Make sure you don't turn a blind eye to data security!
The basic concept of converting sensitive data into a form that could not be easily understood if it was to be seen by the wrong audience goes back as far as 500 BC (Atbash Cipher), some would even argue that in 1900 BC a simple hieroglyphic substitution was the first form of cryptography. 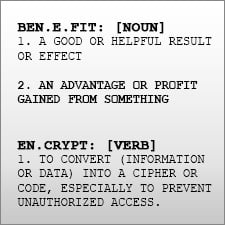 While technology has made great advancements in recent years, it has also created an even greater need for privacy of sensitive information. Whether you are the Chief Security Officer, IT personnel, or database administrator; you should know how your company is handling sensitive data. In fact, security is the responsibility of every business owner and employee. Not using secure passwords can lead to a data breach just as not following key management best practices can provide access to people with malicious intent. When awareness around data security reaches every department and individual, then the company can not only meet compliance regulations, but can benefit from effective data security. Compliance regulations require (or strongly recommend) all industries following best practices for encryption and key management . Do you know which of these apply to you and your company? For example, if you take credit cards for any reason, you fall under Payment Card Industry - Data Security Standards (PCI-DSS). Other common regulations are:
While technology has made great advancements in recent years, it has also created an even greater need for privacy of sensitive information. Whether you are the Chief Security Officer, IT personnel, or database administrator; you should know how your company is handling sensitive data. In fact, security is the responsibility of every business owner and employee. Not using secure passwords can lead to a data breach just as not following key management best practices can provide access to people with malicious intent. When awareness around data security reaches every department and individual, then the company can not only meet compliance regulations, but can benefit from effective data security. Compliance regulations require (or strongly recommend) all industries following best practices for encryption and key management . Do you know which of these apply to you and your company? For example, if you take credit cards for any reason, you fall under Payment Card Industry - Data Security Standards (PCI-DSS). Other common regulations are:
- HIPAA/HITECH ACT requires security of Protected Health Information (PHI) in the medical sector.
- GLBA/FFIEC sets regulations for banks, credit unions, credit reporting agencies, and anyone in the financial industry.
- FISMA is for Federal US Government Agencies.
- The Federal Trade Commission (FTC) also gets involved with anyone who issues a privacy statement.
- More than 45 states also have their own privacy rules, in addition to the ones listed above, that strongly recommend encryption of any personally identifiable information (PII).
So, beyond compliance with regulations, why should you care about encryption… First of all, your customers, clients, and suppliers all expect you to protect their sensitive data. Effective encryption and key management can provide your company with a number of other benefits as well. Here are just a few basic benefits of effective encryption key management:
- Peace of Mind - While hackers and identity thieves are getting smarter and regulations are getting more complex, data protection technology is also improving at a rapid rate. Encryption and key management options are now available in virtual machines and cloud environments as well as hardware security modules(HSMs). How well would you sleep at night if you kept your house key under your welcome mat?
- Reputation - Whether information is lost due to a hacker or a hurricane, if a company loses all of it’s important data, the whole business could be ruined. However if sensitive data is lost because mechanisms for protecting it are not in place, then an organization has even bigger problems. The most effective way to secure data and ensure the integrity of a company is to deploy encryption and properly manage the encryption keys.
- Credibility - Beyond audit requirements, organizations need to consider the security of their customers Personally Identifiable Information (PII). Being able to protect your clients with strong key management practices can add a level of trust and confidence that will help grow your business.
Mobility is also great benefit! As more people move their data to the cloud or virtualized environments the need for encryption increases, and the importance of key management becomes even more evident. In order to maintain control over your data, and the privacy of your customers, information must not only be encrypted but kept secure while in motion, in use, or at rest. By properly managing your encryption keys, you are still in control of your data no matter who is sharing your infrastructure.
In this complimentary eBook, "Turning a Blind Eye to Data Security”, authors Kevin Beaver, CISSP; Patrick Townsend, and Todd Ostrander will teach you about:
- Tools and resources to begin the discussion about data security in your company
- 5 Common misconceptions about data security
- 6 Questions to ask your CIO

