to truly achieve centralized key management. A historical problem surrounding key management was the difficulty of an organization to store and manage encryption keys across multiple platforms, operating systems, and often departments. By implementing KMIP, MongoDB continues to make implementing key management across an organization more and more easy and effective, and therefore more user-friendly, which is what MongoDB is best known for.
Without deploying a strong encryption key management solution, encryption of sensitive data on its own is considered ineffective. In the age of the cloud, deploying a key management solution alongside your data is equally important, and therefore having options for where you deploy it is an important factor in your key management strategy. An effective key management solution should not only be centralized across your organization, but it should meet your data where it’s at, whether that is the cloud, a virtual environment, or on-site hardware.
KMIP also enables MongoDB customers to choose their own KMIP compliant key management solution and maintain complete custody of the key management server, and therefore the keys. Whether deploying the key manager in the cloud, in a virtual environment, or on-site, owning a third-party KMIP compliant key manager allows users to retain total control of their keys without sharing access with cloud service provides or software vendors.
Lastly, when researching professional or enterprise key management solutions, check to see if the vendor has validated their solutions with NIST such as to the NIST FIPS 140-2 standard, uses standardized technology, and has been validated to meet PCI DSS or other regulatory certifications. These validations ensure that the technology has been tested by independent labs to the highest security standards.
In combination with a robust database encryption solution from MongoDB, your encryption key management solution will elevate your security position and total level of control.

